1.2 Support for Standard Driver Features
The LDAP driver supports these standard driver features:
1.2.1 Local and Remote Platforms
You can install the LDAP driver locally or remotely.
An installation on the same computer where an Identity Vault and the Metadirectory engine are installed is referred to as a local configuration. The following figure illustrates a local configuration:
Figure 1-2 A Local Configuration
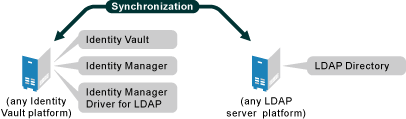
If platform or policy constraints make a local configuration difficult, you can install the LDAP driver on the server hosting the target LDAP server. This installation is referred to as a remote configuration and requires the use of the Remote Loader service.
Although a remote configuration is possible, it provides little additional flexibility because of the following:
-
The driver can run on any Identity Vault platform.
-
The driver communicates with the LDAP server on any platform across the wire via the LDAP protocol.
See Considerations and Prerequisites for Installation
in the NetIQ Identity Manager Setup Guide for information about the supported platforms for the Identity Manager server and Remote Loader.
1.2.2 Entitlements
The LDAP driver supports entitlements. However, an action such as provisioning an account in the target directory is delayed until the proper approvals have been made. In Role-Based Services, rights assignments are made based on attributes of a user object. Entitlements standardize a method of recording this information on objects in the Identity Vault. From the driver perspective, an entitlement grants or revokes the user’s right to objects in the target directory. You can use entitlements to grant the right to an account in the target directory and to control group membership. The User Application either grants or revokes entitlements for a user based upon administrator defined rules.
The LDAP driver uses Permission Collection and Reconciliation service to map entitlements to resources and automatically assign those entitlements to users when permissions change in the target directory. The driver updates the Resource Catalog so that it reflects the exact state of user permissions in the target directory. The driver content includes an enhanced entitlement package that contains the following entitlements, by default:
-
Account: This entitlement grants or denies an account in the target directory for the specified user. When this entitlement is granted, the driver provides an enabled logon account. When this entitlement is revoked, the driver either disables or deletes the logon account, depending on the driver configuration.
-
Group: This entitlement grants or denies membership to a group in the target directory. When the entitlement is revoked, Identity Manager removes the user from the group.
The LDAP driver also supports custom entitlements other than the default set provided, creating and automatically managing the relationship of identities to resource assignments. The driver uses a CSV file to map the target directory permissions into corresponding resources in the Resource Catalog. If an administrator then assigns a resource to a user in the User Application or in iManager, that change is reflected in the target directory and similarly, if the target directory administrator makes a change to the user permission, that change is reflected in the Identity Vault and the corresponding resource is updated with the permission assignment.
The following packages contain the content necessary for collecting and reconciling permission assignments in the target directory:
-
NOVLACOMSET 2.0.0 (Common Settings Advanced Edition)
-
NOVLLDAPENT 2.2.0 (LDAP Entitlements Support)
-
NOVLLDAPDCFG 2.1.0 (LDAP Default Configuration)
If you want the driver to support custom entitlement and use Permission Collection and Reconciliation service, ensure that these packages are installed on the driver. You can turn this functionality on or off using the new set of GCVs included with the driver.
You should enable entitlements for the driver only if you plan to use the User Application or Role-Based Entitlements with the driver. For more information about entitlements, see the NetIQ Identity Manager Entitlements Guide.
Prerequisites
Before continuing, ensure that you go through the prerequisites needed for enabling this functionality. For general prerequisites, see Prerequisites
in Synchronizing Permission Changes from the Connected Systems
in the NetIQ Identity Manager Driver Administration Guide. In addition to the general prerequisites, ensure that the LDAP driver version is 4.0.0.1.
Also, you need to set up administrative user accounts and configure a password policy for them. For more information, see Setting Up Administrative User Accounts
and Setting Up Administrative Passwords
in the NetIQ Identity Manager Driver Administration Guide.
To use the new functionality included in the LDAP driver, you can either create a new driver with the latest packages or upgrade packages on an existing driver. For more information about creating a driver, see Creating the Driver Object in Designer or Adding Packages to an Existing Driver.
CSV File Format
The LDAP driver can consume the entitlement information from the CSV file, which is present on the server where Identity Manager is installed.The CSV file must contain values of the target system permission information in the format specified below. The target directory administrator should maintain a separate CSV file for every custom entitlement. For example, a CSV file can contain details about issuing parking passes to the employees for the ParkingPass entitlement. A CSV file that holds ParkingPass entitlement details represents this information in the following format:
North, North Lot, North Parking Lot
where North is the entitlement value, North Lot is the display name in the User Application for the entitlement value North, and North Parking Lot is the description of the entitlement value, which is displayed in the User Application.
1.2.3 Password Synchronization
The LDAP driver supports password synchronization on the Subscriber channel, meaning that you can send passwords from the Identity Vault to any connected LDAP directory.
Password synchronization on the Publisher channel (LDAP directory to Identity Vault) is supported only with Sun Java System Directory Server Enterprise Edition version 6.3.x. For more information about installing the Identity Manager plug-ins for synchronizing passwords on the Subscriber channel, see Installing the Identity Manager Plug-Ins for Password Synchronization with Sun Java System Directory.