7.1 Understanding the Trust Model
Setting up trust involves system administrators agreeing on how to establish a secure method for providing and consuming authentication assertions between their Identity Servers. An Identity Server is always installed as an identity provider, which is used to provide authentication to trusted service providers and Embedded Service Providers (ESPs). It can also be configured to be a service provider and trust the authentication of an identity provider.
7.1.1 Identity Providers and Consumers
An Identity Server can be configured as an identity provider, which allows other service providers to trust it for authentication. It can also be configured as a service provider, which enables the Identity Server to consume authentication assertions from trusted identity providers. Figure 7-1 depicts two Identity Servers. The Identity Server at the top of the figure is configured as an identity provider for SAML 1.1, SAML 2.0, and Liberty authentication. The Identity Server in the middle of the figure is configured as a service provider, consuming the authentication credentials of the top Identity Server. This second Identity Server is also configured as an identity provider, providing authentication for the Embedded Service Provider of the Access Gateway.
Figure 7-1 Identity Server Trust
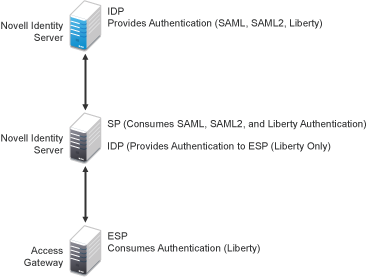
As an administrator, you determine whether your server is to be used as the identity provider or service provider in the trust relationship. You and the trusted partner agree to exchange identity provider metadata, and then you create references to the trusted partner’s identity provider or service provider in your Identity Server configuration. You can obtain metadata via a URL or an XML document, then enter it in the system when you create the reference.
7.1.2 Embedded Service Providers
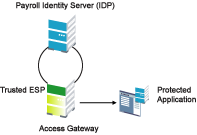
In addition to setting up trust with internal or external service providers, you can reference Embedded Service Providers (ESPs) in your enterprise. An ESP uses the Liberty protocol and does not require metadata entry, because this exchange happens automatically. The ESP comes with Access Manager and is embedded in the Access Gateways, the J2EE agents, and a version of the SSL VPN server. The ESP facilitates authentication between the Identity Server and the resource protected by the device, as shown in as shown in Figure 7-2.
Figure 7-2 Embedded Service Provider
7.1.3 Configuration Overview
The following high-level tasks describe the process required to set up the trust model between an identity provider and a service provider. Although these tasks assume that both providers are Identity Servers provided with Access Manager, similar tasks must be performed when one of the providers is a third-party application.
-
Administrators at each company install and configure the Identity Server.
See Section 1.1.1, Creating a Cluster Configuration. (You should already be familiar with the Novell Access Manager 3.1 SP4 Installation Guide.)
-
Administrators at each company must import the trusted root certificate of the other Identity Server into the NIDP trust store.
Click > > > > > , then auto import the certificate. Use the SSL port (8443) even if you haven’t set up the base URL of the Identity Server to use HTTPS.
-
Administrators must exchange Identity Server metadata with the trusted partner.
Metadata is generated by the Identity Server and can be obtained via a URL or an XML document, then entered in the system when you create the reference. This step is not applicable if you are referencing an ESP. When you reference an ESP, the system lists the installed ESPs for you to choose, and no metadata entry is required.
-
Create the reference to the trusted identity provider and the service provider.
This procedure associates the metadata with the new provider. See Section 7.3.1, Creating a Trusted Provider for Liberty or SAML 2.0.
-
Configure user authentication.
This procedure defines how your Identity Server interacts with the trusted provider during user authentication. Access Manager comes with default basic authentication settings already enabled. See Section 12.0, Configuring User Identification Methods for Federation.
Additional important steps for enabling authentication between trusted providers include:
-
Setting up the necessary authentication contracts. See Section 3.4, Configuring Authentication Contracts.
-
Enabling the profiles that you are using. See Section 14.2, Managing Web Services and Profiles.
-
Enabling the option on the Web Service Consumer page. See Section 14.5, Configuring the Web Service Consumer.
-
-
(Conditional) If you are setting up SAML 1.1 federation, the protocol does not allow the target link after federation to be automatically configured. You must manually configure this setting.
See Specifying the Intersite Transfer Service URL for the Login URL Option.
NOTE:For a tutorial that explains all the steps for setting up federation between two Novell Identity Servers, see Setting Up Federation
in the NetIQ Access Manager 3.1 SP5 Setup Guide.