16.1 Enabling Suite B in a New Installation
Figure 16-1 shows the sequence of tasks for enabling Suite B on eDirectory components in a new installation.
Figure 16-1 Enabling Suite B in a New Installation
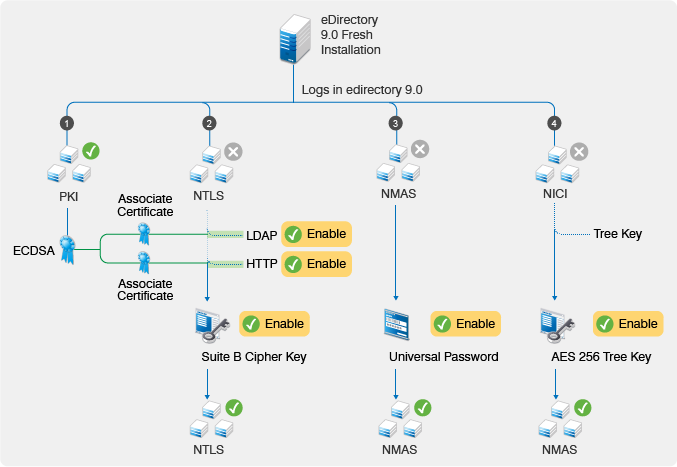
16.1.1 Enabling Suite B on the Certificate Server
When you configure a new tree, the Certificate Server creates a self-signed ECDSA certificate on P-384 curve for the tree Certificate Authority (CA) in addition to the traditional RSA certificates. If you add new servers to the tree or upgrade old servers to eDirectory 9.0, the Certificate Server issues the ECDSA certificates to these servers.
NOTE:By default, NetIQ Certificate Server creates the ECDSA certificates on P-384 curve. However, you can also create server certificates on P-256 curve.
It is possible to use only the ECDSA certificates without enabling Suite B. Enabling Suite B is an additional step for adhering to RFC 5759.
To configure the CA Certificate Server to operate in the Suite B mode, perform the following steps:
-
Configure Enhanced Background Authentication for the CA Certificate Server.
For more information, see Enabling Background Authentication.
-
Launch iManager.
-
Log in to the eDirectory tree as an administrator with the appropriate rights.
-
On the Roles and Tasks menu, click NetIQ Certificate Server > Configure Certificate Authority.
-
Select Enable Suite B Mode.
-
Click OK.
When the CA Certificate Server is in Suite B mode, the CA does not allow you to create RSA certificates. Also, server self-provisioning does not generate RSA certificates any longer. If you plan to add new servers, ensure that the servers are configured to run Enhanced Background Authentication.
When all servers in the tree or any external services connecting to the tree start using the ECDSA server certificates, you can revoke and delete the RSA certificates because they are not needed any more.
NOTE:The Follow CA's Algorithm feature that was introduced in eDirectory 8.8.8 Patch 6 is no longer available with eDirectory 9.0. Instead, eDirectory 9.0 servers use SHA-256 algorithm for RSA certificates and SHA-384 for ECDSA certificates by default.
16.1.2 Configuring LDAP and HTTP Services to Use ECDSA Certificates and Suite B Ciphers
NetIQ Transport Layer Security (NTLS) supports TLS 1.2 and Suite B cryptographic algorithms through the FIPS compliant OpenSSL module. The FIPS compliant OpenSSL module is used by eDirectory components such as LDAP, httpstk (iMonitor), and NCP engine. For more information, see Operating eDirectory in FIPS Mode in the NetIQ eDirectory Installation Guide.
Before enabling a Suite B mode on a server, ensure that the server has ECDSA certificates and LDAP clients, LDAP browsers, and web browsers in the eDirectory environment support TLS 1.2, ECDSA certificates, and Suite B ciphers. To configure LDAP and HTTPS interfaces in a Suite B mode, enable the interfaces with the desired Suite B mode and associate an appropriate ECDSA server certificate to them. Repeat this procedure for each eDirectory server in the tree. To view the cipher level and ECDSA server certificate for a server, use the server's LDAP and httpstk configuration objects: ldapServer and httpServer.
To configure the LDAP server in Suite B mode:
-
Log in to the eDirectory tree as an administrator with the appropriate rights.
-
On the Roles and Tasks menu, click LDAP > LDAP Options > View LDAP Servers and select the LDAP server object you want to configure in Suite B mode.
-
Click Connections.
-
In the Server Certificate parameter, browse to and click the Elliptic Curve certificate that you want to use with the LDAP server object.
-
Depending on the Suite B mode that you want to enable for the LDAP server object, select a value from the Bind Restrictions for Cipher drop-down list.
Bind Restrictions for Cipher
Cipher Suite
Description
Use SuiteB Cipher (128-bit)
-
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
-
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
Enables Suite B mode operation by using 128-bit level of security. When you select this option, eDirectory permits both 128-bit and 192-bit level of security by peers (any LDAP clients). You can use either ECDSA 256 or ECDSA 384 certificate with this option.
Use SuiteB Cipher (128-bit only)
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
Enables Suite B mode operation by using 128-bit level of security. When you select this option, eDirectory does not allow 192-bit level of security by peers (any LDAP clients).
All certificates in a certificate chain should use ECDSA keys on P-256 curve. This is mandatory for servers and applicable for clients if client certificate validation is enabled.
Use SuiteB Cipher (192-bit)
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
Enables Suite B mode operation by using 192-bit level of security. When you select this option, eDirectory permits only 192-bit level of security by peers (any LDAP clients).
All certificates in a certificate chain should use ECDSA keys on P-384 curve. This is mandatory for servers and applicable for clients if client certificate validation is enabled.
eDirectory allows you to use combination values of ldapbindrestrictions and cipher levels. For more information, see Table 14-1.
-
-
Click Apply, then click OK.
-
For the changes to take effect, do one of the following:
-
Restart eDirectory.
-
Unload and load the LDAP server.
-
To configure the HTTPS interface in Suite B mode:
-
Log in to the eDirectory tree as an administrator with the appropriate rights.
-
On the Roles and Tasks menu, click Directory Administration > Modify Object.
-
Select the http server object you want to modify, or browse to and click the http server object you want to view.
-
Click OK.
-
Click the Other tab, then select httpBindRestrictions from the Valued Attributes list.
-
Click Edit.
-
Depending on the Suite B mode that you want to enable for the http server object, change the value to 4,5, or 6 in the dialog that displays.
Bind Restrictions for Cipher
Cipher Suite
Description
4 - Use SuiteB Cipher (128-bit)
-
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
-
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
Enables Suite B mode operation by using 128-bit level of security (Suite B Cipher 128-bit). When you select this option, eDirectory permits both 128-bit and 192-bit level of security by clients (web browsers). You can use either ECDSA 256 or ECDSA 384 certificate with this option.
5 - Use SuiteB Cipher (128-bit only)
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
Enables Suite B mode operation by using 128-bit level of security (Suite B Cipher 128-bit only). When you select this option, eDirectory does not allow 192-bit level of security by clients (web browsers).
All certificates in a certificate chain should use ECDSA keys on P-256 curve. This is mandatory for servers and applicable for clients if client certificate validation is enabled.
6 - Use SuiteB Cipher (192-bit)
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
Enables Suite B mode operation by using 192-bit level of security (Suite B Cipher 192-bit). When you select this option, eDirectory permits only 192-bit level of security by clients (web browsers).
All certificates in a certificate chain should use ECDSA keys on P-384 curve. This is mandatory for servers and applicable for clients if client certificate validation is enabled.
-
-
Click Apply.
-
Select httpKeyMaterialObject from the Valued Attributes list and click Edit.
-
Browse to and select the Elliptic Curve certificate that you want to use with the HTTPS interface and click OK.
-
Click Apply, then click OK.
-
Restart eDirectory for the changes to take effect.
16.1.3 Creating an AES 256-Bit SDI Key
By default, the NICI SDI key is a 3DES key. However, to support Suite B modes, you need to manually create the AES 256-bit NICI SDI key. Create this key only when all servers in the tree are eDirectory 9.0.
When a server holding the writeable replica of KAP.Security container is upgraded to eDirectory 9.0, the PKI health check will create a W1 object in this container. When all servers in the tree are upgraded to eDirectory 9.0, the tree administrator can create the AES 256-bit NICI SDI key.
To create the AES 256-bit NICI SDI key, follow the instructions from Creating an AES 256-Bit Tree Key in the NICI Administration Guide.
Re-encrypting Data with AES 256-Bit NICI SDI Key
NMAS uses the NICI SDI key to securely store passwords and Challenge-Response configuration (questions and answers). NMAS also has a secret store for the user and method specific configuration that uses NICI SDI key. When the AES 256-bit NICI SDI key is created, NMAS handles re-encryption of existing secrets such as Universal Passwords and Simple Password using this key when a user logs in to eDirectory the first time after this key is created.
To re-encrypt passwords for multiple users in large deployments, use the diagpwd utility. For more information, see NetIQ Download Page.
IMPORTANT:If your eDirectory environment includes servers with prior versions of eDirectory and eDirectory 9.0 and you created the AES 256-bit tree key, the passwords are re-encrypted with the AES 256-bit keys when a user logs in to an eDirectory 9.0 server. When this occurs, the servers with prior versions of eDirectory will not be able to decrypt passwords or secret data resulting in a failed login to these servers.
16.1.4 Enabling Background Authentication
eDirectory provides a strong authentication mechanism that verifies the identity of users who request to access it. For more information about enhanced background authentication, see Section 17.0, Enabling Enhanced Background Authentication.