1.2 Traditional and ESP-Enabled SSL VPNs
The Novell SSL VPN can be deployed as either an ESP-enabled SSL VPN or a Traditional SSL VPN.
When SSL VPN is deployed without the Access Gateway, an Embedded Service Provider (ESP) component is installed along with the SSL VPN server. This deployment requires the Identity Server and the Administration server to also be installed. This type of deployment is called an ESP-enabled Novell SSL VPN.
When SSL VPN is deployed with the Access Gateway, it is called a Traditional Novell SSL VPN. In this type of installation, SSL VPN is deployed with the Identity Server, Administration Console, and the Linux Access Gateway components of Novell Access Manager.
1.2.1 ESP-Enabled Novell SSL VPN
In an ESP-enabled Novell SSL VPN, the process involved in establishing a secure connection between a client machine and the different components of Novell Access Manager is as follows:
-
The user specifies the following URL to access the SSL VPN server:
https://<www.sslvpn.novell.com>/sslvpn/login
<www.sslvpn.novell.com> is the DNS name of the SSL VPN server, and /sslvpn/login is the path of the SSL VPN server.
-
The SSL VPN redirects the browser to the Identity Server for authentication.
-
After successful authentication, the Identity Server redirects the browser back to SSL VPN.
-
The Identity Server propagates the session information to the SSL VPN server through the Embedded Service Provider.
-
The SSL VPN server injects the SSL VPN policy for that user into the SSL VPN servlet. The SSL VPN servlet processes the parameters and sends the policy information back to the server.
-
The SSL VPN checks if the client machine has sufficient security restraints. For more information on client integrity checks, see Section 3.1, Configuring Policies to Check the Integrity of the Client Machine.
-
When the user accesses the applications behind the protected network, the connection goes through the secure tunnel formed with the SSL VPN server.
-
The browser stays open throughout the SSL VPN connection to allow the keep alive packets.
-
When the user clicks the logout button to close the SSL VPN session, all the client components are automatically uninstalled from the workstation.
1.2.2 Traditional Novell SSL VPN
The following figure shows the Novell Access Manager components and the process involved in establishing a secure connection between a client machine and traditional Novell SSL VPN server. In this type of deployment, the Linux Access Gateway accelerates and protects the SSL VPN server.
Figure 1-1 Traditional Novell SSL VPN
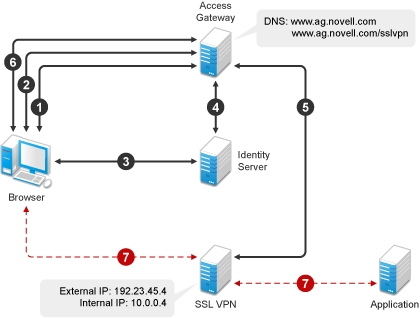
-
The user specifies the following URL to access the SSL VPN server:
https://<www.ag.novell.com>:8443/sslvpn/login<www.ag.novell.com> is the DNS name of the Access Gateway that accelerates the SSL VPN server, and /sslvpn/login is the path of the SSL VPN server.
-
The Access Gateway redirects the user to the Identity Server for authentication, because the URL is configured as a protected resource.
-
The Identity Server authenticates the user’s identity.
-
The Identity Server propagates the session information to the Access Gateway through the Embedded Service Provider.
-
The Access Gateway injects the SSL VPN policy for that user into the SSL VPN servlet. The SSL VPN servlet processes the parameters and sends the policy information back to the Access Gateway.
-
The SSL VPN checks if the client machine has sufficient security restraints. For more information on client integrity checks, see Section 3.1, Configuring Policies to Check the Integrity of the Client Machine.
-
One of the following actions takes place, depending on the mode of the SSL VPN connection:
-
In Enterprise mode, a tunnel interface is created and is bound with the tunnel IP address assigned by the SSL VPN server. A secure tunnel is established between the client machine and the SSL VPN server, and the routing table is updated with the protected network configuration.
-
In Kiosk mode, a secure tunnel is established between the client machine and the SSL VPN server, and the protected network configuration is pushed to the client.
-
-
When the user accesses the applications behind the protected network, the connection goes through the secure tunnel formed with the SSL VPN server and not through the Access Gateway.
-
The browser stays open throughout the SSL VPN connection to allow the keep alive packets to go through the Access Gateway.
-
When the user clicks the logout button to close the SSL VPN session, all the client components are automatically uninstalled from the workstation.
1.2.3 High-Bandwidth and Low-Bandwidth SSL VPNs
Novell SSL VPN comes in high-bandwidth and low-bandwidth versions.
Low-Bandwidth Version: The default SSL VPN server is a low-bandwidth version. It is restricted to 249 simultaneous user connections and a transfer rate of 90 Mbits per second because of export restrictions.
High-Bandwidth Version: The high-bandwidth version does not have the connection and performance restrictions. It is essential to have the high-bandwidth SSL VPN installed if you want to cluster the SSL VPN servers.
If the export law permits, you can order the high-bandwidth SSL VPN RPM and get the high-bandwidth capabilities at no extra cost. After the export controls have been satisfied, the order will be fulfilled. You can install the high-bandwidth SSL VPN RPM on both the Traditional Novell SSL VPN server and on the ESP-enabled Novell SSL VPN server.
Your regular Novell sales channel can determine if the export law allows you to order the high-bandwidth version at no extra cost.
For more information on how to order and install the high-bandwidth SSL VPN, and to upgrade the high-bandwidth version to the latest build, see Installing the Key for the High-Bandwidth SSLVPN
in the Novell Access Manager 3.1 SP4 Installation Guide.