9.25 Smartphone
Advanced Authentication provides the Smartphone method that facilitates users to authenticate through their Smartphone. The authentication happens through the NetIQ smartphone app to perform the out-of-band authentication. The out-of-band authentication is typically a two-factor authentication that requires a secondary verification through a separate communication channel along with the ID and password.
The authentication flow for the Smartphone method in Advanced Authentication is described in the following image.
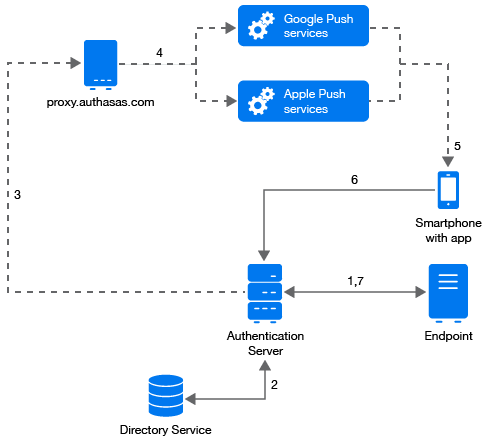
A user wants to authenticate on an endpoint such as a laptop or a website with the Smartphone method. The following steps describe the authentication flow:
-
When the authentication request is initiated, the endpoint contacts the Advanced Authentication server.
-
The Advanced Authentication server validates the user’s credentials.
-
After validating the credentials, the Advanced Authentication server sends a push message to proxy.authasas.com.
-
Depending on the platform of the Smartphone, the server selects an appropriate push service and then forwards the push message to the Smartphone.
-
The push message is then delivered to the user’s Smartphone to inform that an authentication request has been initiated.
-
When the user opens the Smartphone app, the app reaches the Advanced Authentication server to validate if there is an authentication needed. The authentication is indicated by the Accept and Reject options. The user’s selection is then sent to the server.
-
Finally, the server validates the authentication and the endpoint gets authenticated.
HTTPS protocol is used for the communication.
This authentication method is recommended to use in combination with another method such as Password or LDAP Password to achieve multi-factor authentication and protect a user from getting SPAM push messages.
NOTE:To use Smartphone authentication method, at least one Advanced Authentication server from each site (if any) should be accessible from the Public URL.
Access Configurations
The following are the configurations required for the Smartphone method:
-
Advanced Authentication server must be accessible by the specified Server URL address from smartphones (HTTPS, outbound).
-
Advanced Authentication server must have a permitted outbound connection to proxy.authasas.com (HTTPS).
Scenario for Authenticating with the Smartphone Method
Bob wants to authenticate on the myexample.com website. When he logs in to the website, the Smartphone authentication method sends a push message to his mobile phone. When he opens the Smartphone app installed on his phone, the Accept and Reject buttons are displayed. If he selects the Accept option, the authentication request is sent over the mobile network (secure) back to the Authentication framework. Without specifying an OTP code, Bob authenticates to myexample.com.
When your smartphone does not have a network connection, you can use a backup OTP as offline authentication.
This section covers the following configurations related to the Smartphone method:
NOTE:You can customize the authentication request message that is displayed on the NetIQ Auth app using the Custom Messages policy.
For more information about customizing the authentication request message, see Customizing Authentication Request Message For Smartphone Method.
9.25.1 Configuring Smartphone Method
To configure the Smartphone method, specify the following details:
|
Parameter |
Description |
|---|---|
|
Push salt TTL |
The server uses this time span to update the Push ID, which is used to identify phone and send the push notification. The default value is 60 seconds. NOTE:It is not recommended to change the default value and this field will be discontinued from Advanced Authentication 6.4. |
|
Learn timeout |
The time that is valid for the user to scan the QR code for enrollment. he default timeout is 60 seconds. |
|
Authentication salt TTL |
Based on the set time span, the smartphone rejects the response from Advanced Authentication app if the response is received too late. The default time is 60 seconds. NOTE:It is not recommended to change the default value and this field will be discontinued from Advanced Authentication 6.4. |
|
TOTP Length |
The length of OTP token used for backup authentication. The default length is 6 digits. |
|
TOTP step |
The time a TOTP is displayed on a screen before the next OTP is generated. The default time is 30 seconds. |
|
TOTP time window |
The time in seconds in which the specified TOTP is accepted. The default time is 300 seconds. |
|
Server URL |
The URL of Advanced Authentication server to where the smartphone app connects for authentication. This URL points to the Public External URLs (Load Balancers) policy. For example, http://<AAServerAddress>/smartphone (/smartphone cannot be changed). It is recommended to use http only for testing and https in the production environment. When using https, you must upload a valid certificate in Server Options. |
|
Require PIN |
Set to ON to enforce the Enable PIN for authenticating to the Smartphone application. A user cannot edit the settings on the application. NOTE:If the PIN is not set, then the user is prompted to set the PIN on launching the app. On the first launch of the app, the user must set the PIN irrespective to the settings. |
|
Minimum PIN length if the PIN is required |
The minimum length of the PIN. The available options are 4,5, and 6. |
|
Require biometrics |
Set to ON to enforce the fingerprint or facial recognition settings for authenticating to the Smartphone application. A user cannot edit the settings on the application. NOTE:Before Advanced Authentication 6.3 Service Pack 5 Patch 1 enabling Require biometrics enabled the Require PIN option. Also, it was not possible to disable Require PIN without disabling Require biometrics. Following are different possibilities of using the Require biometrics and Require PIN options:
|
|
Enroll TOTP method when enrolling Smartphone |
Set to ON to enable enrolling both the Smartphone and TOTP methods during the Smartphone method enrollment. After enrolling, the NetIQ Advanced Authentication application on the user's Smartphone displays only one authenticator. Still, it will correspond to both Smartphone, and TOTP authenticators enrolled on the Advanced Authentication Server. IMPORTANT:Even if you set the option to OFF, the user can use the Smartphone method in following ways:
|
|
Allow to accept/reject authentication through push notification |
Set to ON to display the action buttons Accept and Reject with the notification in the mobile notification bar. This allows users to take action directly from the notification without opening the app. This option is applicable for Android and iOS versions of the NetIQ Authentication app. NOTE:After enrolling the Smartphone method, for the first authentication the actions buttons are not displayed with the notification in the notification bar. Therefore, the user is required to launch the NetIQ Authentication app to accept or reject the request. |
|
Prevent login from a rooted device |
Set to ON to enable a root check for mobile devices. The smartphone app must detect whether the device is rooted and prevent login from that device. Rooted devices can provide administrative privileges to third-party software that is not secured and mostly not allowed by device vendors. |
|
Use image on mobile devices |
Select the option to use a customized image on your Smartphone app. Browse the image. This image is displayed in the About screen of your Smartphone app. The resolution of the image must be 2732×637 pixels. NOTE:The Require PIN, Require biometrics, and Use image on mobile devices policies are automatically applied on the smartphone if a user has an enrolled authenticator in the smartphone app and the app is open on one of the screens: Authentication Requests, Enrolled Authenticators, or Requests History. It takes 2 to 30 seconds to display the authentication request.
|
|
Disable offline authentication |
Select this option to disable users from authenticating using the Smartphone TOTP. By default this option is disabled and users can login using Smartphone even when Smartphone is not connected to a network. Enabling this option will disallow users to use the One-Time Password of the Smartphone method to login to the offline mode. |
|
Allow as first authentication method |
Option that allows a user to authenticate using a chain where Smartphone authenticator is the first authentication method. The option is set to ON by default. Set this option to OFF to prevent user from authenticating using a chain where Smartphone authenticator is the first authentication method. If the option is set to OFF, and a user tries to authenticate using a chain where the Smartphone method is the first authentication method, the user is displayed a The method cannot be first in the login chain message and the user cannot authenticate. |
|
Advanced Settings |
These settings are optional. |
|
Default Vendor |
The Default Vendor is set to NetIQ and this vendor sends the push notifications to the NetIQ Advanced Authentication app for users to complete the Smartphone authentication. NOTE:You can add only the approved vendor as a default vendor. A certificate for your custom application must be provided to Micro Focus and be applied to proxy.authasas.com. |
|
Priority Vendor |
Click Add to add the preferred vendor as a priority vendor that sends push notifications to the custom smartphone application. To understand the requirements to add the priority vendor, see Priority Vendor Requirements. NOTE:You can add only the approved vendor as a priority vendor. A certificate for your custom application must be provided to Micro Focus and uploaded to proxy.authasas.com. Before adding a priority vendor, the default vendor manages all the smartphone enrollment and authentication requests. After you add a priority vendor, new enrollment requests get associated with the priority vendor. Even after adding the priority vendor, the default vendor continues to process the authentication requests of the enrollments that were associated earlier. If you add more than one priority vendor, then the Vendor list appears for the user to select the preferred vendor while enrolling the Smartphone method on the Self Enrollment portal. |
|
Google project ID |
You can specify Google Project ID for your Android app if you have an approved vendor and the Private key (in JSON format) has been generated, provided to Micro Focus, and applied on the proxy.authasas.com. The push notifications are sent only to the application which matches the configured Google Project ID. |
|
Geo Zones |
You can configure Geo-fencing with the Smartphone method. Geo-fencing allows you to authenticate with the Smartphone method with one more factor, which is the geographical location. When you enable geo-fencing, users will be able to authenticate with Smartphone from only allowed geographical locations. You must enable the policy Geo Fencing Options to use geo-fencing. To set up the Geo-fence, see Setting Up Geo-fence for Smartphone. |
NOTE:To use geo-fencing, ensure that access to the location is enabled for the NetIQ Advanced Authentication app on the smartphone.
To configure the Smartphone method as second factor authenticator to secure Windows workstation, see
NOTE:The NetIQ Advanced Authentication app icon displayed in the video has been updated. However, the concept and configuration steps remain same.
9.25.2 Configuring Enrollment Link
Users can enroll the Smartphone method either by a QR code or through a link sent to their email or SMS. You as an administrator must configure the link and send it to all the users whom you want to enroll the authenticator. You can use one of the following links as per the requirement:
https://<public_external_url>/smartphone/enroll
https://<public_external_url>/smartphone/enroll?category=cat1
https://<public_external_url>/smartphone/enroll?tenant=t1
https://<public_external_url>/smartphone/enroll?category=cat2&tenant=t1
Default category is default. For more information about the category, see Event Categories.
Default tenant is TOP. For more information about the tenant, see Multitenancy Options.
For more information about how to set the public external URLs, see Public External URLs (Load Balancers).
To allow users to enroll the Smartphone method using the link, ensure to configure the Smartphone Enrollment Event.
9.25.3 Setting Up Geo-fence for Smartphone
To configure geo-fencing, you need to draw a boundary of the location to be authenticated with a polygon. To configure geo-fencing, perform the following steps:
-
Click Add.
-
Specify the name of the zone.
-
Click the Search icon and specify the address to locate the required geographical location.
You can click the full-screen
 icon to view the map in the full screen.
icon to view the map in the full screen. -
Click the polygon
 icon in the menu bar of the map.
icon in the menu bar of the map. -
Click the starting point on the map and draw the boundary of the specific location to be authenticated.
-
Click to mark the end point of the boundary after you have finished drawing the geo zone.
You can also edit the marked polygon by clicking the edit
 icon.
icon. -
Click Save.
9.25.4 Priority Vendor Requirements
NetIQ sends the push notification to the smartphone application by default. You can add a priority vendor that sends the push notification to the customized iOS application during the authentication. Before adding a priority vendor, you must generate the .p8 key file, obtain Key ID, Bundle ID, and Apple Team ID. The .p8 key file enables the configured priority vendor to send the push notification to any iOS application.
To generate the .p8 key file, perform the following steps:
-
Sign in to your Apple Developer account.
-
Navigate to Certificates, IDs & Profiles > Keys.
-
Click + icon to add a key.
-
Specify name of the key in Key Name.
-
Select Apple Push Notification service (APNs).
-
Click Continue then click Register.
-
Click Download to download the key file.
The name of key file includes the Key ID.
For example, the file name is AuthKeyABCD1234.p8, the ABCD1234 represents the Key ID.
NOTE:Ensure to store and secure the Key file for further use because you cannot download the key file again.
-
Click Membership and gather the TeamID.
-
Click Certificates, IDs & Profiles > Identifiers.
-
Select the name of the application to view the Bundle ID.
NOTE:The Bundle ID is created by the customer who develops the application. Apple allows developers to use reverse domain name notation deriving the bundle identifier for the application.
For example, the Bundle ID for the domain abc.com can be com.abc.<appname>.
To proceed, you must share the above details with the Micro Focus Support team to configure the proxy server.