22.2 Preparing Your Environment
Your environment for PCRS must be configured appropriately. For example, the User Application must have new administrative user accounts that can be used by the policies to create and configure the configuration objects and job for quick onboarding of identity, resources, and permission assignments. This section helps you prepare your environment before you install a driver enabled with PCRS.
22.2.1 Setting Up Administrative User Accounts
To create and configure the configuration objects and job for quick onboarding of identity, resources, and permission assignments, the new policies use two administrative accounts: the Administrative user for the Identity Vault and a Resource Administrator for the User Application:
-
Identity Manager Driver Administrator: Set this administrative user in the driver’s Security Equivalence attribute when you deploy the driver. The policies use the user specified by the Security Equivalence attribute. This user needs the rights to create and modify the driver policy objects and to execute the PermissionOnboarding job, which is part of the driver package.
-
User Application Resource Administrator: This administrative user performs the following tasks:
-
Creates resource objects
-
Triggers cache flush and entitlement refresh actions
-
Assigns and revokes resource assignments
-
For the User Application Resource Administrator user, NetIQ recommends that you create a new user. For example, you can create the new user, cn=ResourceAdmin,OU=sa,O=data and configure the following rights for the user in the User Application:
-
Role, Resource Creation, and Assignment Rights: Click Administration > RBPM Provisioning and Security > Administrator Assignments > Assign System Role Administrator, select Domain and assign the following rights to the user:
-
Provisioning: Select All Permissions
-
Resource: Select All Permissions
-
Role: Select All Permissions
NOTE:You need to assign each set of Domain permissions separately for the user.
-
-
Application Cache Refresh Rights: In the User Application, click Administration > Application Configuration > User Application Administrator Assignment, then add the user to the Current Assignments list.
NOTE:This user account is also used to filter the duplicate entitlement events occurring on the Subscriber channel as a result of auto-reconciliation of resource assignments.
22.2.2 Setting Up Administrative Passwords
To simplify the configuration and security of Identity Manager drivers with PCRS, use Distribution Password for the Driver Administrator user and the User Application Resource Administrator administrative user. Identity Manager uses Distribution Password to control password synchronization between the Identity Vault and connected systems. Identity Manager reads passwords for these administrative users from their nspmDistributionPassword attribute.
When you create the new administrator accounts, you must assign a password policy to the new user accounts. Optionally, you can use the default Sample Password Policy and assign the policy to them. For more information, see Password Management Configuration
in the NetIQ Identity Manager - Administrator’s Guide to the Identity Applications.
22.2.3 Configuring Common Settings GCVs
The Common Settings Advanced Edition package contains the User Application Provisioning Administrator and User Application Provisioning URL GCVs. These GCVs are created by the new package supporting PCRS and used by the PermissionOnboarding job.
You must configure the GCVs on the driver set containing the drivers for quick onboarding of custom entitlements. Identity Manager recommends that you install and configure the GCVs before creating or configuring a new driver.
-
Start Designer and open your project.
-
In the Outline view, right-click Package Catalog and select Import Package.
-
Clear Show Base Packages Only.
-
Select the Common Settings Advanced Edition package and click OK, then click OK when Designer finishes importing the package.
-
In Modeler, right-click the driver set where you want to create your new drivers and select Properties.
-
Click Packages.
-
Click the Add package icon, select Common Settings Advanced Edition, then click OK.
-
Click OK.
-
(Conditional) Click OK to install any additional package dependencies.
-
In the Package Installation Wizard, specify the URL for your User Application installation and the DN of your User Application Administrator account, then click Next.
-
Click Finish.
Now you have all the information for creating custom entitlements. For creating custom entitlements, continue with Understanding the PCRS Process.
22.2.4 Configuring Custom Entitlements
You use Designer to configure custom entitlements on a driver enabled with PCRS. The entitlements packages contain the content necessary for collecting and reconciling permissions. If you want a driver to support permission collection and reconciliation, ensure that these packages are installed on the driver. You can turn this functionality on or off using the new set of GCVs included with the driver.
You can either create a new driver with the latest packages or upgrade the packages for an existing driver. In both cases, you install the driver packages and then modify the driver configuration to suit your environment. For creating new drivers, NetIQ recommends that you refer to the individual driver documentation guides.
Installing the Driver Packages
After you have imported the current driver packages into the Package Catalog, you can install the driver packages to create a new driver.
-
In Designer, open your project.
-
In the Modeler, right-click the driver set where you want to create the driver, then select New > Driver.
-
Follow the driver configuration wizard to create the driver.
-
On the Entitlements Name to CSV File Mappings page, click the Add Name to File Mapping
 icon to populate the page with the entitlement configuration options.
icon to populate the page with the entitlement configuration options.
Identity Manager uses the CSV file to map entitlements to corresponding resources in the Identity Manager catalog.
The information that you specify on this page is used for creating the permission catalog. This page uses BuildingAccess as an example. Fill in the following fields, then click Next:
-
Entitlement Name: Specify a descriptive name for the entitlement to map it to the CSV file that contains the connected system entitlement details.
Entitlement Name is the name of the entitlement. This parameter corresponds to the Entitlement Assignment Attribute in the connected system. For example, you could define an entitlement called BuildingAccess.
This parameter is used to create a resource in the User Application.
-
Entitlement Assignment Attribute: Specify a descriptive name for the assignment attribute for an entitlement.
This parameter holds the entitlement values from the connected system. For the engine to receive the attribute events from the Publisher channel, ensure that you add this parameter to the Driver Filter. For example, you could have an attribute called BuildingAccess.
NOTE:For the Delimited Text Driver, add this parameter in the Field Names on the Driver Parameters page or modify it in driver settings after creating the driver.
-
CSV File: Specify the location of the CSV file. This file must be located on the same server as the Identity Manager engine. This file contains the values for the application entitlements in the format value, displayname, and description. An example for the CSV file path is /root/user/BuildingAccess.csv. For more information, see Understanding the CSV File Format.
-
Multi-valued?: Set the value of this parameter to True if you want to assign resources and entitlements multiple times with different values to the same user. Otherwise, set it to False.
NOTE: In case you changed the value of this parameter after the driver starts, delete the associated entitlement object and the resource, and then restart the driver.
-
-
Review the summary of tasks that will be completed to create the driver, then click Finish.
The driver is now created. Deploy the driver to the Identity Vault.
22.2.5 Understanding the PCRS Process
After a driver with custom entitlements is created or configured in Designer, you must deploy it into the Identity Vault. When the driver is started, the driver automatically creates new resources based on the entitlements configured and populates the resource with the entitlement values from the CSV file. The new custom entitlement and the corresponding resource object is updated in the PermissionEntMapping table. When a permission assignment changes in the connected system, the driver policies consume the modified permission value and update the Resource Catalog. The following sections provide information about the sequence of actions involved in this process.
Sequence of Actions
-
When the driver is started, the following actions occur:
-
Identity Manager executes the driver start up policies.
-
The InitEntitlementConfigurationResource policies perform the following actions:
-
Reads the permissionnametofile mapping table to retrieve the entitlement information from this mapping table and creates these entitlements in the Identity Vault if they are not already existing.
-
Updates the PermissionEntMapping object with the entitlement information and the location of the CSV file.
-
Updates the entitlement configuration resource object with the entitlement information. RBPM uses this object for refreshing the code map.
-
-
The SetJobNamedPassword and UpdateJobConfiguration policies configure the permission onboarding job with the required permissions.
-
The OnboardEntitlements policy starts the PermissionOnboarding job.
When the job is started, it performs the following actions:
-
Reads the CSV file containing the entitlement values.
-
Populates the <entitlementname>_Values objects in the Identity Vault. For example, for a custom entitlement named BuildingAccess, it creates a DirXML-Resource object in eDirectory with name BuildingAccess_values containing the values of the custom entitlement.
-
Creates a dynamic resource for assigning new custom entitlement values to the users.
-
Populates the PermissionEntMapping object with the newly created resource name.
-
Issues a code map refresh to update the Resource Catalog with the new entitlement values.
At the end of this step, verify that the following tasks are completed:
-
Custom entitlements are created in the Identity Vault.
-
The EntitlementConfiguration resource object is updated in the Identity Vault.
-
<entitlementname>_Values object is updated for each entitlement in the Identity Vault.
-
Resources are created in RBPM.
-
The PermissionEntMapping object is updated in the Identity Vault.
Now the driver is ready to synchronize the connected system permission changes to the User Application.
For more information, see Viewing Permission Collection and Reconciliation Service Configuration Objects.
-
-
How Permissions Are Reconciled
The below examples will help you understand how permissions are reconciled in different scenarios.
Use Case 1: When the Publisher channel has an event with permission changes.
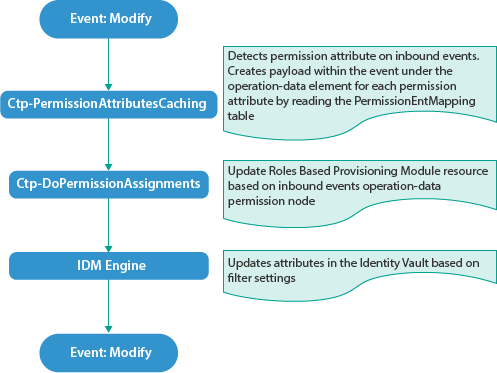
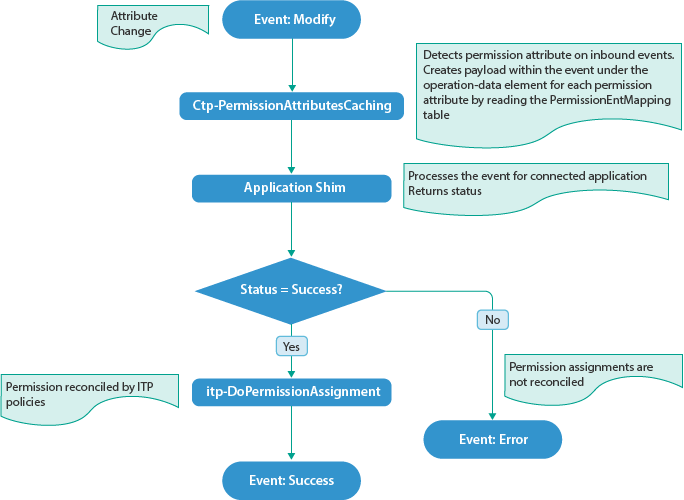
Use Case 2: When a permission attribute changes in the Identity Vault.
In this case, Identity Manager sends a Subscriber event to update the changed permission in the connected system. Also, the permission is reconciled in Resource Catalog.

Use Case 3: When a permission changes in Resource Catalog.
This action causes a Subscriber event to update the permission in the connected system.
IMPORTANT:You can create a new resource and map it to a custom entitlement and reconcile permission assignments. However, if PCRS is turned off, all resource assignments for the custom entitlement are disabled regardless of whether the resource is created through PCRS or not. Identity Manager does not support using the common package included with PCRS on a driver that already supports entitlements