14.6 Mapping LDAP and Liberty Attributes
You can create an LDAP attribute map or edit an existing one. To create an attribute map, you specify how single-value and multi-value data items map to single-value and multi-value LDAP attributes. A single-value attribute can contain no more than one value, and a multi-value attribute can contain more than one. An example of a single-value attribute might be a person’s gender, and an example of a multi-value attribute might be a person’s various e-mail addresses, phone numbers, or titles.
-
In the Administration Console, click >> Edit > .
-
Select one of the following actions:
New: Allows you create an LDAP attribute mapping. Select from the following types:
-
One to One: Maps a single Liberty attribute to a single LDAP attribute. See Section 14.6.1, Configuring One-to-One Attribute Maps.
-
Employee Type: Maps the Employee Type attribute to an LDAP attribute, then maps the possible Liberty values to LDAP values. See Section 14.6.2, Configuring Employee Type Attribute Maps.
-
Employee Status: Maps the Employee Status attribute to an LDAP attribute, then maps the possible Liberty values to LDAP values. See Section 14.6.3, Configuring Employee Status Attribute Maps.
-
Postal Address: Maps the Postal Address attribute to either multiple LDAP attributes or a delimited LDAP attribute. See Section 14.6.4, Configuring Postal Address Attribute Maps.
-
Contact Method: Maps the Contact Method attribute to multiple LDAP attributes. See Section 14.6.5, Configuring Contact Method Attribute Maps.
-
Gender: Maps the Gender attribute to an LDAP attribute, then maps the possible Liberty values to LDAP values. See Section 14.6.6, Configuring Gender Attribute Maps.
-
Marital Status: Maps the Marital Status attribute to an LDAP attribute, then maps the possible Liberty values to LDAP values. See Section 14.6.7, Configuring Marital Status Attribute Maps.
Delete: Deletes the selected mapping.
Enable: Enables the selected mapping.
Disable: Disables the selected mapping. When the mapping is disabled, the server does not load the definition. However, the definition is not deleted.
-
-
Click , then update the Identity Server.
14.6.1 Configuring One-to-One Attribute Maps
A one-to-one map enables you to map single-value and multiple-value LDAP attribute names to standard Liberty attributes. A default one-to-one attribute map is provided with Access Manager, but you can also define your own.
An example of a one-to-one attribute map might be the single-valued Liberty attribute Common Name (CommonName) used by the Personal Profile that is mapped to the LDAP attribute givenName. You can further configure the various Liberty values to map to any LDAP attribute names that you use.
-
In the Administration Console, click > > > > > > .
-
Configure the following fields:
Type: Displays the type of mapping you are modifying or creating:
Name: The name you want to give the map.
Description: A description of the map.
Access Rights: A drop-down menu that provides the broadest control for the page. If you set this to , you can specify rights for individual data items.
In order for user provisioning to succeed, you must select from the drop-down menu for any maps that use an attribute during user provisioning.
User Stores: The user store that a map applies to. If a user logs into a user store that is not in the map’s user store list, that map is not used to read or write attributes for that user.
-
Use the following guidelines to configure the map:
-
Mapping Personal Profile Single-Value Data Items to LDAP Attributes
-
Mapping Personal Profile Multiple-Value Data Items to LDAP Attributes
-
Mapping Employee Profile Single-Value Data Items to LDAP Attributes
-
Mapping Employee Profile Multiple-Value Data Items to LDAP Attributes
-
Mapping Custom Profile Single-Value Data Items to LDAP Attributes
-
Mapping Custom Profile Multiple-Value Data Items to LDAP Attributes
-
-
After you create the mapping, click .
-
On the LDAP Attribute Mapping page, click .
-
Update the Identity Server.
Mapping Personal Profile Single-Value Data Items to LDAP Attributes
The data items displayed are single-value Liberty Personal Profile attributes that you can map to the single-valued LDAP attributes that you have defined for your directory.
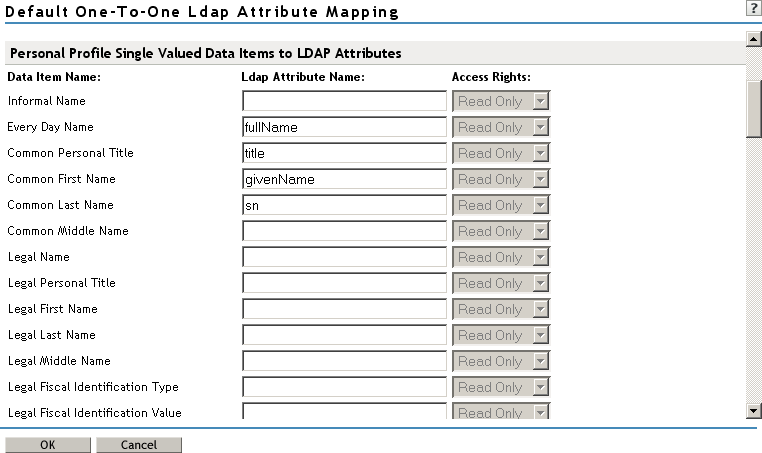
Mapping Personal Profile Multiple-Value Data Items to LDAP Attributes
Use the fields on this page to map multiple-value attributes from the Liberty Personal Profile to the multiple-value LDAP attributes you have defined for your directory. For example, you can map the Liberty attribute Alternate Every Day Name (AltCN) to the LDAP attribute you have defined for this purpose in your directory.
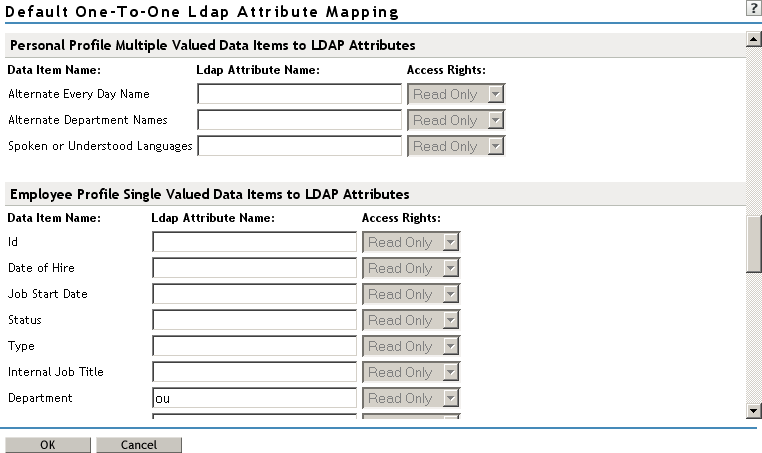
Mapping Employee Profile Single-Value Data Items to LDAP Attributes
Map the Liberty Employee Profile single-value attributes to the LDAP attributes you have defined in your directory for entries such as ID, Date of Hire, Job Start Date, Department, and so on.
Mapping Employee Profile Multiple-Value Data Items to LDAP Attributes
Map the Liberty Employee Profile multiple-value attributes to the LDAP attributes you have defined in your directory.
Mapping Custom Profile Single-Value Data Items to LDAP Attributes
Map custom Liberty profile single-value attributes to LDAP attributes you have defined in your directory. These attributes are customizable strings associated with the Custom Profile.
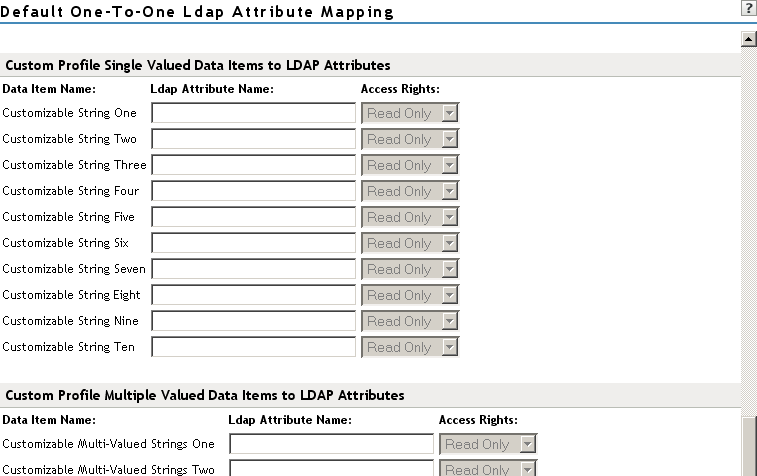
Customizable String (1 - 10): The Custom Profile allows custom single-value and multiple-value attributes to be defined without using the Data Model Extension XML to extend a service’s schema. To use a customizable attribute, navigate to the tab on the Custom Profile Details page (see Section 14.4, Customizing Attribute Names). Use the page to customize the name of any of the predefined single-value or multiple-value customizable attributes in the Custom Profile. After you customize a name, you can use that attribute in the same way you use any other profile attribute.
Mapping Custom Profile Multiple-Value Data Items to LDAP Attributes
Customizable Multi-Valued Strings (1 - 5): Similar to customizable strings for single-value attributes, except these attributes can have multiple values. Use this list of fields to map directory attributes that can have multiple values to multiple-value strings from the Custom Profile.
14.6.2 Configuring Employee Type Attribute Maps
You can map the LDAP attribute name and values to the Liberty profile values for Employee Type. This is an Employee Profile attribute. Examples of Liberty values appended to this attribute include Contractor Part Time, Contractor Full Time, Full Time Regular, and so on.
-
In the Administration Console, click > > > > > > .
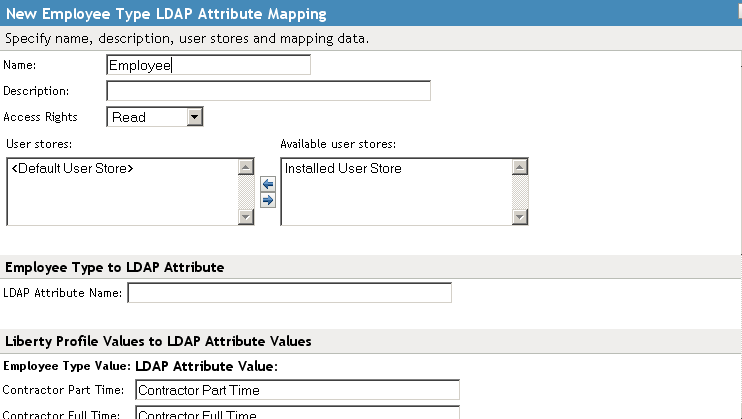
-
Configure the following fields:
Name: The name you want to give the map.
Description: A description of the map.
Access Rights: A drop-down menu that provide the broadest control for the page. If you set this to , you can specify rights for individual data items.
In order for user provisioning to succeed, you must select from the drop-down menu for any maps that use an attribute during user provisioning.
User Stores: The user store that a map applies to. If a user logs into a user store that is not in the map’s user store list, that map is not used to read or write attributes for that user.
-
In the field, type the LDAP attribute name that you want to map to the Liberty Employee Type attribute.
-
In the fields, type the predefined LDAP attribute values that you want to map to the values.
These are the values that you want to store in the LDAP attribute for each given Liberty attribute value. The LDAP attribute map then maps the actual Liberty URI value, back and forth, to this supplied value.
-
Click .
-
On the LDAP Attribute Mapping page, click .
-
Update the Identity Server.
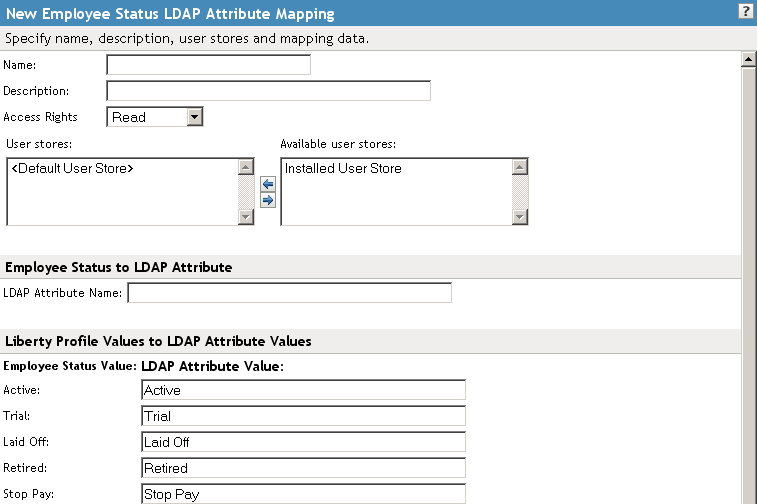
14.6.3 Configuring Employee Status Attribute Maps
You can map the LDAP attribute name and values to the Liberty profile values for Employee Status. This is an Employee Profile attribute. Examples of the values appended to this Liberty attribute include Active, Trial, Retired, Terminated, and so on.
-
In the Administration Console, click > > > > > > .
-
Configure the following fields:
Name: The name you want to give the map.
Description: A description of the map.
Access Rights: A drop-down menu that provide the broadest control for the page. If you set this to , you can specify rights for individual data items.
In order for user provisioning to succeed, you must select from the drop-down menu for any maps that use an attribute during user provisioning.
User Stores: The user store that a map applies to. If a user logs into a user store that is not in the map’s user store list, that map is not used to read or write attributes for that user.
-
In the field, type the LDAP attribute name that you want to map to the element.
-
In the fields, type the predefined LDAP attribute values that you want to map to the values.
These are the values that you want to store in the LDAP attribute for each given Liberty attribute value. The LDAP attribute map then maps the actual Liberty URI value, back and forth, to this supplied value.
-
Click .
-
On the LDAP Attribute Mapping page, click .
-
Update the Identity Server.
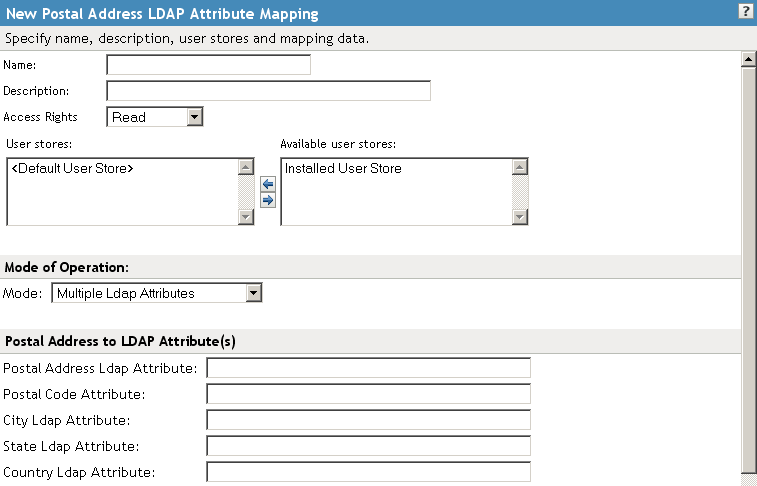
14.6.4 Configuring Postal Address Attribute Maps
You can map the LDAP attribute name and values to the Liberty profile values for Postal Address. The PostalAddress element refers to the local address, including street or block with a house number, and so on. This is a Personal Profile attribute.
-
In the Administration Console, click > > > > > > .
-
Configure the following fields:
Name: The name you want to give the map.
Description: A description of the map.
Access Rights: A drop-down menu that provide the broadest control for the page. If you set this to , you can specify rights for individual data items.
In order for user provisioning to succeed, you must select from the drop-down menu for any maps that use an attribute during user provisioning.
User Stores: The user store that a map applies to. If a user logs into a user store that is not in the map’s user store list, that map is not used to read or write attributes for that user.
-
In the drop-down menu, select either or .
Multiple LDAP Attributes: Allows you to map multiple LDAP attributes to multiple Liberty Postal Address elements. When you select this option, the following Liberty Postal Address elements are displayed under the group. Type the LDAP attributes that you want to map to the Liberty elements.
-
Postal Address
-
Postal Code
-
City
-
State
-
Country
Single Delimited LDAP Attributes: Allows you to specify one LDAP attribute that is used to hold multiple elements of a Liberty Postal Address in a single delimited value. When you select this option, the page displays the following fields:
-
Delimited LDAP Attribute Name: The delimited LDAP attribute name you have defined for the LDAP postal address that you want to map to the Liberty Postal Address attribute.
-
Delimiter: The character to use to delimit single-value entries. A $ sign is the default delimiter.
-
-
(Single Delimited LDAP Attributes mode) Under , specify the order in which the information is contained in the string. Select 1 for the value that comes first in the string, 2 for the value that follows the first delimiter, etc.
-
(Multiple LDAP Attributes mode) Under , fill in the following options:
Nickname: (Required) A Liberty element name used to identify the Postal Address object.
Contact Method Type: Select the contact method type, such as , , , and so on.
-
Click .
-
On the LDAP Attribute Mapping page, click .
-
Update the Identity Server.
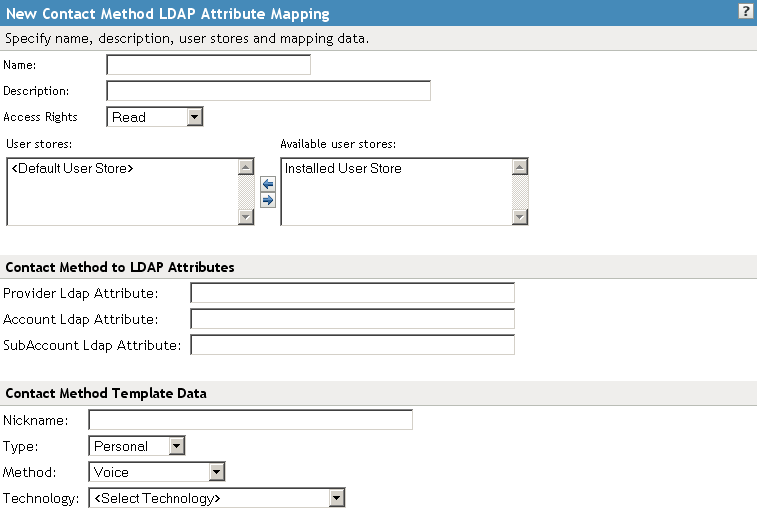
14.6.5 Configuring Contact Method Attribute Maps
You can map the LDAP attribute you have defined for contact methods to the Liberty attribute Contact Method (MsgContact).
-
In the Administration Console, click > > > > > > .
-
Configure the following fields:
Name: The name you want to give the map.
Description: A description of the map.
Access Rights: A drop-down menu that provide the broadest control for the page. If you set this to , you can specify rights for individual data items.
In order for user provisioning to succeed, you must select from the drop-down menu for any maps that use an attribute during user provisioning.
User Stores: The user store that a map applies to. If a user logs into a user store that is not in the map’s user store list, that map is not used to read or write attributes for that user.
-
Under , fill in the following fields to map to the Liberty Contact Method attribute:
Provider LDAP Attribute: Maps to the Liberty attribute MsgProvider, which is the service provider or domain that provides the messaging service.
Account LDAP Attribute: Maps to the Liberty attribute MsgAccount, which is the account or address information within the messaging provider.
SubAccount LDAP Attribute: Maps to the Liberty MsgSubaccount, which is the subaccount within a messaging account, such as the voice mail box associated with a phone number.
-
Under , specify the settings for the following Liberty attribute values:
Nickname: Maps to the Liberty attribute Nick, which is an informal name for the contact.
Type: Maps to the Liberty attribute MsgType (such as Mobile, Personal, or Work).
Method: Maps to the Liberty MsgMethod (such as Voice, Fax, or E-mail).
Technology: Maps to the Liberty attribute MsgTechnology (such as Pager, VOIP, and so on).
-
Click .
-
On the LDAP Attribute Mapping page, click .
-
Update the Identity Server.
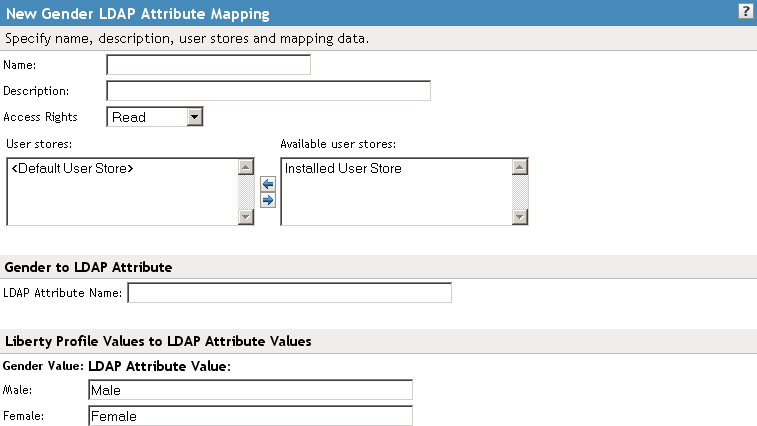
14.6.6 Configuring Gender Attribute Maps
You can map the LDAP attribute name and values to the Liberty profile values for the Gender attribute. You can use gender to differentiate between people with the same name, especially in countries where national ID numbers cannot be collected. This is a Personal Profile attribute.
-
In the Administration Console, click > > > > > > .
-
Configure the following fields:
Name: The name you want to give the map.
Description: A description of the map.
Access Rights: A drop-down menu that provide the broadest control for the page. If you set this to , you can specify rights for individual data items.
In order for user provisioning to succeed, you must select from the drop-down menu for any maps that use an attribute during user provisioning.
User Stores: The user store that a map applies to. If a user logs into a user store that is not in the map’s user store list, that map is not used to read or write attributes for that user.
-
In the field, type the LDAP attribute name that you want to map to the Liberty element Gender.
-
In the fields, type the predefined LDAP attribute values that you want to map to the Gender values.
These are the values that you want to store in the LDAP attribute for each given Liberty attribute value. The LDAP attribute map then maps the actual Liberty URI value, back and forth, to this supplied value.
-
Click .
-
On the LDAP Attribute Mapping page, click .
-
Update the Identity Server.
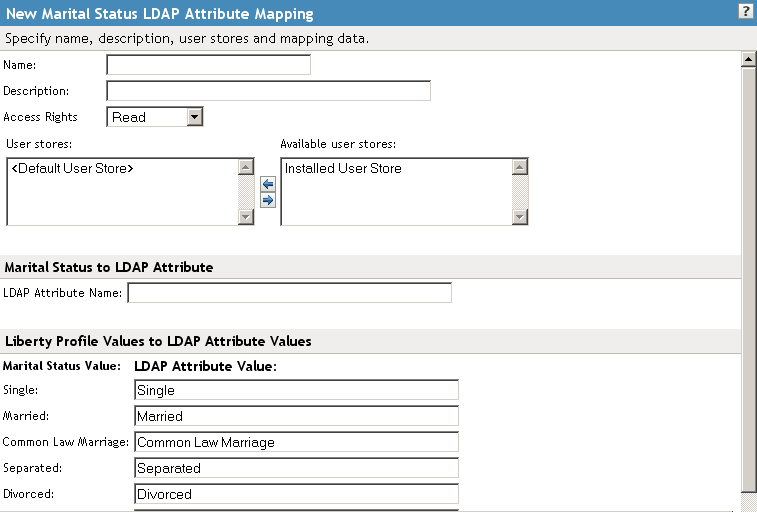
14.6.7 Configuring Marital Status Attribute Maps
You can map the LDAP marital status attribute to the Liberty attribute. The Liberty Marital Status (MaritalStatus) element includes appended values such as single, married, divorced, and so on. For example, urn:liberty:id-sis-pp:maritalstatus:single. This is a Personal Profile attribute.
-
In the Administration Console, click > > > > > > .
-
Configure the following fields:
Name: The name you want to give the map.
Description: A description of the map.
Access Rights: A drop-down menu that provide the broadest control for the page. If you set this to , you can specify rights for individual data items.
In order for user provisioning to succeed, you must select from the drop-down menu for any maps that use an attribute during user provisioning.
User Stores: The user store that a map applies to. If a user logs into a user store that is not in the map’s user store list, that map is not used to read or write attributes for that user.
-
In the field, type the LDAP attribute name that you want to map to the Liberty element Marital Status (MaritalStatus).
-
In the fields, type the predefined LDAP attribute values that you want to map to the MaritalStatus values.
These are the values that you want to store in the LDAP attribute for each given Liberty attribute value. The LDAP attribute map then maps the actual Liberty URI value, back and forth, to this supplied value.
-
Click .
-
On the LDAP Attribute Mapping page, click .
-
Update the Identity Server.