1.2 Appliance Requirements
Ensure that your system meets the requirements in this section before you begin the installation of the PlateSpin Transformation Manager Appliance.
1.2.1 Appliance Host Server
You deploy the OVF file for the PlateSpin Transformation Manager Appliance on your virtualization host server.
Virtualization Host Server
PlateSpin transformation supports the following virtualization software:
-
VMware ESXi version 5.5 or higher. The ESXi host must have a VMware enterprise license.
-
VMware vSphere Client 5.x or higher. Use this tool to set up the hypervisor environment for the appliance VM.
Micro Focus recommends setting up NTP (Network Time Protocol) for the Appliance and the host server in accordance with the VMware Time Keeping Best Practices for Linux Guests (KB 1006427).
Virtual Machine
The OVF creates a virtual machine. This section describes the VM minimum requirements.
-
Memory: The host server must provide a minimum of 4 GB of memory for the virtual machine. This memory configuration is the appliance default.
-
Processor: The host server must provide a minimum of 2 vCPUs for the virtual machine. This processor configuration is the appliance default.
-
IP Address Information: During the deployment, you must provide the following IP address information for the appliance, including:
-
Static IP address
-
Network mask
-
Gateway IP address
-
DNS host name associated with the IP address
-
IP address of a DNS server
-
IP address or DNS name of the NTP server
Micro Focus recommends setting up NTP for the VM in accordance with the VMware Time Keeping Best Practices for Linux Guests (KB 1006427).
-
Virtual Storage
You must provide a boot disk and a data disk when you deploy the appliance:
-
Disk 1 Boot: The boot partition for the appliance stores the system files, including the guest operating system, all appliance-specific software, and the appliance system event logs that are stored in the /var directory. The default size is 20 GB.
-
Disk 2 /vastorage: The /vastorage partition stores the PlateSpin Transformation Manager software and PostgreSQL database, the appliance configuration information, and the Ganglia health metrics. You must create and add this virtual disk during the appliance installation. The required size is 20 GB or larger.
1.2.2 Appliance Management Console
Most of your management interaction with the PlateSpin Transformation Manager Appliance takes place through the browser-based PlateSpin Transformation Manager Appliance Management Console.
Supported Web Browsers
PlateSpin Transformation Manager supports the following web browsers for the Appliance Management Console:
-
Google Chrome (latest version)
-
Microsoft Internet Explorer 11
-
Mozilla Firefox (latest version)
NOTE:JavaScript (Active Scripting) must be enabled in your web browser.
Supported Languages
The Appliance Management Console supports English (En) and Japanese (Ja) languages in your web browser. Modify the Language setting in your web browser with your preferred language as the first in the list. For translated Online Help, also set your Language preference on www.netiq.com and allow cookies.
Ports and Firewalls
PlateSpin Transformation Manager communications use the following ports. They are opened by default for the appliance, as noted. Ensure that you open the following ports in all firewalls in your network between the PlateSpin Transformation Manager Appliance and the computers you use to access the appliance.
Table 1-1 Communications Ports for Appliance Management
|
Component |
Port |
Description |
|---|---|---|
|
Appliance Management Console |
|
Use this port to securely manage the appliance. |
|
Transformation Manager Database (PostgreSQL) |
5432 |
If you configure a remote PostgreSQL database for the appliance, this port is used by PTM to access to your remote database. PostgreSQL allows TCP traffic, incoming and outgoing. Secure traffic by enabling SSL in the postgresql.conf file on your remote PostgreSQL server. This port is closed by default if the PostgreSQL is installed on the appliance. |
|
SSH |
22 |
You can use SSH to remotely access the appliance to start, stop, or restart it without using a VMware client. SSH is disabled by default. See Section 3.4.1, Starting, Stopping, or Restarting System Services. |
|
Ganglia |
8649 (secure, default) 9080 (non-secure) |
The Ganglia gmond daemon uses UDP port 8649 for communications. The gmetad daemon uses TCP port 8649 for metrics data. You can enable port 9080 to allow anonymous access to the Ganglia monitoring information. See Section 3.7.3, View Ganglia Metrics Directly Using Port 9080 (Not Secure). |
1.2.3 Transformation Manager Web Interface
PlateSpin Transformation Manager server software is automatically installed on the Appliance. User interaction with the PlateSpin Transformation Manager Server takes place through the browser-based PlateSpin Transformation Manager Web Interface.
Supported Web Browsers
PlateSpin Transformation Manager supports the following web browsers for the PlateSpin Server Web Interface:
-
Google Chrome (latest version)
-
Microsoft Internet Explorer 11
-
Mozilla Firefox (latest version)
NOTE:JavaScript (Active Scripting) must be enabled in your web browser.
Supported Languages
The Web Interface supports English (En) and Japanese (Ja) languages in your web browser. Modify the Language setting in your web browser with your preferred language as the first in the list.
Internet Access
PlateSpin Transformation Manager must be able to communicate across the public Internet with the Micro Focus License Server, using the following URL:
https://www.novell.com/center/nodeactivationservice/1_0/subscriptions/getPTMLicenseCount
Internet access is required to activate your License Key on the Configuration > Licenses page in the PlateSpin Transformation Manager Web Interface. As you begin to configure workloads, Transformation Manager communicates with the License Server to verify license availability as you edit workloads individually or with bulk actions. It also synchronizes license information daily. See Managing Licenses
in the PlateSpin Transformation Manager User Guide.
To provide Internet access through a proxy server, you must configure the Appliance as a proxy client for that server. See Configuring Proxy Client Settings.
Ports and Firewalls
PlateSpin Transformation Manager communications use the following ports for the PlateSpin Transformation Manager Server. They are opened by default for the Appliance, as noted. Ensure that you open the following ports in all firewalls in your network between the PlateSpin Transformation Manager Appliance and the computers you use to access the PlateSpin Transformation Manager Server.
Table 1-2 Communications Ports for the Transformation Manager Web Interface
|
Component |
Port |
Description |
|---|---|---|
|
Web Interface |
|
Port 8183 is enabled by default. NOTE:Micro Focus recommends that you use the secure port and SSL options for accessing the Web Interface. For security reasons, port 8182 is disabled by default. |
Table 1-3 shows the protocol and port required for event messaging in a PlateSpin Migration Factory environment. These messages reflect events and state changes and do not contain sensitive information.
Table 1-3 Event Messaging Requirements for Network Protocols and Ports
|
Traffic |
Network Protocol and Port |
Other Requirements |
|---|---|---|
|
Event Messaging |
61613 (Stomp, allow TCP, incoming) (not secure) |
This port is open by default on the PlateSpin Transformation Manager Appliance, which includes a pre-installed instance of PlateSpin Migrate Connector. Open this port on all other Connector host servers, the PlateSpin Migrate servers configured for the project, and the firewalls between them. |
1.2.4 PlateSpin Migrate Connector
An instance of the PlateSpin Migrate Connector is automatically installed and configured to work with all projects on the PlateSpin Transformation Manager server on the Appliance. User interaction with the PlateSpin Migrate Connector takes place through a configuration file on the Appliance and global settings in the PlateSpin Transformation Manager Web Interface. See the PlateSpin Migrate Connector Quick Start.
You can install additional instances of Migrate Connector on your SUSE Linux Enterprise Server servers in the same network as source workloads. See Installing, Upgrading, or Uninstalling PlateSpin Migrate Connector
in the PlateSpin Migrate Connector Quick Start.
1.2.5 Network Connectivity and Access Requirements
Ensure that the network connections are working:
-
Between the PlateSpin Migrate Connector and the source workloads
-
Between the PlateSpin Migrate Connector and the PlateSpin Migrate servers
-
Between the source network and target network
PlateSpin Migrate Connector requires network connectivity to the following resources, based on its assignment to the PlateSpin Transformation Manager server or to a specific project:
-
Its assigned PTM server
-
Source workloads
-
Target VMware cluster hosts
-
PlateSpin Migrate servers
In addition, review the security guidelines in Section 1.2.6, Security Guidelines.
Your environment must meet the requirements described in this section for network connectivity and access. Refer to the ports map in Figure 1-1.
Figure 1-1 Ports Map for PlateSpin Migration Factory
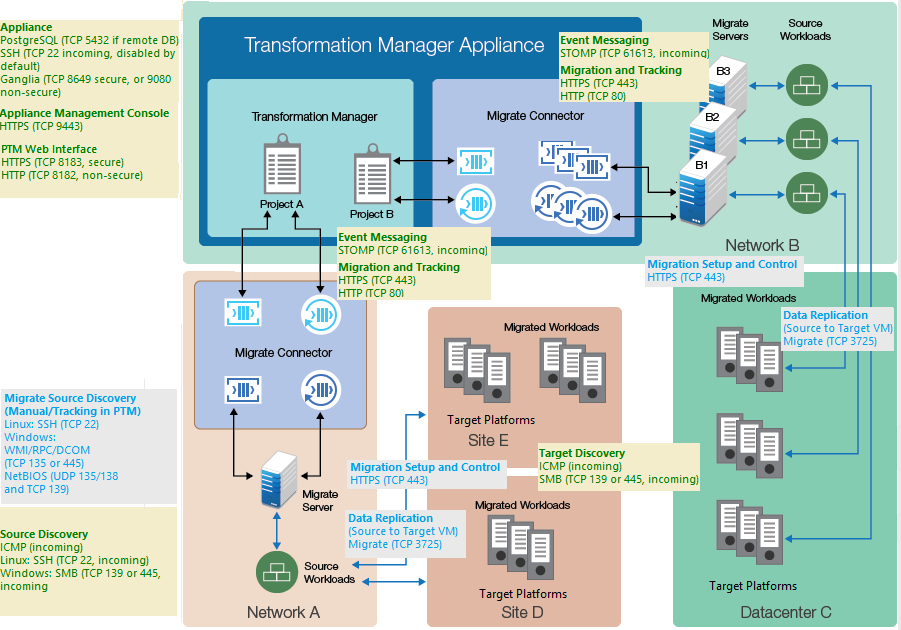
Event Messaging
PlateSpin Migrate provides an event messaging service based on RabbitMQ for use in the PlateSpin Migration Factory environment. Each PlateSpin Migrate server can publish workload migration state change messages to PlateSpin Migrate Connector instances that subscribe to the service on behalf of PlateSpin Transformation Manager projects.
Table 1-3 shows the protocol and port required for event messaging in a PlateSpin Migration Factory environment. These messages reflect events and state changes and do not contain sensitive information.
Table 1-4 Event Messaging Requirements for Network Protocols and Ports
|
Traffic |
Network Protocol and Port |
Other Requirements |
|---|---|---|
|
Event Messaging |
61613 (Stomp, allow TCP, incoming) (not secure) |
This port is open by default on the PlateSpin Transformation Manager Appliance, which includes a pre-installed instance of PlateSpin Migrate Connector. Open this port on all other Connector host servers, the PlateSpin Migrate servers configured for the project, and the firewalls between them. |
Workload Discovery
Workload discovery in PlateSpin Transformation Manager requires that you enable incoming ping (ICMP echo reply and ICMPv4-In echo request) traffic for source workloads and firewalls. PlateSpin supports only IPv4. For information about required software, network, and port settings for workload discovery, see Table 1-5.
Table 1-5 Workload Discovery Requirements for Network Access and Communications
|
Discovery Target |
Network Protocols and Ports |
Other Requirements |
|---|---|---|
|
Windows workloads |
|
|
|
Linux workloads |
|
Root-level access. For information on using an account other than root, see KB Article 7920711. |
Target Host Discovery
Host discovery requires that you enable incoming ping (ICMP echo reply and ICMPv4-In echo request) traffic for target VMware hosts and firewalls. PlateSpin supports only IPv4. For information about required software, network, and port settings for host discovery, see Table 1-6.
Table 1-6 Host Discovery Requirements for Network Access and Communications
|
Discovery Target |
Network Protocols and Ports |
Other Requirements |
|---|---|---|
|
VMware Cluster hosts |
|
VMware account with an Administrator role |
Workload Migration
Table 1-7 provides the ports to open in the firewall and on each of the Migrate servers in order for PlateSpin Transformation Manager to use the Migrate REST APIs for automated migration. In addition, the Migration Server resource for Migrate server must provide a valid Credentials resource for the Migrate Administrator user.
Table 1-7 REST API Requirements for Network Access and Communications
|
REST API Traffic |
Network Protocol and Port |
Access |
|---|---|---|
|
HTTPS (secure) |
Port 443, TCP, incoming and outgoing |
Administrator login credentials for the Migrate server |
|
HTTP (non-secure) |
Port 80, TCP, incoming and outgoing |
Administrator login credentials for the Migrate server |
In addition, Transformation Manager requires that your migration environment meets the PlateSpin Migrate requirements for network communications. See Requirements for Migration
in the PlateSpin Migrate 12.2.1 User Guide.
1.2.6 Security Guidelines
PlateSpin Transformation Manager provides several key security options.
SSL (HTTPS) for Secure Communications
For secure connections between PlateSpin Migrate Connector and PlateSpin Transformation Manager, the Jetty SSL settings on the PlateSpin Transformation Manager Appliance VM are configured with the latest recommended security settings.
Ensure that you configure the Appliance to use port 8183 for secure communications.
SSL Certificate for Secure Communications
The installation of the PlateSpin Transformation Manager Appliance generates and installs a self-signed certificate for SSL (Secure Sockets Layer) communications. It uses the DNS name that you specify for the PlateSpin Transformation Manager Appliance. The certificate applies to the appliance and the software.
For higher security, Micro Focus recommends that you use a server certificate that is signed by a trusted certificate authority (CA) such as VeriSign or Equifax. You can use your own existing signed certificate, or you can use the Digital Certificate tool on the appliance to create a certificate, have it signed by a trusted certificate authority, and then add it to the appliance.
NOTE:The DNS name of the server must match the subject of the security certificate.
To import your signed certificate, you must provide the certificate and key, as described in Digital Certificates
in the PlateSpin Transformation Manager Appliance Guide.
Antivirus Setup for Discovery
To run discovery on Windows workloads, you might need to exclude certain services, files, and folders from antivirus protection.
-
Service: Exclude the PTM Discovery Service (PTMDiscoverySvc.exe) from antivirus protection.
This service uses the PsExec utility to run remote commands on the target MachineDiscoveryReader.dll.
-
Files and Folders: Exclude the PlateSpinDiscovery directory, including any subdirectories and files, from antivirus protection.
During each discovery attempt, all binaries and services files the PTM Discovery Service creates and uses are located under the PlateSpinDiscovery directory in the first Windows share it discovers, such as Admin$.
-
Ports: The antivirus software must not restrict any of the ports needed for discovery. For port information, see Workload Discovery.
Proxy Services
PTM Server is proxy aware. It can use the Proxy Client settings on the host Appliance for communications with the Micro Focus License Server. Persistent Internet access is required to license the individual workloads during the planning process. You might need to configure proxy services in a highly restrictive networking environment.
See Configuring Proxy Client Settings
in the Appliance Guide.
Unique Login Credentials for Each Connector Instance
To distinguish actions initiated by the project’s Connector instance, we strongly recommend that you create a unique User object to use for the Connector login credentials instead of using a real User object. Create this special user as a System user, then assign it a Project Architect role at the Project level. Create a different User object for each Connector instance with permissions appropriate for its assigned project.
Password Security for Credentials Resources
PlateSpin Transformation Manager uses industry-standard strong encryption to secure passwords in the PTM database for the Credentials resources used to access source machines and target hosts. The 16-digit key is randomly generated during the Appliance installation. The key is unique to each PTM server. As new Credentials resources are created, their passwords will be encrypted with this key.
The encryption key is stored as the tm.encrypt.key property in the system.properties file:
/opt/microfocus/ps_transform_mgr/config/system.properties
PTM writes the system.properties file to a ZIP file and saves it in the /vastorage/conf/ folder when the appliance shuts down.
The system.properties file is protected by the strength of the password you set for root and other system users on the Appliance as well as other security best practices in your data center.