22.1 Planning Overview
This section provides valuable information for planning a PCRS implementation in your Identity Manager environment.
22.1.1 Prerequisites
Ensure that you meet the following requirements for implementing PCRS:
-
Designer for Identity Manager 4.0.2 AU4 and later
-
Identity Manager 4.0.2 with Engine Patch 4 and later
-
Managed System Gateway driver version 4.0.0.6 and later
-
Driver Set Package:
-
Common Settings Advanced Edition Package (NOVLACOMSET 2.0.0 and later)
-
-
Driver Package:
-
Driver-specific entitlements packages for Active Directory, LDAP, Delimited Text, and Loopback drivers
For example, use NOVLADENTEX for Active Directory driver, NOVLLDAPENT for LDAP driver, and NOVLDTXTENT for Delimited Text driver. For more information, see driver-specific implementation guides.
-
NOVLCOMPCRS 2.0.0 and later PCRS package
This is the common PCRS package for defining custom entitlements on drivers such as SOAP and JDBC.
-
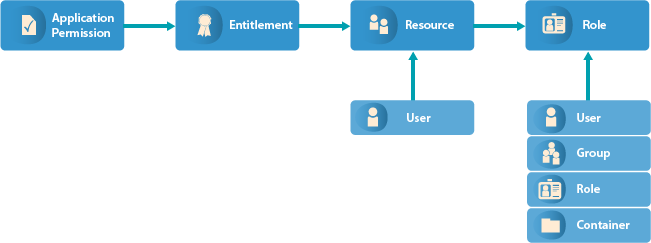
22.1.2 Understanding the Resource Model
In Identity Manager, a resource is any digital entity such as a user account, computer, or database that a business user needs to be able to access.
Resources are similar to entitlements and used in user provisioning. Technically, you can think of a resource as an additional abstraction layer between driver entitlements and roles. Identity Manager restricts that a resource be associated with only one entitlement. However, you can bind a resource to the same entitlement more than once, with different entitlement values for each resource.
Resources can be assigned to roles. There are three levels of roles provided in the roles-base provisioning model. A role can be made up of other roles, which in turn can be made of other roles. At the lowest level a role has a resources attached to it.
You can map resource assignments to users or to roles within your organization. For example, you can use resources to:
-
Make resource requests for users
-
Create resources and map them to entitlements
Identity Manager leverages its resource model for performing event-based reconciliation of external system permission assignments. The resource model simplifies the entitlement model and provides you a convenient way to perform resource-based provisioning actions. The resource-based provisioning actions allow you to manage resource definitions and resource assignments within your organization.
You can assign resources only to users. You cannot assign them to groups or containers. If a resource is mapped to a role, that role can be assigned to a group or container resulting in an assignment of mapped resource to all the users in that group or container.
Before you can assign resources to users, the resources must be defined in Identity Manager. Identity Manager stores resources in the Resource Catalog of the User Application. The Resource Catalog also stores the supporting data needed by the Role and Resource Subsystem, which is the underlying infrastructure for roles-based provisioning module. All the defined resources are displayed in the Resource Catalog. You can create new resources, and modify, delete, and assign the existing resources.
Identity Manager provides User Application for end users to request the resources they need. It also provides additional tools that administrators can use to define and manage resources such as Designer and Catalog Administrator.
22.1.3 Understanding the Components for PCRS
The following Identity Manager components help you reconcile the connected system permissions with the Resource Catalog of the User Application.
Common Settings Advanced Edition Package GCVs
The Common Settings Advanced Edition package includes the NOVLACOMSET-GCVs object, which contains two new GCVs used in permission assignment onboarding process.
-
User Application Provisioning Services URL GCV (UAProvURL)
-
User Application Provisioning Services Administrator GCV (UAProvAdmin)
The new entitlement packages create these GCVs which are used by the PermissionOnboarding job. For information about configuring the Common Settings GCVs, see Configuring Common Settings GCVs. For information about PermissionOnboarding job, see PermissionOnboarding Job Object.
Identity Manager Policy Objects
The Startup policies update the following mapping table objects:
-
PermissionNameToFile: Contains entitlement configuration data that you specified in the Entitlements Name to CSV File Mappings page when the driver was created in Designer. You can add custom entitlements to this table.
-
PermissionEntMapping: Created empty but is populated by the Startup policies and PermissionOnboarding job. It contains the configuration data transferred from the PermissionNameToFile object and DNs of entitlements created by the Startup policies. It also contains the LDAP DNs of the default dynamic User Application resource objects that are used to assign entitlements to users. You should not change the data populated by the Startup policies in this table.
-
StaticValueEntitlementMap: Created empty but contains mapping between specific native entitlement values and a User Application static resource DN used by the driver to reconcile that value. You need to populate this table if you want to synchronize assignments bound to a static resource.
You must manually enter the complete DN of the static resource in the Static Resource column.
IMPORTANT:Restart the driver for it to take effect of any changes made to the PermissionNameToFile and StaticValueEntitlementMap mapping table objects.
PermissionOnboarding Job Object
The driver policies update the PermissionOnboarding job parameters and the PermissionEntMapping mapping table.
The PermissionOnboarding job is a standard Identity Manager job and part of the entitlement package. The driver creates the job in the Identity Vault when the driver is deployed. The job runs when the driver starts. However, you can schedule the job to run periodically. Also, you can run it manually to process an updated CSV file. The NOVLCOMPCRS-ENT-startup-UpdateJobConfiguration Startup policies configure the PermissionOnboarding job.
The PermissionOnboarding job performs the following tasks:
-
Reads the driver's PermissionEntMapping table object to obtain the list of the driver's entitlement objects populated by the Startup policies.
-
Creates or verifies the existence of a dynamic nrfResource object to allow the assignment of the native permissions for each entitlement object in the PermissionEntMapping table. To do this, the job uses the Identity Manager provisioning, resource, and service SOAP APIs.
-
Updates the PermissionEntMapping table with the nrfResource DNs.
-
Reads the CSV file and populates the associated <name>_Values resource object with the values, display names, and descriptions for each entitlement object that specifies a CSV File catalog source in the PermissionEntMapping table.
-
Calls a User Application private API to flush the User Application Entitlement cache so that newly created entitlements are recognized.
-
Calls the User Application Entitlement refresh API to force the User Application to issue an entitlement query to obtain the catalog values for each driver entitlement.
Mapping Table Objects
When you install the entitlement package, the policies of this package are added to the driver Startup policy set. The driver executes these policies only once when the driver is started. The driver policies automatically configure the following objects for your environment:
-
Entitlement Objects: The driver creates new entitlement objects to represent the native entitlement names identified in the PermissionNameToFile mapping table. The name of entitlement is the value of the entitlementName column of the PermissionNameToFile mapping table. For more information about mapping table objects, see Mapping Table Objects.
-
Permission Value Resource Object: The driver adds a new permission value resource object, entitlementName_values. This object contains values for Entitlement Values, Description, and Display Name for every custom entitlement from the CSV file. It might also contain mappings for legacy value formats. To add more values to the entitlements, update the CSV file.
-
Entitlement Configuration Resource Object: The driver creates a new entitlement configuration resource object, EntitlementConfiguration.
Understanding the CSV File Format
An Identity Manager driver enabled with PCRS consumes the custom entitlement information from a CSV file created by the system administrator of a connected system. The system administrator maintains a separate CSV file for every custom entitlement. A CSV file must contain values of the connected system permissions in the below format that Identity Manager can consume.
|
Attribute |
Description |
|---|---|
|
entitlement value |
The custom entitlement value you want to add to the Resource Catalog. |
|
entitlement display name |
The custom entitlement name you want to display in the User Application. |
|
entitlement description |
The description for the new custom entitlement value. |
The values for entitlement display name and entitlement description are consumed by the User Application while assigning a resource to a user. These attributes can be viewed in the User Application. For example, a CSV file containing details about granting access to the employees for a BuildingAccess entitlement represents this information in the following format:
Building A, Engineering, The engineering building Building B, Accounting, The accounting building Building C, Facilities, The facilities building Building D, Warehouse, The warehouse
where Building A is the entitlement value, Engineering is the display name in the User Application for the entitlement value Building A, and The engineering building is the description for the entitlement value that appears in the User Application.
It is mandatory that the CSV file is placed on the Identity Manager server.