11.7 Completing the Installation of the Identity Applications
This section provides instructions for activities that you might want to perform after installing identity application and their framework:
11.7.1 Checking the Health of the Server in a Clustered Environment
For more information see, Checking the Health of the Server
11.7.2 Accessing the Oracle Database Using Oracle Service Name
You can connect to the Oracle database by using Oracle System ID (SID) or Oracle Service Name. The identity applications installer accepts only SID. If you want to access the database by using a service name, complete the identity applications installation to one database instance by connecting through SID. After the installation is completed, perform the following actions:
-
Create a service name in the Oracle database by running the following command:
alter system set service_names='SERVICE1' scope=both sid='*';
where SERVICE 1 is the name of the Oracle service.
NOTE:You can specify the service name in uppercase or lowercase. It is not case-sensitive.
-
Define the service name in Tomcat’s server.xml file by modifying the Oracle data source details in the file:
url="jdbc:oracle:thin:@IP:PORT/service1"
-
Restart Tomcat.
-
Verify that the service name is included in the catalina.out log file.
-
Verify that the identity applications are properly connected to the database.
11.7.3 Manually Creating the Database Schema
When you install the identity applications, you can postpone connecting to the database or creating tables in the database. If you do not have permissions to the database, you might need to choose this option. The installation program creates a SQL file that you can use to create the database schema. You can also recreate the database tables after installation without having to reinstall. To do so, you delete the database for the identity applications and create a new database with the same name.
Using the SQL File to Generate the Database Schema
This section assumes that the installation program created a SQL file that you can execute to generate the database schema. If you do not have the SQL file, see Manually Creating the SQL File to Generate the Database Schema.
NOTE:Do not use SQL*Plus to execute the SQL file. The line lengths in the file exceed 4000 characters.
-
Stop the Application Server.
-
Login to the Database Server.
-
Delete the database that is used by the identity applications.
-
Create a new database with the same name as the one that was deleted in Step 3.
-
Navigate to the SQL script that the installation process created, by default in the /installation_path/userapp/sql directory.
-
Have the database administrator run the SQL script to create and configure the User Application database.
-
Restart Tomcat.
Manually Creating the SQL File to Generate the Database Schema
You can recreate the database tables after installation without having to reinstall and without having the SQL file. This section helps you create the database schema in the event that you do not have the SQL file.
-
Stop Tomcat.
-
Log in to the server that hosts your identity applications database.
-
Delete the existing database.
-
Create a new database with the same name as the one that you deleted in Step 3.
-
In a text editor, open the NetIQ-Custom-Install.log file, located by default at the root of the installation directory for the identity applications. For example:
C:\NetIQ\idm\apps\UserApplication
-
Search and copy the below command from the NetIQ-Custom-Install.log file:
C:\NetIQ\idm\jre\bin\java -Xms256m -Xmx256m -Dwar.context.name=IDMProv -Ddriver.dn="cn=User Application Driver,cn=driverset1,o=system" -Duser.container="o=data" -jar C:\NetIQ\idm\jre\liquibase.jar --databaseClass=liquibase.database.core.PostgresDatabase --driver=org.postgresql.Driver --classpath=C:\NetIQ\idm\apps\postgresql\postgresql-9.4.1212jdbc42.jar C:\NetIQ\idm\apps\UserApplication\IDMProv.war --changeLogFile=DatabaseChangeLog.xml --url="jdbc:postgresql://localhost:5432/idmuserappdb" --contexts="prov,newdb" --logLevel=info --logFile=C:\NetIQ\idm\apps\UserApplication\db.out --username=******** --password=******** update
-
Log in to the server where you installed the database for the identity applications.
-
In a terminal, paste the command string that you copied.
NOTE:The command should be updateSQL. If it is update, change the command to updateSQL.
-
In the command, replace the asterisks (*) that represent the database username and password with the actual values required to authenticate. Also, ensure the name of the SQL file is unique.
-
Execute the command.
-
(Conditional) If the process generates a SQL file instead of populating the database, provide the file to your database administrator to import into the database server. For more information, see Using the SQL File to Generate the Database Schema.
-
After the database administrator imports the SQL file, start Tomcat.
11.7.4 Manually Import the Identity Applications and Identity Reporting Certificates into Identity Vault
-
If you have custom certificates for Identity Applications and Identity Reporting components, import those certificates into the Identity Vault at C:\NetIQ\eDirectory\jre\lib\security\cacerts.
For example, you can use the following keytool command to import certificates into Identity Vault:
keytool -import -trustcacerts -alias <User Application certificate alias name> -keystore <cacerts file> -file <User Application certificate file>
-
If you install SSPR on a different server than the User Application server, ensure that the SSPR application certificate is added to User Application’s cacerts.
For example, you can use the following keytool command to import certificates into User Application:
keytool -import -trustcacerts -alias <SSPR certificate alias name> -keystore <cacerts> -file <SSPR certificate file>
11.7.5 Recording the Master Key
NetIQ recommends that you copy the encrypted master key and record it in a safe place immediately after installation. If this installation is on the first member of a cluster, use this encrypted master key when installing the identity applications on other members of the cluster.
WARNING:Always keep a copy of the encrypted master key. You need the encrypted master key to regain access to encrypted data if the master key is lost. For example, you might need the key after an equipment failure.
11.7.6 Configuring the Identity Vault for the Identity Applications
The identity applications must be able to interact with the objects in your Identity Vault.
To improve the performance of the identity applications, the eDirectory Administrator should create value indexes for the manager, ismanager and srvprvUUID attributes. Without value indexes on these attributes, identity application users can experience impeded performance, particularly in a clustered environment.
You can create these value indexes automatically during installation by selecting Advanced > Create eDirectory Indexes in the RBPM Configuration utility. For more information about using Index Manager to create value indexes, see the NetIQ eDirectory Administration Guide.
11.7.7 Changing the Default Context Name for User Application
Instead of using the default context name, you can create a new context based on your organizational requirements. You can change the context name by performing the following actions:
-
Stop the Tomcat service by using the services.msc file.
-
Navigate to the User Application directory located in C:\NetIQ\idm\apps\UserApplication.
-
Launch the configupdate utility in GUI mode.
Ensure that the use_console option is set to false in configupdate.bat.properties file.
-
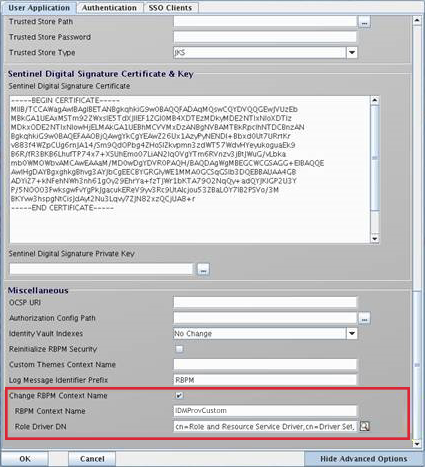
In the User Application tab, click Show Advanced Options and perform the following steps:
-
Select Change RBPM Context Name.
-
Specify the custom context name in RBPM Context Name. For example, IDMProvCustom.
-
Browse to and select the Roles Driver DN. For example, cn=Role and Resource Service Driver,cn=Driver Set,o=system.
-
Click OK.
-
-
Verify that the war file is renamed.
-
Navigate to the Tomcat webapps folder and check if IDMProvCustom.war entry is updated.
-
Navigate to ism-configuration properties file located in \TOMCAT_INSTALLED_HOME\conf and check if portal.context entry specifies the new context name.
-
-
Update your database with the new context name by using the update-context.bat file located in C:\NetIQ\idm\apps\UserApplication.
Execute the following command to run the update-context.bat file.
ua:C:\NetIQ\idm\apps\UserApplication # vi update-context.bat
You should see the following entries on your screen:
# copy and paste or execute this script before changing context name
# Substitute your new context where indicated
#
C:\NetIQ\idm\jre\bin\java -Xms256m -Xmx256m -Dwar.context.name=[New Context Here] -Ddriver.dn=[UA Driver DN] -jar C:\NetIQ\idm\apps\UserApplication\liquibase.jar --databaseClass=liquibase.database.core.PostgresDatabase --driver=org.postgresql.Driver --classpath= C:\NetIQ\idm\apps\postgres\postgresql-9.4.1212.jdbc42.jar: C:\NetIQ\idm\apps\tomcat\webapps\IDMProv.war --changeLogFile=UpdateProducerId.xml --url="jdbc:postgresql://localhost:5432/idmuserappdb?compatible=true" --contexts="prov,updatedb" --logLevel=debug --username=******** --password=******** update
For example, run the following script if you are using a PostgreSQL database:
C:\NetIQ\idm\apps\jre\bin\java -Xms256m -Xmx256m -Dwar.context.name=IDMProvCustom -Ddriver.dn= cn=Role and Resource Service Driver,cn=driverset1,o=system -jar C:\NetIQ\idm\apps\UserApplication\liquibase.jar --databaseClass=liquibase.database.core.PostgresDatabase --driver=org.postgresql.Driver --classpath= C:\NetIQ\idm\apps\postgres\postgresql-9.4.1212.jdbc42.jar: C:\NetIQ\idm\apps\tomcat\webapps\IDMProv.war --changeLogFile=UpdateProducerId.xml --url="jdbc:postgresql://<Database Server:5432/idmuserappdb?compatible=true" --contexts="prov,updatedb" --logLevel=debug -–username=dbadmin --password=******** update
where
-Dwar.context.name=IDMProvCustom specifies the new context.
-Ddriver.dn ="cn=User Application Driver,cn=driverset1,o=system" specifies the User Application driver DN.
--username=dbadmin specifies the database administrator username that can create database tables, views, and other artifacts.
IMPORTANT:Do not change the database driver details in the script for other supported databases.
-
Verify that the database tables have the new context name.
Table Name
Column to Check
PORTALPRODUCERS
producerid
PORTALPRODUCERREGISTRY
producerid
PORTALREGISTRY
producerid
PORTALPORTLETSETTINGS
producerid
PORTALPORTLETHANDLES
producerid
PROFILEGROUPPREFERENCES
elementid
For example, run the following SQL command to verify the new context name in the PORTALPRODUCERS table:
Select * from PORTALPRODUCERS;
The command should return only the new context name.
-
Start the Tomcat service by using the services.msc file.
11.7.8 Reconfiguring the WAR File for the Identity Applications
To update your WAR file for the identity applications, run the RBPM Configuration utility.
-
Run the utility in the install directory by executing configupdate.bat.
For more information about utility parameters, see Configuring the Settings for the Identity Applications.
-
Deploy the new WAR file to your application server.
For Tomcat single server, the changes are applied to the deployed WAR.
11.7.9 Configuring Forgotten Password Management
The Identity Manager installation includes Self Service Password Reset to help you manage the process for resetting forgotten passwords. Alternatively, you can use an external password management system.
Using Self Service Password Reset for Forgotten Password Management
In most cases, you can enable the forgotten password management feature when you install SSPR and the identity applications. However, you might not have specified the URL of the landing page for the identity applications to which SSPR forwards users after a password change. You might also need to enable forgotten password management. This section provides the following information:
Configuring Identity Manager to Use Self Service Password Reset
This section provides information about configuring Identity Manager to use SSPR.
-
Log in to the server where you installed the identity applications.
-
Run the RBPM configuration utility. For more information, see Running the Identity Applications Configuration Utility.
-
In the utility, navigate to Authentication > Password Management.
-
For Password Management Provider, specify SSPR.
-
Select Forgotten Password.
-
Navigate to SSO Clients > Self Service Password Reset.
-
For OSP client ID, specify the name that you want to use to identify the single sign-on client for SSPR to the authentication server. The default value is sspr.
-
For OSP client secret, specify the password for the single sign-on client for SSPR.
-
For OSP redirect URL, specify the absolute URL to which the authentication server redirects a browser client when authentication is complete.
Use the following format: protocol://server:port/path.For example, http://10.10.10.48:8180/sspr/public/oauth.
-
Save your changes and close the utility.
Configuring Self Service Password Reset for Identity Manager
This section provides information about configuring SSPR to work with Identity Manager. For example, you might want to modify the password policies and challenge response questions.
When you installed SSPR with Identity Manager, you specified a password that an administrator can use to configure the application. NetIQ recommends that you modify the SSPR settings, then specify an administrator account or group can configure SSPR. For more information about the configuration password, see Installing Password Management for Identity Manager.
-
Log in to SSPR by using the configuration password that you specified during installation.
-
In the Settings page, modify the settings for the password policy and challenge response questions. For more information about configuring the default values for SSPR settings, see Configuring Self Service Password Reset in the NetIQ Self Service Password Reset Administration Guide.
-
Lock the SSPR configuration file (SSPRConfiguration.xml). For more information about locking the configuration file, see Locking the SSPR Configuration.
-
(Optional) To modify SSPR settings after you lock the configuration, you must set the configIsEditable setting to true in the SSPRConfiguration.xml file.
-
Log out of SSPR.
-
For the changes to take effect, restart Tomcat.
Locking the SSPR Configuration
-
Go to http://<IP/DNS name>:<port>/sspr. This link takes you to the SSPR portal.
-
Log in to the Identity Manager with an administrator account or log in with your existing login credentials.
-
Click Configuration Manager at the top of the page and specify the configuration password that you specified during installation.
-
Click Configuration Editor and navigate to Settings > LDAP Settings.
-
Lock the SSPR configuration file (SSPRConfiguration.xml).
-
Under the Administrator Permission section, define a filter in LDAP format for a user or a group that has administrator rights to SSPR in the Identity Vault. By default, the filter is set to groupMembership=cn=Admins,ou=Groups,o=example.
For example, set it to uaadmin (cn=uaadmin) for the User Application administrator.
This prevents users from modifying the configuration in SSPR except the SSPR admin user who has full rights to modify the settings.
-
To ensure LDAP query returns results, click View Matches.
If there is any error in the setting, you cannot proceed to the next configuration option. SSPR displays the error details to help you troubleshoot the issue.
-
Click Save.
-
In the confirmation window that pops up, click OK.
When SSPR is locked, the admin user can see additional options in the Administration user interface such as Dashboard, User Activity, Data Analysis, and so on that were not available for him before SSPR lock down.
-
-
(Optional) To modify SSPR settings after you lock the configuration, you must set the configIsEditable setting to true in the SSPRConfiguration.xml file.
-
Log out of SSPR.
-
Log in to SSPR again as an admin user defined in Step 3.
-
Click Close Configuration, then click OK to confirm the changes.
-
For the changes to take effect, restart Tomcat.
Using the Legacy Provider for Forgotten Password Management
Instead of SSPR, you can use the legacy provider in Identity Manager for the Forgotten Password Management feature. If you choose the legacy provider, you do not need to install SSPR. However, you will need to reassign permissions for users to access the shared pages for password management. This section provides the steps to perform these activities:
For more information about shared pages and permissions, see Page Administration in the NetIQ Identity Manager - Administrator’s Guide to the Identity Applications.
Configuring the Legacy Provider for Forgotten Password Management
-
Log in to the server where you installed the identity applications.
-
Run the RBPM configuration utility. For more information, see Running the Identity Applications Configuration Utility.
-
In the utility, navigate to Authentication > Password Management.
-
For Password Management Provider, specify User Application (Legacy).
-
For Forgotten Password, specify Internal.
-
Navigate to SSO Clients > Self Service Password Reset.
-
For OSP redirect URL, the setting should be empty.
-
Save your changes and close the utility.
Reassigning Permissions for the Password Management Pages
The settings for the identity applications default to SSPR during installation. You must assign or reassign the permissions for the users, groups, or containers that you want to access the shared pages for managing passwords. When you assign users View permission for a container page or shared page, the users can access the page and see it in a list of available pages.
-
Ensure that Identity Manager is using the legacy provider. For more information, see Configuring the Legacy Provider for Forgotten Password Management.
-
Log in to the User Application as the application administrator. For example, log in as uaadmin.
-
Navigate to Administration > Page Admin.
-
In the Shared Pages panel, navigate to Password Management.
-
Select the page for which you want to specify permissions. For example, Change Password or Password Challenge Response.
-
In the right panel, click Assign Permission.
-
In View, select the users, groups, or containers that you want to assign to the page.
-
(Optional) To ensure that only an application administrator can access the specified page, select View Permission Set to Admin Only.
-
Click Save.
-
Perform Step 5 through Step 9 for each page that you want to configure.
-
Select the Home icon to return to the Dashboard.
-
Navigate to Applications, then select
 .
. -
On the Manage Applications page, replace the link to SSPR with the link for UserApp PwdMgt.
For more information, see Updating SSPR Links in the Dashboard for a Distributed or Clustered Environment and the Help for the Identity Applications.
-
Log out and then restart Tomcat.
Using an External System for Forgotten Password Management
To use an external system, you must specify the location of a WAR file containing Forgot Password functionality. This process includes the following activities:
Specifying an External Forgotten Password Management WAR File
If you did not specify this values during installation and want to modify the settings, you can use either the RBPM Configuration utility or make the changes in the User Application as an administrator.
-
(Conditional) To modify the settings in the RBPM Configuration utility, complete the following steps:
-
Log in to the server where you installed the identity applications.
-
Run the RBPM configuration utility. For more information, see Running the Identity Applications Configuration Utility.
-
In the utility, navigate to Authentication > Password Management.
-
For Password Management Provider, specify User Application (Legacy).
-
-
(Conditional) To modify the settings in the User Application, complete the following steps:
-
Log in as the User Application Administrator.
-
Navigate to Administration > Application Configuration > Password Module Setup > Login.
-
-
For Forgotten Password, specify External.
-
For Forgot Password Link, specify the link shown when the user clicks Forgot password on the login page. When the user clicks this link, the application directs the user to the external password management system. For example:
http://localhost:8180/ExternalPwd/jsps/pwdmgt/ForgotPassword.jsp
-
For Forgot Password Return Link, specify the link shown after the user finishes performing the forgot password procedure. When the user clicks this link, the user is redirected to the link specified. For example:
http://localhost/IDMProv
-
For Forgot Password Web Service URL, specify the URL for the web service that the external forward password WAR uses to call back to the identity applications. Use the following format:
https://idmhost:sslport/idm/pwdmgt/service
The return link must use SSL to ensure secure web service communication to the identity applications. For more information, see Configuring SSL Communication between Application Servers.
-
Manually copy ExternalPwd.war to the remote application server deploy directory that runs the external password WAR functionality.
Testing the External Forgot Password Configuration
If you have an external password WAR file and want to test the Forgot Password functionality by accessing it, you can access it in the following locations:
-
Directly, in a browser. Go to the Forgot Password page in the external password WAR file. For example, http://localhost:8180/ExternalPwd/jsps/pwdmgt/ForgotPassword.jsp.
-
On the User Application login page, click the link for Forgot password.
Configuring SSL Communication between Application Servers
If you use an external password management system, you must configure SSL communication between the Tomcat instances on which you deploy the identity applications and the External Forgotten Password Management WAR file. For more information, refer to the Tomcat documentation.
Updating SSPR Links in the Dashboard for a Distributed or Clustered Environment
The installation process assumes that you deploy SSPR on the same application server as the identity applications and Identity Reporting. By default, the built-in links on the Applications page in the Dashboard use a relative URL format that points to SSPR on the local system. For example, \sspr\private\changepassword. If you install the applications in a distributed or clustered environment, you must update the URLs for the SSPR links.
For more information, see the Help for the Identity Applications.
-
Log in as an administrator to the Dashboard. For example, log in as uaadmin.
-
Click Edit.
-
In the Edit Home Items page, hover on the item that you want to update, and then click the edit icon. For example, select Change My Password.
-
For Link, specify the absolute URL. For example, http://10.10.10.48:8180/sspr/changepassword.
-
Click Save.
-
Repeat for each SSPR link that you want to update.
-
Upon completion, click I’m done.
-
Log out, and then log in as a regular user to test the changes.