5.2 Deployment Procedure
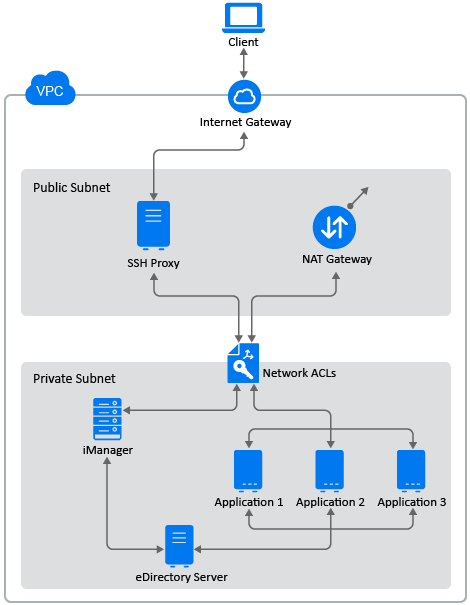
eDirectory should be deployed only in a private subnet in Amazon VPC. Figure 4-1 illustrates a sample deployment that is used in the subsequent sections.
Figure 5-1 eDirectory Deployment on AWS EC2
NOTE:
-
SSH Proxy is bastion host in the public subnet to which the administrator connects using SSH and connects to other instances in the private subnet using the SSH agent forwarding.
-
Applications that need to access eDirectory should be deployed in the private subnet. If these applications need to be accessed from the Internet, configure an AWS EC2 load balancer in the public subnet to enable the access. For more information, see Create an Application Load Balancer.
The deployment procedure consists of the following steps:
5.2.1 Preparing AWS Virtual Private Cloud
This section outlines general steps to configure AWS VPC to use with eDirectory. For more information, see the Amazon Elastic Compute Cloud Documentation.
Perform the following steps to create AWS VPC services:
-
Log in to the AWS Management Console.
-
Create the following services:
Service
Description
VPC
You can create a VPC using the Amazon VPC console. For more information on how to create a VPC, see Creating a VPC.
For more information on the overview of VPC, see the Amazon Virtual Private Cloud Documentation.
IMPORTANT:Creating a VPC using Start VPC Wizard creates two Subnets, Internet gateways, and Route table and NAT gateway for the VPC. You can view or edit these items as follows:
Subnets
As part of the VPC creation, two subnets will be created; a public and a private subnet. eDirectory should be deployed in the private subnet. As shown in Figure 4-1, any application which is accessing eDirectory, should be deployed in the same private subnet. SSH access to the instances in the private subnet should be done via SSH proxy in the public subnet. For more information, see VPC and Subnet.
Internet gateways
Internet gateway is required to enable SSH connection to SSH proxy as shown in Figure 4-1. For more information to create and attach Internet gateways with VPC, see Internet Gateways.
Route table
For more information to create a route table, see Route Tables.
NAT gateway
NAT gateway is required for those instances which are in the private subnet to download operating system updates. For more information to create a NAT gateway, see NAT Gateways.
Elastic IP address
Elastic IP addresses are public static IP addresses which should be assigned to the instance running SSH proxy and NAT gateway. For more information to create Elastic IP address, see Working with Elastic IP Addresses.
5.2.2 Configuring Network ACLs
A network access control list (ACL) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets. For more information, see Network ACLs.
This section outlines the rules to create network ACLs in the private subnet. Configure the following rules for network ACLs in the private subnet:
-
Inbound Rules:
Table 5-1
Rule
Type
Port Range
Source
Action
Description
10
SSH
TCP 22
<SSH Proxy IP Address>/32
ALLOW
Allows inbound SSH traffic from your SSH proxy IP address in public subnet
15
HTTPS
TCP 8443
<SSH Proxy IP Address>/32
ALLOW
Allows inbound HTTPS traffic from the SSH proxy IP address in public subnet
20
Custom TCP Rule
TCP 32768-65535
0.0.0.0/0
ALLOW
Allows inbound return traffic from hosts on the Internet that are responding to requests originating in the subnet
*
All Traffic
All
0.0.0.0/0
DENY
Denies all inbound IPv4 traffic not already handled by a preceding rule (not modifiable)
-
Outbound Rules:
Table 5-2
Rule
Type
Port Range
Destination
Action
Description
10
Custom TCP Rule
TCP 32768-65535
<SSH Proxy IP Address>/32
ALLOW
Allows outbound SSH traffic from the private subnet to SSH proxy in the public subnet
12
Custom TCP Rule
TCP 32768-65535
<SSH Proxy IP Address>/32
ALLOW
Allows outbound traffic for accessing iManager from the public subnet
15
HTTPS
TCP 443
0.0.0.0/0
ALLOW
Allows outbound HTTPS traffic from the private subnet to the Internet
20
HTTP
TCP 80
0.0.0.0/0
ALLOW
Allows outbound HTTP traffic from the private subnet to the Internet
25
HTTPS
Port number to which the auditing server is listening
<IP Address of the audit server>
ALLOW
Allow auditing eDirectory events.
NOTE:This rule is applicable only when the audit server is outside the private subnet.
*
All Traffic
All
0.0.0.0/0
DENY
Denies all outbound IPv4 traffic not already handled by a preceding rule (not modifiable)
5.2.3 Configuring Security Groups
A security group is a set of virtual firewall rules which can be assigned to one or more instances in the VPC.
By default, a new security group only allows incoming traffic on port 22, so that you can only connect to the instance by using SSH.
For more information, see Amazon EC2 Security Groups for Linux Instances.
To deploy eDirectory on AWS, create three security groups. For example Security Group 1, Security Group 2 and Security Group 3. Create these security groups with the following port rules:
-
Security Group 1 (for eDirectory):
Port
Source
Description
TCP 22
Public subnet
Allows SSH traffic from public subnet
TCP 636
Private subnet
Allows LDAPS traffic in private subnet
TCP 524
Private subnet
Allows NCP traffic for eDirectory in private subnet
UDP 427
Private Subnet
Allows SLP traffic in the private subnet
NOTE:LDAP port 389 should not be enabled on the security group which is assigned to eDirectory. HTTP port should only be enabled on the security group assigned to eDirectory server hosting the tree CA.
-
Security Group 2 (for eDirectory):
Port
Source
Description
TCP 8028
VPC
Required for accessing the eDirectory tree CRL from the VPC when there are services in the VPC which are configured with certificates issued by tree CA. This security group is assigned to the eDirectory server hosting the tree CA.
-
Security Group 3 (for iManager):
Port
Source
Description
TCP 22
Public subnet
Allows SSH traffic from public subnet
TCP 8443
Public subnet
Allows HTTPS traffic for accessing iManager from public subnet
5.2.4 Creating a SSH Key Pair
You must create a SSH key pair before configuring the Amazon EC2 instances. To create a key pair, perform the following steps:
-
Create a 4096-bit RSA SSH key pair on your client using the following command:
ssh-keygen -t rsa -b 4096
ssh-keygen places the newly created public key at ~/.ssh/id_rsa.pub.
-
Import the SSH public key to your Amazon EC2 account. For more information, see Importing Your Own Public Key to Amazon EC2.
IMPORTANT:You can connect to and manage your instances only using the SSH private key. Therefore, do not lose the SSH private key.
5.2.5 Creating and Deploying Instances
Create and launch your EC2 instances on one of the supported platforms. For more information on how to create and launch instances, see Create Your EC2 Resources and Launch Your EC2 Instance. As a part of creating and launching the instances, you must also perform the following steps:
-
Associate Security Group 1 with the instances where first eDirectory server will be configured, Security Group 2 with the instance where all other eDirectory servers will be configured and Security Group 3 with the instance where iManager will be configured. For more information about security groups, see Configuring Network Security Groups for Virtual Machine.
-
Associate the public key created in section Creating a SSH Key Pair with your instances.
5.2.6 Configuring EBS Volume for Storing eDirectory Data
Configuring EBS volume is required to prevent loss of eDirectory data and configuration in case of EC2 instance crash. For more information on recovering eDirectory data and configuration, see Disaster Recovery. After creating the EC2 instance, perform the following steps to prepare the instance for deploying eDirectory:
-
Create an EBS volume, perform the steps in Creating an Amazon EBS Volume.
-
Associate the EBS volume with the EC2 instance. For more information, see Attaching an Amazon EBS Volume to an Instance
-
Login to the instance, format the EBS volume with ext4 file system and mount the EBS volume. For more information on how to format and mount the EBS volume, see Making an Amazon EBS Volume Available for Use on Linux.
-
Bind mount directories from the EBS volume to eDirectory data/NICI data directories. Perform the following steps as root user to bind mount:
-
Create eDirectory data directory by using the following command:
mkdir <mount_point>/eDirectory_data
-
Create NICI data directory by using the following command:
mkdir <mount_point>/nici_data
-
Create NICI and eDirectory configuration directories by using the following command:
mkdir <mount_point>/eDirectory_nici_conf
-
Create required directories for eDirectory by using the following commands:
mkdir –-parents /var/opt/novell/eDirectory mkdir –-parents /var/opt/novell/nici mkdir –-parents /etc/opt/novell/eDirectory
-
To bind mount the directories, add the following to /etc/fstab:
<mount_point>/eDirectory_data /var/opt/novell/eDirectory none defaults,bind 0 0
<mount_point>/nici_data /var/opt/novell/nici none defaults,bind 0 0
<mount_point>/eDirectory_nici_conf /etc/opt/novell/eDirectory none defaults,bind 0 0
NOTE:All operations in the instance should be performed as a root user.
-
5.2.7 Installing eDirectory and iManager
Prerequisites
-
Ensure that you meet the requirements listed in System Requirements.
-
Create security groups as mentioned in Configuring Network Security Groups for Virtual Machine.
-
SSH proxy instance should be hardened and secured server. Open only SSH port 22 for this instance and select an AWS instance type with good performance and memory. SSH private key required for accessing instances in the private subnet and the instance where SSH proxy is running, should not be stored in the VPC but on the client only. Associate an Elastic IP address to the SSH Proxy server to have static public IP address.
-
Configure the VNC server in the SSH Proxy instance. VNC server should be hardened with a password of good strength. Connect to the VNC server through an SSH tunnel only to allow a secured communication. VNC server should be configured to listen only for connections from the localhost. Disable screen lock to avoid session lockout. After using the VNC server, you should terminate the session.
-
Connect to the instance in the private subnet where eDirectory/iManager will be configured using SSH proxy:
ssh -i edir_key.pem -A -J ec2-user@<ssh_proxy_ip> ec2-user@<instance_private_ip>
NOTE:
-
in above sample commands, edir_key.pem is a sample file name containing the server key.
-
You can also add the identity file in the agent using the SSH-Add command to avoid using identity file every time you login.
To view the private IP address of an instance, click Instances > [instance] > Description.
-
-
Configure an SLP Directory Agent (DA) server in a VM in the Backend subnet. Open port 427 in the inbound rule of NSG for the VM where SLP DA is deployed. Enable DA operation by editing the slp.conf file. For more information, see Configuring OpenSLP for eDirectory in the NetIQ eDirectory Administration Guide.
Installation and Configuration Procedure
This section explains the step by step instructions to install and configure eDirectory and iManager in an AWS EC2 environment. Once eDirectory is installed, you should ensure that the following conditions are met:
-
EBA is enabled
-
SNMP is disabled
-
eDirectory is not listening on port 389
-
LDAP and HTTP services are configured to use ECDSA certificates only
-
Access to the SSH port of the AWS EC2 private instance should be disabled when not in use.
-
Disable iMonitor, eMBox and DHost modules to provide additional security. After disabling them, all activities involving these modules should be performed using the NDS utilities only.
Installing & Configuring eDirectory
-
Copy the eDirectory_<version>_Linux_x86_64.tar.gz file using Secure Copy (scp) to the instance in the private subnet where eDirectory will be configured using SSH proxy:
scp -i <keyname> -o ProxyJump=ec2-user@<ssh_proxy_ip> eDirectory_<version>_Linux_x86_64.tar.gz ec2-user@<instance_ip>:/<directory> -
Install eDirectory. For more information, see Using the nds-install Utility to Install eDirectory Components.
-
Configure eDirectory. For more information, see Using the ndsconfig Utility to Add or Remove the eDirectory Replica Server. For example, here’s a sample command for installing and configuring eDirectory:
ndsconfig new [-t <tree_name>] [-n <server context>] -a <admin FDN> [-w <admin password>] -P ldaps://<instance_ip> --configure-eba-now yes -
Install openslp-server and start the SLPD service.
Installing & Configuring iManager
Using the iManager administrative console, you can manage the eDirectory operations on your AWS environment. iManager should be installed on your AWS instance after installing eDirectory.
-
Copy the iMan_<version>_linux_x86_64.tgz file using Secure Copy (scp) to the instance in the private subnet where iManager will be configured using SSH proxy:
scp -i <keyname> -o ProxyJump=ec2-user@<ssh_proxy_ip> iMan_<version>_linux_x86_64.tgz ec2-user@<instance_ip>:/<directory> -
Install and configure iManager. For more information, see Installing iManager Server on Linux. Before installing iManager, see the system requirements in System Requirements section in the iManager Installation Guide.
-
Download the EBA CA certificate on the instance where iManager is running. For more information, see Managing the EBA CA by Using iManager in the NetIQ eDirectory Administration Guide.
-
Replace the Self-Signed certificates in the VM running iManager with a secure CA signed certificates. For more information, see Replacing the Temporary Self-Signed Certificates for iManager.
NOTE:Ensure to configure the iManager server to use ECDSA certificates only. After installing iManager, specify an authorized user and the appropriate eDirectory tree name that this user will manage.
Launching iManager
Perform the following steps to launch iManager:
-
Connect to the VNC server running on localhost of the SSH Proxy through SSH tunnel.
-
Install and launch a browser in the same instance.
-
Launch iManager and connect to the eDirectory tree using the IP address or the tree name.
Post-Configuration Tasks
-
To check if EBA is enabled, see Viewing Information About EBA in the NetIQ eDirectory Administration Guide.
-
Enable Suite B on Certificate Server. For more information, see Enabling Suite B on the Certificate Serverin the NetIQ eDirectory Administration Guide.
-
Configure AES 256-bit tree key for the first eDirectory server. For more information, see Creating an AES 256-Bit Tree Key in the NICI Administration Guide.
-
Delete the CRL distribution points in the first eDirectory server. As non-secured LDAP access over port 389 is disabled on all eDirectory servers, the CRL for the tree CA should be available for download over HTTP only. Perform the following steps to delete the CRL distribution points:
-
Login to iManager as Administrator.
-
Go to Roles & Tasks > NetIQ Certificate Server > Configure Certificate Authority.
-
Click CRL.
-
Click One. Select and delete all CRL Distribution Points except the HTTP CRL Distribution Point (http://<instance_ip>:8028/crl/one.crl).
-
Click Apply and then click Close.
-
Click OneEC. Select and delete all CRL Distribution Points except the HTTP CRL Distribution Point (http://<instance_ip>:8028/crl/oneec.crl).
-
Click Apply and then click OK.
-
-
Repair the server’s default certificates using the iManager certificate server plug-in. To repair the default certificates, perform the following steps:
-
Login to iManager as Administrator.
-
Go to Roles & Tasks > NetIQ Certificate Server > Repair Default Certificates.
-
Select the server(s) which owns the certificates and click Next.
-
Select Yes All Default Certificates will be overwritten and click Next.
-
Review the tasks to be performed and select Finish.
-
-
Configure LDAP and HTTP services to use ECDSA Certificates and Suite B ciphers. For more information, see Configuring LDAP and HTTP Services to Use ECDSA Certificates and Suite B Ciphers in the NetIQ eDirectory Administration Guide. Once done, restart eDirectory.
-
For more information to check if SNMP sub-agent is unloaded, see Loading and Unloading the SNMP Server Module in the NetIQ eDirectory Administration Guide.
-
Ensure that eDirectory is not listening on port 389.
-
Disable iMonitor, embox, DHost and HTTP stack.
-
Perform the following steps to disable iMonitor, embox and DHost in the eDirectory server hosting the tree CA:
-
Edit the ndsmodules.conf file by commenting hconserv, imon and embox.
-
Restart eDirectory.
-
-
Perform the following steps to disable the HTTP stack in the eDirectory replica servers:
-
Edit the ndsmodules.conf file by commenting httpstk, hconserv, imon and embox.
-
Restart eDirectory.
NOTE:httpstk should be placed above nds in the ndsmodules.conf file before commenting. This stops nds module from enabling HTTP stack.
-
-
-
Configure SLP to force eDirectory to use unicast as advertising method. Edit the slp.conf file by providing the IP address of the DA server in the Backend subnet. For more information, see Configuration Parameters in the NetIQ eDirectory Administration Guide.
NOTE:Once all eDirectory instances and iManager have been configured, configure the network ACL of the AWS private subnet to deny access to the SSH port and allow it only when required.
5.2.8 Deploying Auditing Services
You can deploy the Common Event Format (CEF) auditing service on AWS EC2 to audit various eDirectory events. Perform the following steps to deploy CEF auditing services:
-
Install an auditing server in the VPC.
-
Configure the auditing server to listen on a port
NOTE:We recommend you to use Sentinel as your auditing server.
-
Create a new security group with the following configuration and associate with the instance where the audit server is running:
Port
Source
Description
TCP (Auditing server port)
Private subnet
Allows receiving events from eDirectory servers
-
Update the following in /etc/opt/novell/eDirectory/conf/auditlogconfig.properties file on all the eDirectory instances:
log4j.appender.S.Host=<Auditing server ip> log4j.appender.S.Port=<auditing server port>
-
Enable the corresponding CEF events from iManager. For more information, see Configuring the CEF Events for Auditing. Enabled events will be forwarded to the auditing server.
5.2.9 Disaster Recovery
Disaster recovery is performed in case of an instance crash where eDirectory was running. Perform the following steps for disaster recovery:
-
Stop the instance which has crashed and dissociate the EBS volume from it. For more information, see Detaching an Amazon EBS Volume from an Instance.
-
Configure a new EC2 instance with the same operating system as the instance which has crashed.
-
Install the same version of eDirectory in the new EC2 instance.
-
Attach the EBS volume to the new instance and mount the file system. For more information, see Attaching an Amazon EBS Volume to an Instance.
-
Bind mount the directories.
To bind mount the directories, update the following in /etc/fstab:
<mount_point>/eDirectory_data /var/opt/novell/eDirectory none defaults,bind 0 0
<mount_point>/nici_data /var/opt/novell/nici none defaults,bind 0 0
<mount_point>/eDirectory_nici_conf /etc/opt/novell/eDirectory none defaults,bind 0 0
-
Change the IP address in /etc/opt/novell/eDirectory/conf/nds.conf to current instance IP address.
-
Upgrade eDirectory skipping health check. For more information, see Upgrading eDirectoryin the NetIQ eDirectory Installation Guide.
-
Repair the network addresses using ndsrepair utility. For more information, see DSRepair Options in the NetIQ eDirectory Administration Guide.
-
Modify the CRL distribution point IP address if the tree CA IP address is changed. For more information on how to change the IP address, see Viewing and Modifying a CRL Configuration Object's Properties in the NetIQ eDirectory Administration Guide.
-
Repair the server’s default certificates using the iManager certificate server plug-in. To repair the default certificates, perform the following steps:
-
Login to iManager as Administrator.
-
Go to Roles & Tasks > NetIQ Certificate Server > Repair Default Certificates.
-
Select the server(s) which owns the certificates and click Next.
-
Select Yes All Default Certificates will be overwritten and click Next.
-
Review the tasks to be performed and select Finish.
-
-
Configure LDAP and HTTP services to use new ECDSA Certificates.