6.3 Deploying eDirectory Container
OS base image of the eDirectory Docker image is openSUSE Leap 15.4. eDirectory image archive file should be downloaded to the Docker Host machine. After downloading the archive file, it has to be extracted and then the image has to be loaded into the local Docker registry by using the following commands:
# tar -xvf eDirectory_92x_Container.tar.gz # docker load --input eDirectory_92x/eDirectory_92x.tar.gz
The above command will load a Docker image named edirectory:9.2.x.
eDirectory Docker container accepts all parameters of the ndsconfig utility with the Docker Run command. For information on ndsconfig utility, see, Using the ndsconfig Utility to Add or Remove the eDirectory Replica Server.
NOTE:Setting the password using -w option of the ndsconfig utility in the Docker Run command is not recommended. Password set using this option can be viewed in plain-text using Docker inspect command. Specifying the admin FDN and admin password in the prompt is a more secure way of configuring the admin credential.
eDirectory Docker container uses default values for the following ndsconfig parameters. Hence, you should not configure these parameters in the Docker run command:
-
Configuration File: /config/eDirectory/inst/conf/nds.conf
-
Instance Location: /config/eDirectory/inst/data/data
-
DIB Location: /config/eDirectory/inst/data/data/dib
NOTE:It is important that the instance data and configuration is populated under the /config folder of the container. This is to enable persistent storage and upgrade functionality of eDirectory containers. For more information, see Managing eDirectory Data Storage.
The default log file location of the eDirectory container is /config/eDirectory/inst/data/log.
Before deploying eDirectory, you must consider the following recommendations:
-
Docker containers do not have any resource constraints by default. This provides every container with the access to all the CPU and memory resources provided by the host’s kernel. You must also ensure that one running container should not consume more resources and starve other running containers by setting limits to the amount of resources that can be used by a container.
-
Docker container should ensure that a Hard Limit is applied for the memory used by the container using the --memory flag on Docker run command.
-
Docker container should ensure that a limit is applied to the amount of CPU used by a running container using the --cpuset-cpus flag on the Docker run command.
-
-
--pids-limit should be set to 300 to restrict the number of kernel threads spawned inside the container at any given time. This is to prevent DoS attacks.
-
You must set the container restart policy to on-failure with number of retries as 5 using the --restart flag on Docker run command. Containers will have to be manually restarted if the Docker daemon on the host machine gets restarted.
-
You must only use the eDirectory container once the health status shows as healthy after the container comes up. To check the container’s health status, run the following command:
docker ps --filter status="running"
-
Docker containers usually have a default list of Linux capabilities enabled. You must ensure to keep only the following capabilities enabled for eDirectory container and drop the others:
-
AUDIT_WRITE
-
CHOWN
-
DAC_OVERRIDE
-
SETGID
-
SETUID
-
NET_BIND_SERVICE
-
SYS_CHROOT (Only if enabling SLP service)
-
SYS_PTRACE (Only if using utilities that make use of Linux ptrace. Such as gdb)
For more information on how to add and drop capabilities, see Runtime privilege and Linux capabilities.
-
-
eDirectory container will always start as non-root user (nds). As an additional security measure, enable user namespace remapping on the daemon to prevent privilege-escalation attacks from within the container. For more information on user namespace remapping, see Isolate containers with a user namespace.
-
You must set the --stop-timeout option in the Docker run command with a value of 180. This is to make sure that the nds service gets enough time to shutdown gracefully.
NOTE:If you are using any previous version of standalone eDirectory, you will not be able to migrate your setup to the Docker environment using eDirectory 9.2 Docker container.
eDirectory Docker container supports Host and Overlay network drivers for deployment in a multi-host Docker environment:
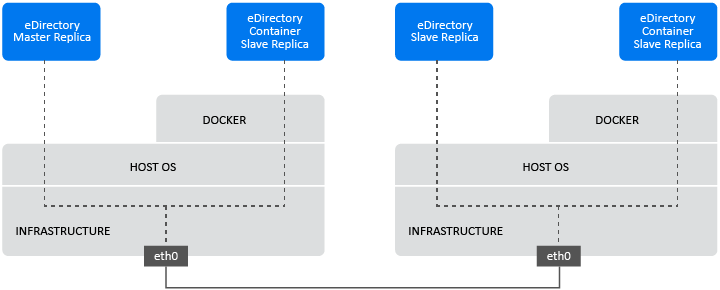
6.3.1 Deploying eDirectory Container in Host Network
eDirectory containers can be deployed in a Hybrid environment using the Host network driver only on Linux. For information on Docker networks, see Configure Networking.
NOTE:Host Network is not supported on Windows.
A Hybrid environment is a combination of both legacy and container based deployments of eDirectory servers in the same tree. A Hybrid network enables a seamless introduction of eDirectory Docker containers to an existing production environment that is already hosting a legacy eDirectory deployment. In Docker Host networking, service ports cannot be re-used as the network stack of the host is shared by both legacy and containerized eDirectory deployments. Also, a containerized eDirectory server will appear as a legacy eDirectory server to clients and other servers in the tree.
The following example shows, how to create a new tree using eDirectory container without enabling EBA:
docker run -it --name eDir-container-1 --stop-timeout 180 --restart on-failure:5 --memory="700M" --cpuset-cpus="1" --pids-limit="300" --volume eDir-volume1:/config --network=host edirectory:9.2.0 new -t docker-tree1 -n novell -S m1 -B 164.99.1.1@1524 -o 1028 -O 1030 -L 1389 -l 1636 --configure-eba-now no
The following example shows, how to add an eDirectory container replica server to an existing tree without enabling EBA:
docker run -it --name eDir-container-2 --stop-timeout 180 --restart on-failure:5 --memory="700M" --cpuset-cpus="1" --pids-limit="300" --volume eDir-volume2:/config --network=host edirectory:9.2.0 add -t docker-tree1 -n novell -S m2 -B 164.99.10.10@2524 -o 2028 -O 2030 -L 2389 -l 2636 --configure-eba-now no -p 164.99.1.1@1524
The following example shows, how to create a new tree using eDirectory container enabling EBA:
docker run -it --name eDir-container-1 --stop-timeout 180 --restart on-failure:5 --memory="700M" --cpuset-cpus="1" --pids-limit="300" --volume eDir-volume1:/config --network=host edirectory:9.2.0 new -t docker-tree1 -n novell -S m1 -B 164.99.1.1@1524 -o 1028 -O 1030 -L 1389 -l 1636 --configure-eba-now yes
The following example shows, how to add an eDirectory container replica server to an existing tree enabling EBA:
docker run -it --name eDir-container-2 --stop-timeout 180 --restart on-failure:5 --memory="700M" --cpuset-cpus="1" --pids-limit="300" --volume eDir-volume2:/config --network=host edirectory:9.2.0 add -t docker-tree1 -n novell -S m2 -B 164.99.10.10@2524 -o 2028 -O 2030 -L 2389 -l 2636 --configure-eba-now yes -p 164.99.1.1@1524
NOTE:
-
--network flag is used to deploy the container using the Host networking driver.
-
Port numbers of services should not be repeated across eDirectory containers running on the same Docker host.
-
IP addresses used in the above commands are of the Docker host machine where the container is supposed to run.
Figure 6-1 Deploying eDirectory Container in Host Network
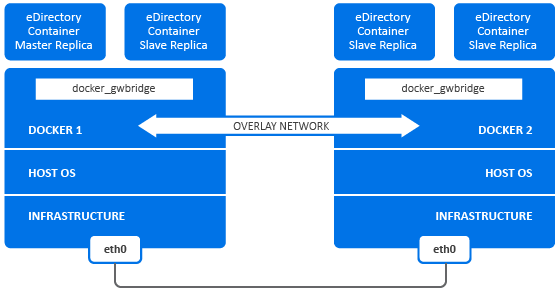
6.3.2 Deploying eDirectory Container in User Defined Overlay Network
A User Defined Overlay network can be used to create a distributed network of eDirectory containers running on multiple Docker daemon hosts. eDirectory container in user defined overlay network can be deployed in both Linux and Windows. Docker Swarm service should be used to join the Docker hosts to a Swarm, so that eDirectory containers running on them can communicate seamlessly. For more information on Docker Overlay network driver, see Use Overlay Networks.
NOTE:Scaling and scheduling functions of a Docker swarm is not certified with eDirectory containers. Migration of eDirectory containers across hosts by Swarm service is not also supported.
Prerequisites
-
A Docker swarm should be created with at least one Docker host configured as manager and the other hosts as workers.
-
Create an attachable Overlay network called myOverlay.
-
Open the following ports on the firewall between Docker hosts for cluster management and communication within a Docker Swarm:
-
TCP port 2377
-
TCP and UDP port 7946
-
UDP port 4789
-
-
Containers deployed in Overlay network should be assigned a static internal IP address that belongs to the myOverlay subnet.
For information on how to deploy a Swarm and create a user defined Overlay network, see Networking with overlay networks.
Before deploying eDirectory container in a user defined Overlay network, you must consider the following recommendations:
-
eDirectory container master replica server and it’s R/W replicas must be deployed within the same Overlay network. Communication with other standalone eDirectory servers or containers running outside the Overlay network will not be supported.
-
It is recommended to deploy the iManager Docker container within the same user defined Overlay network for administering eDirectory. For more information on how to deploy iManager Docker containers, see Deploying iManager Using Docker Container.
-
You can find the network details of the user defined overlay network by running the following command:
docker inspect myOverlay
The following command shows how to create a new tree using eDirectory container without enabling EBA:
docker run -it --name eDir-container-1 --stop-timeout 180 --restart on-failure:5 --memory="700M" --cpuset-cpus="1" --pids-limit="300" --volume eDir-volume1:/config --network=myOverlay --ip=10.0.0.5 edirectory:9.2.0 new -t docker-tree1 -n novell -S m1 –B @524 -o 8028 -O 8030 -L 389 -l 636 --configure-eba-now no
The following command shows how to create a new tree using eDirectory container enabling EBA:
docker run -it --name eDir-container-1 --stop-timeout 180 --restart on-failure:5 --memory="700M" --cpuset-cpus="1" --pids-limit="300" --volume eDir-volume1:/config --network=myOverlay --ip=10.0.0.5 edirectory:9.2.0 new -t docker-tree1 -n novell -S m1 –B @524 -o 8028 -O 8030 -L 389 -l 636 --configure-eba-now yes
The following command shows how to obtain the IP Address of the eDirectory container created above:
docker inspect eDir-container-1 --format {{.NetworkSettings.Networks.myOverlay.IPAddress}}
The displayed IP Address can be used as the remote_IP_Address while adding an eDirectory container replica server to the Tree.
The following command shows how to add an eDirectory container replica server to an existing tree without enabling EBA:
docker run -it --name eDir-container-2 --stop-timeout 180 --restart on-failure:5 --memory="700M" --cpuset-cpus="1" --pids-limit="300" --volume eDir-volume2:/config --network=myOverlay --ip=10.0.0.6 edirectory:9.2.0 add -t docker-tree1 -n novell -S m2 –B @524 -o 8028 -O 8030 -L 389 -l 636 --configure-eba-now no -p <remote_IP_Address>
The following command shows how to add an eDirectory container replica server to an existing tree enabling EBA:
docker run -it --name eDir-container-2 --stop-timeout 180 --restart on-failure:5 --memory="700M" --cpuset-cpus="1" --pids-limit="300" --volume eDir-volume2:/config --network=myOverlay --ip=10.0.0.6 edirectory:9.2.0 add -t docker-tree1 -n novell -S m2 –B @524 -o 8028 -O 8030 -L 389 -l 636 --configure-eba-now yes -p <remote_IP_Address>
NOTE:
-
--network flag is used to deploy the container in the user-defined Overlay network called myOverlay using the Overlay network driver.
-
In the above examples, --ip flag is used to assign a static internal IP address to the container that belongs to myOverlay subnet.
-
-B @524 option will allow the NCP, http and https services to bind to all the available interfaces.
Figure 6-2 Deploying eDirectory Container in User Defined Overlay Network