14.5 Configuring LDAP Objects
An eDirectory installation creates an LDAP server object and an LDAP Group object. The default configuration for LDAP Services is located in the directory on these two objects. You can modify the default configuration by using the LDAP Management task in NetIQ iManager.
The LDAP server object represents server-specific configuration data.
The LDAP Group object contains configuration information that can be conveniently shared among multiple LDAP servers. This object provides common configuration data and represents a group of LDAP servers. The servers have common data.
You can associate multiple LDAP server objects with one LDAP Group object. All the associated LDAP servers then get their server-specific configuration from their LDAP server object but get common or shared information from the LDAP Group object.
By default, the eDirectory installation program installs a single LDAP Group object and a single LDAP server object for each nldap.nlm or nldap.dlm. Later, you can associate multiple LDAP server objects with a single LDAP Group object.
IMPORTANT:Although it is possible to associate newer versions of an LDAP server object with older versions of LDAP Group objects, we recommend that you don't mix versions. For example, avoid associating an LDAP Group object in eDirectory 8.7.3 SP9 with an LDAP server object in eDirectory 9.0.
The amount of common information held in an LDAP Group object is limited. LDAP doesn’t need to read many attributes because the data contained in the attributes is incredibly common. Many LDAP servers will need to use the same data. Without a common or shared Group object, you would have to replicate that data across each LDAP server.
The LDAP server object allows more server-specific configuration options and data than the LDAP Group object allows.
Both objects have DN-syntax attributes that point to each other.
An additional association must be made so that the LDAP server can find its configuration data. This association is through the NCP™ server, which holds the customary eDirectory configuration data. The eDirectory installation program automatically makes the association.
Every eDirectory server has an NCP Server object. In the following figure, server Lundi illustrates this object as displayed in iManager:

This object has an LDAP Server attribute, which points to the LDAP server object for a particular host eDirectory server. The following figure illustrates this attribute:
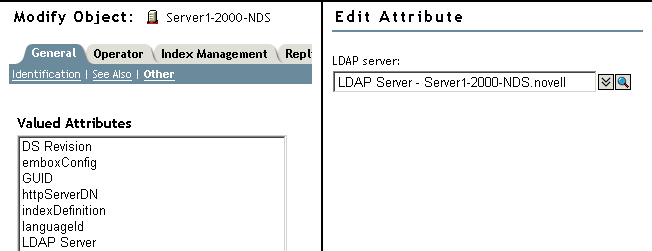
Typically, the LDAP server object, the LDAP Group object, and the NCP Server object are located in the same container. You name this container during the eDirectory installation, when you name the server and Admin context.
If you move the LDAP server object, you must place it in a writable replica.
14.5.1 Configuring LDAP Server and LDAP Group Objects on Linux
The LDAP configuration utility is ldapconfig. You can use ldapconfig on Linux, systems to modify, view, and refresh the attributes of LDAP server and LDAP Group objects.
Use the following syntax to view LDAP attribute values on Linux, systems:
ldapconfig get [...] | set attribute-value-list [-t treename | -p hostname[:port]] [-w password] [-a user FDN] [-f]
ldapconfig [-t tree_name | -p host_name[:port]] [-w password] [-a user FDN] [-V] [-R] [-H] [-f] -v attribute,attribute2...
Use the following syntax to modify values of LDAP attributes on Linux:
ldapconfig [-t tree_name | -p host_name[:port]] [-w password] [-a admin_FDN] -s attribute=value,...
|
Parameter |
Description |
|---|---|
|
-t treename |
Name of the eDirectory tree where the component will be installed. |
|
-p hostname |
The name of the host. You could specify the DNS name or IP address also. |
|
-w |
The password of the user having administration rights. |
|
-a |
The fully distinguished name of the user having administration rights. For example: cn=user.o=org1 |
|
get | -V |
Lets you view all LDAP server/group attributes. |
|
get | -v attribute list |
Displays the current values of the attributes in the attribute list. |
|
set | -s attribute-value pairs |
Sets the attributes to the specified values. |
|
-v |
Lets you view the value of the LDAP attribute. |
|
-s |
Sets a value for an attribute of the installed components. |
|
-R |
Refreshes the LDAP server. |
|
-V |
Lets you view the current LDAP configuration settings. |
|
-H |
Lets you view the usage and help strings. |
|
-f |
Allows operations on a filtered replica. |
|
attribute |
A configurable LDAP server or group attribute name. For more information, see Attributes on the LDAP Server Object and Attributes on the LDAP Group Object. |
Examples
To view the value of the attribute in the attribute list, enter the following command:
ldapconfig [-t tree_name | -p host_name[:port]] [-w password] [-a user_FDN] -v "Require TLS for simple binds with password","searchTimeLimit"
To configure the LDAP TCP port number and search size limit to 1000, enter the following command:
ldapconfig [-t tree_name | -p host_name[:port]] [-w password] [-a admin_FDN] -s "LDAP TCP Port=389","searchSizeLimit=1000”
Attributes on the LDAP Server Object
Use the LDAP server object to set up and manage the NetIQ LDAP server properties.
The following table provides a description of the LDAP server attributes:
|
Attribute |
Description |
|---|---|
|
LDAP Server |
The fully distinguished name of the LDAP server object in eDirectory. |
|
LDAP Host Server |
The fully distinguished name of the host eDirectory server that the LDAP server runs on. |
|
LDAP Group |
The LDAP Group object in eDirectory that this LDAP server is a member of. |
|
LDAP Server Bind Limit |
The number of clients that can simultaneously bind to the LDAP server. A value of 0 (zero) indicates no limit. |
|
LDAP Server Idle Timeout |
The period of inactivity from a client after which LDAP server terminates the connection with this client. A value of 0 (zero) indicates no limit. |
|
LDAP Enable TCP |
This option is deprecated. It is available through ldapInterfaces. For more information, see ldapInterfaces. |
|
LDAP Enable TLS |
This option has been deprecated. However, it is available through ldapInterfaces. For more information, see ldapInterfaces. |
|
LDAP TCP Port |
This option has been deprecated. However, it is available through ldapInterfaces. For more information, see ldapInterfaces. |
|
LDAP TLS Port |
This option has been deprecated. However, it is available through ldapInterfaces. For more information, see ldapInterfaces. |
|
keyMaterialName |
The name of the Certificate object in eDirectory that is associated with this LDAP server and will be used for SSL LDAP connections. |
|
searchSizeLimit |
The maximum number of entries that the LDAP server will return to an LDAP client in response to a search. A value of 0 (zero) indicates no limit. If the user has the administrator rights on the LDAP server object, the searchSizeLimit value is not considered. |
|
searchTimeLimit |
The maximum number of seconds after which an LDAP search will be timed out by the LDAP server. A value of 0 (zero) indicates no limit. If the user has the administrator rights on the LDAP server object, the searchTimeLimit value is not considered. |
|
filteredReplicaUsage |
Specifies whether the LDAP server should use a filtered replica for an LDAP search. Values=1 (use filtered replica), 0 (do not use filtered replica) |
|
sslEnableMutualAuthentication |
Specifies whether SSL-based mutual authentication (Certificate-based client authentication) is enabled on the LDAP server. |
|
ldapTLSVerifyClientCertificate |
Enables or disables verification of the client certificate for a TLS operation through LDAP. |
|
ldapNonStdAllUserAttrsMode |
Enables or disables the non standard, all user, and operational attributes. |
|
ldapBindRestrictions |
Enables LDAP bind restrictions and cipher level on LDAP client connections.This attribute can be used to control client connections. You can set any of the following seven LDAP bind restrictions using iManager:
NOTE:The value from 4 to 7 can be set from the ldapconfig utility. iManager doesn’t allow to set this value. For more information, see Table 14-1. For RSA and Elliptic Curve Digital Signature (ECDSA) algorithms, eDirectory allows you to use the following values to restrict the cipher usage:
|
|
Suite B Mode: Use the following values:
eDirectory allows you to use combination values of ldapbindrestrictions and cipher levels. For more information, see Table 14-1. |
|
ldapChainSecureRequired |
This is a boolean attribute. If enabled, chaining to other eDirectory will be over secure NCP. By default, ldapChainSecureRequired is disabled. |
|
ldapInterfaces |
A multi-valued SYN_CI_STRING attribute used to store LDAP URLs on which LDAP server listens (on both cleartext and secure ports). This attribute is useful in configuring multiple instances that require each instance of the eDirectory server to listen on a specific interface. It can be configured with the IP addresses and port numbers in the LDAP URL format.The LDAP server listens on these IP addresses and ports. The following are examples for IPv4 and IPv6 listeners. ldap://192.168.1.1:389 - To specify for IPv4 specific address on clear text port ldaps://192.168.2.1:636 - To specify for IPv4 specific address on secure port ldap://[2015::3]:389 - To specify for IPv6 specific address on clear text port ldaps://[2015::3]:636 - To specify for IPv6 specific address on secure port ldap://[::]:389 - To specify for IPv6 unspecified address on clear text port ldaps://[::]:636 - To specify for IPv6 unspecified address on secure port The LDAP Enable TCP, LDAP Enable TLS, LDAP TCP Port, and LDAP TLS Port attributes are not populated if a new server is configured from eDirectory 9.0. The ldapInterface atrribute values corresponding to the ports selected for ldap and ldaps during configuration are populated. For example, ldap://:389, ldaps://:636. By default, only IPv4 interface values are added to the ldapInterfaces attribute. During upgrade, eDirectory is triggered to delete the LDAP Enable TCP, LDAP Enable TLS, LDAP TCP Port, LDAP TLS Port attributes. It populates corresponding values of these attributes in ldapInterface. The ldapconfig set command takes comma separated values and replaces all the existing values with the new values. |
|
ldapStdCompliance |
eDirectory LDAP server by default does not return the sub-ordinate referrals for ONE level search. To enable this, you need to turn on ldapStdCompliance with a value 1. Setting this value will make the LDAP server return the sub-ordinate referrals for ONE level search. |
|
ldapChainSecureRequired |
This is a boolean attribute. If this is enabled, the chaining to other eDirectory will be over secure NCP. By default, the attribute will be disabled. |
|
ldapEnablePSearch |
Specifies whether or not the persistent search feature is enabled on the LDAP server. Values= yes, no |
|
ldapMaximumPSearchOperations |
An integer value that limits the number of concurrent persistent search operations possible. A value of 0 specifies unlimited search operations. |
|
ldapIgnorePSearchLimitsForEvents |
Indicates whether size and time limits should be ignored after the persistent search request has sent the initial result set. Values= yes, no If this attribute is set to false, the entire persistent search operation is subject to the search limits. If either limit is reached, the search fails with the appropriate error message. |
|
ldapGeneralizedTime |
Enable Generalized Time to display time in the YYYYMMDDHHmmSS.0Z format. Values= yes, no |
|
ldapPermissiveModify |
Enable Permissive Modify Control to extend the LDAP modify operation. If an attempt is made to delete an attribute that does not exist or to add any value to an attribute that already exists, the operation goes through without displaying any error message Values= yes, no |
|
ldapSSLConfig |
This attribute allows you to define the TLS protocols and Ciphers in the LDAP server object. By default, this attribute is disabled. This configuration attribute follows the following order of precedence:
If no protocol and cipher is defined using this attribute, the default configuration specified in the ldapBindRestrictions is followed. For more information, see Configuring Protocols and Ciphers Using ldapSSLConfig Attribute. NOTE:ldapSSLConfig attribute is available from eDirectory 9.0 SP2 onwards. |
|
ldapGroupSSLConfig |
This attribute allows you to define the TLS protocols and Ciphers in the LDAP group object. By default, this attribute is disabled. This configuration attribute follows the following order of precedence:
If no protocol and cipher is defined using this attribute, the default configuration specified in the ldapBindRestrictions is followed. For more information, see Configuring Protocols and Ciphers Using ldapSSLConfig Attribute. NOTE:If this attribute is set through ldapconfig get/set command, use ldapGroupSSLConfig and if set through ldif file, use ldapSSLConfig with LDAP Group object DN. |
Table 14-1 Combination Values of ldapbindrestrictions and Cipher Levels
|
ldapbindrestriction |
Certificate |
Cipher Level |
Combination Value |
|---|---|---|---|
|
None |
RSA |
Export |
0 |
|
RSA |
High |
48 |
|
|
RSA |
Medium |
32 |
|
|
RSA |
Low |
16 |
|
|
ECDSA 256/384 |
SUITEB128 |
64 |
|
|
ECDSA 256 |
SUITEB128ONLY |
80 |
|
|
ECDSA 384 |
SUITEB192 |
96 |
|
|
Disallows anonymous simple bind |
RSA |
Export |
1 |
|
RSA |
High |
49 |
|
|
RSA |
Medium |
33 |
|
|
RSA |
Low |
17 |
|
|
ECDSA 256/384 |
SUITEB128 |
65 |
|
|
ECDSA 256 |
SUITEB128ONLY |
81 |
|
|
ECDSA 384 |
SUITEB192 |
97 |
|
|
Disallow local bind |
RSA |
Export |
2 |
|
RSA |
High |
50 |
|
|
RSA |
Medium |
34 |
|
|
RSA |
Low |
18 |
|
|
ECDSA 256/384 |
SUITEB128 |
66 |
|
|
ECDSA 256 |
SUITEB128ONLY |
82 |
|
|
ECDSA 384 |
SUITEB192 |
98 |
|
|
Disallow anonymous simple bind and unbind |
RSA |
Export |
3 |
|
RSA |
High |
51 |
|
|
RSA |
Medium |
35 |
|
|
RSA |
Low |
19 |
|
|
ECDSA 256/384 |
SUITEB128 |
67 |
|
|
ECDSA 256 |
SUITEB128ONLY |
83 |
|
|
ECDSA 384 |
SUITEB192 |
99 |
|
|
Disallows unauthenticated bind |
RSA |
Export |
4 |
|
RSA |
High |
52 |
|
|
RSA |
Medium |
36 |
|
|
RSA |
Low |
20 |
|
|
ECDSA 256/384 |
SUITEB128 |
68 |
|
|
ECDSA 256 |
SUITEB128ONLY |
84 |
|
|
ECDSA 384 |
SUITEB192 |
100 |
|
|
Disallows anonymous and unauthenticated bind |
RSA |
Export |
5 |
|
RSA |
High |
53 |
|
|
RSA |
Medium |
37 |
|
|
RSA |
Low |
21 |
|
|
ECDSA 256/384 |
SUITEB128 |
69 |
|
|
ECDSA 256 |
SUITEB128ONLY |
85 |
|
|
ECDSA 384 |
SUITEB192 |
101 |
|
|
Disallows non-anonymous simple bind and unauthenticated bind |
RSA |
Export |
6 |
|
RSA |
High |
54 |
|
|
RSA |
Medium |
38 |
|
|
RSA |
Low |
22 |
|
|
ECDSA 256/384 |
SUITEB128 |
70 |
|
|
ECDSA 256 |
SUITEB128ONLY |
86 |
|
|
ECDSA 384 |
SUITEB192 |
102 |
|
|
Disallows anonymous simple bind, non-anonymous simple bind and unauthenticated bind |
RSA |
Export |
7 |
|
RSA |
High |
55 |
|
|
RSA |
Medium |
39 |
|
|
RSA |
Low |
23 |
|
|
ECDSA 256/384 |
SUITEB128 |
71 |
|
|
ECDSA 256 |
SUITEB128ONLY |
87 |
|
|
ECDSA 384 |
SUITEB192 |
103 |
Attributes on the LDAP Group Object
Use the LDAP Group object to set up and manage the way LDAP clients access and use the information on the NetIQ LDAP server.
To require TLS for simple binds, see Requiring TLS for Simple Binds with Passwords. This attribute specifies whether the LDAP server allows transmission of passwords in clear text from an LDAP client. Values=0 (no) or 1 (yes).
To specify a default referral, referralIncludeFilter, referralExludeFilter and how LDAP servers process LDAP referrals, see Using Referrals.
To specify the TLS protocols and Ciphers, you can use the ldapSSLConfig attribute. For more information, see Configuring Protocols and Ciphers Using ldapSSLConfig Attribute.
14.5.2 Configuring Protocols and Ciphers Using ldapSSLConfig Attribute
eDirectory allows you to define various TLS parameters and Ciphers required for TLS communication of LDAP server.
You can specify the protocol and ciphers in JSON format in the ldapSSLConfig attribute for both LDAP server and group object. For example, you can define the protocols and ciphers as mentioned in the below JSON format:
{
"Version": 1,
"Info": {
"Protocol": "+ALL-SSLv3",
"Ciphers": "ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384"
}
}
NOTE:If you specify incorrect information in the ldapSSLConfig attribute, the default configuration specified in the ldapBindRestrictions will be followed.
Configuring Ciphers
You can configure your own list of ciphers using the OpenSSL Cipher List Format. The following examples illustrate the use of Cipher list format that are used during TLS communication of LDAP server:
-
For RSA certificates: !CAMELLIA:!DH:!SRP:!MD5:HIGH+aRSA
-
For ECDSA certificates: HIGH+aECDSA
-
For Suite B 128-bit compliant cipher suite with ECDSA certificates: ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256
-
For Suite B 192-bit compliant cipher suite with ECDSA certificates: ECDHE-ECDSA-AES128-GCM-SHA256
For more information on Cipher List Format, refer to the OpenSSL Ciphers documentation.
Configuring Protocols
eDirectory gives you the flexibility to configure the list of protocols required during the TLS communication. To control the list of protocols, define the required protocol in JSON format in the ldapSSLConfig attribute. You can configure the following protocol strings:
-
SSLv3
-
TLSv1.0
-
TLSv1.1
-
TLSv1.2
-
ALL
Each protocol string should be preceded by a “+” or a “-” symbol. The “+” symbol indicates that the protocol string(s) are allowed and the “-” symbol indicates that the protocol string(s) are not allowed by eDirectory. The following table lists a few TLS protocol configurations:
|
Protocol Configuration |
Description |
|---|---|
|
+TLSv1.2 |
Allows only TLSv1.2 |
|
+ALL-TLSv1.0 |
Allows all except TLSv1.0 |
|
+ALL-TLSv1.2-TLSv1.1 |
Allows SSLv3 and TLSv1.0 |
|
+ALL |
Allows SSLv3, TLSv1.0, TLSv1.1, TLSv1.2 |
NOTE:A protocol can only be preceded by “-” symbol when +ALL is specified.
Examples:
Configuring Protocols and Ciphers in Suite B Compliant Mode
{
"Version": 1,
"Info": {
"Protocol": "+TLSv1.2",
"Ciphers": "ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384"
}
}
In the above example, protocol is defined as +TLSv1.2 in JSON format. Only TLSv1.2 is a supported protocol for Suite B compliant mode.
Configuring Protocols and Ciphers in Non-Suite B Compliant Mode
{
"Version": 1,
"Info": {
"Protocol": "+ALL-SSLv3",
"Ciphers": "HIGH+aECDSA"
}
}
In the above example, protocol is defined as +ALL-SSLv3 in JSON format which means all supported protocols except SSLv3 are allowed during TLS communication.