3.0 Logging In to Authentication Agent
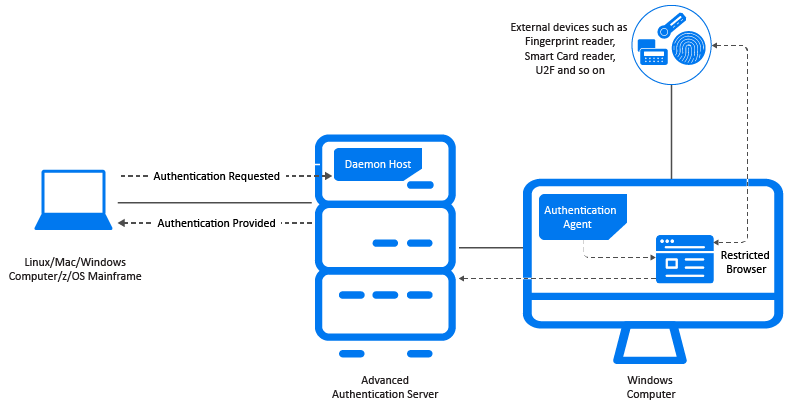
Authentication Agent enables you to perform multi-factor authentication on one computer to get authorized access to another computer, where it is not possible to display the user interface or connect any external authentication device. You can install the Authentication Agent on a workstation or a laptop. When an authentication is initiated from a computer using the Authentication Agent chain, the Authentication Agent on another computer prompts a restricted browser where you must perform the authentication.
The following diagram illustrates how the Authentication Agent works.
Scenario 1: Authenticating to Linux computer using the Authentication Agent
Mark uses the SSH to access Linux computer. But, the external devices such as FIDO U2F token and card reader are not supported in SSH. He cannot get authenticated to Linux computer because it is not possible to redirect the external devices. In this case, Mark can use Authentication Agent to perform authentication on Windows computer and get seamless access to Linux computer.
Consider the following setup:
-
Windows computer is installed with the Authentication Agent and is connected with the external devices such as FIDO U2F token and card reader.
-
Linux computer is where the Authentication Agent chain is enabled and is not connected with the external devices.
Following sequence describes the authentication process using Authentication Agent:
-
Specify user name and select the Authentication Agent chain in Linux computer.
-
Authentication Agent on Windows computer launches a restricted browser.
-
Select the preferred chain to log in to Linux computer in the restricted browser.
-
Perform the authentication using the FIDO U2F token and card reader in the restricted browser.
Mark is logged in to Linux computer automatically.
Scenario 2: Authenticating to Windows computer using the Authentication Agent
Thomas works on two Windows computers simultaneously. However, the external devices such as FIDO U2F token and card reader are connected to one Windows computer. He cannot get authenticated to the other computer because there are no external devices connected to this computer and cannot redirect the external devices. In this case, Thomas can use Authentication Agent to perform authentication on one Windows computer and get seamless access to another Windows computer that does not have external devices.
Consider the following setup:
-
Windows A is a computer with the Authentication Agent installed and is connected with the external devices such as FIDO U2F token and card reader.
-
Windows B is computer without the external devices and where the Authentication Agent chain is enabled.
The following sequence describes the authentication process using the Authentication Agent:
-
Specify user name and select the Authentication Agent chain in Windows B computer.
-
The Authentication Agent on Windows A computer launches a restricted browser.
-
Select the chain mapped to Windows log on in the restricted browser.
-
Perform the authentication using the FIDO U2F token and card reader in the restricted browser.
Thomas is logged in to Windows B computer automatically.
Logging In to Authentication Agent
You can log in to the Authentication Agent in one of the following ways:
Ensure that you have installed the Authentication Agent on a Windows workstation as a pre-requisite.
Single Sign-on Login
If Windows Client is installed along with the Authentication Agent and when you authenticate to Windows you are automatically logged in to the Authentication Agent. Else, when Windows is loading, you are prompted with an authentication request to log in manually. You must log in to authorize the Authentication Agent to receive any authentication request.
Manual Login
To log in to the Authentication Agent manually, perform the following steps:
-
Right-click on the Authentication Agent
 icon in the System Tray.
icon in the System Tray.
-
Select Log on.
-
Authenticate using the available chain in Windows.
Advanced Authentication provides the following authenticators for logging in to Authentication Agent: