5.1 Implementing Multi-Factor Authentication to VPN
Let us assume Reltic Data, Inc. wants to implement multi-factor authentication for its VPN (Virtual Private Network) connection to secure the Corporate network that is accessed from their employees who are in a remote location.
This section explains the prerequisites, flow of actions, and step-by-step configuration details to achieve this.
This example refers to the following user profiles:
-
Thomas: An administrator of Reltic Data, Inc.
-
Mark Jones: An employee of Reltic Data, Inc.
Thomas, an administrator wants to enforce Multi-factor authentication with the LDAP Password and Smartphone methods for OpenVPN to secure the corporate network. After multi-factor authentication is implemented, employees need to authenticate to both methods successfully to access the network through VPN.
Thomas must perform the following tasks to implement multi-factor authentication for OpenVPN:
To understand the sequential flow of configuration in the Advanced Authentication Administration portal, see Configuration Flow in Advanced Authentication for RADIUS Server Event.
For information about how an end user enrolls the configured methods and authenticates to VPN client using Advanced Authentication, see End User Tasks.
5.1.1 Prerequisites
Ensure that you meet the following prerequisites:
-
An LDAP repository for Reltic Data, Inc is configured and the repository contains the information of all users.
This example uses Active Directory Domain Services as an LDAP repository.
-
A group named Employees is created in Active Directory Domain Services.
-
The Advanced Authentication server is installed. For more information, see Installing Advanced Authentication.
-
A VPN client is installed on all employees' system.
This example uses OpenVPN as the VPN client.
5.1.2 Considerations Before Configuration
Follow these guidelines to begin implementing multi-factor authentication for any event:
-
Identify the authentication methods that you want to configure.
-
Determine the order of methods in the chain. The methods are displayed to the end user in the order that you have configured.
-
Determine the policy that must be configured for the identified method.
-
Identify the user group for which you want to enforce this authentication chain.
Configuration Flow in Advanced Authentication for RADIUS Server Event
The following diagram illustrates the sequential flow of actions required for securing the Open VPN client with multi-factor authentication:
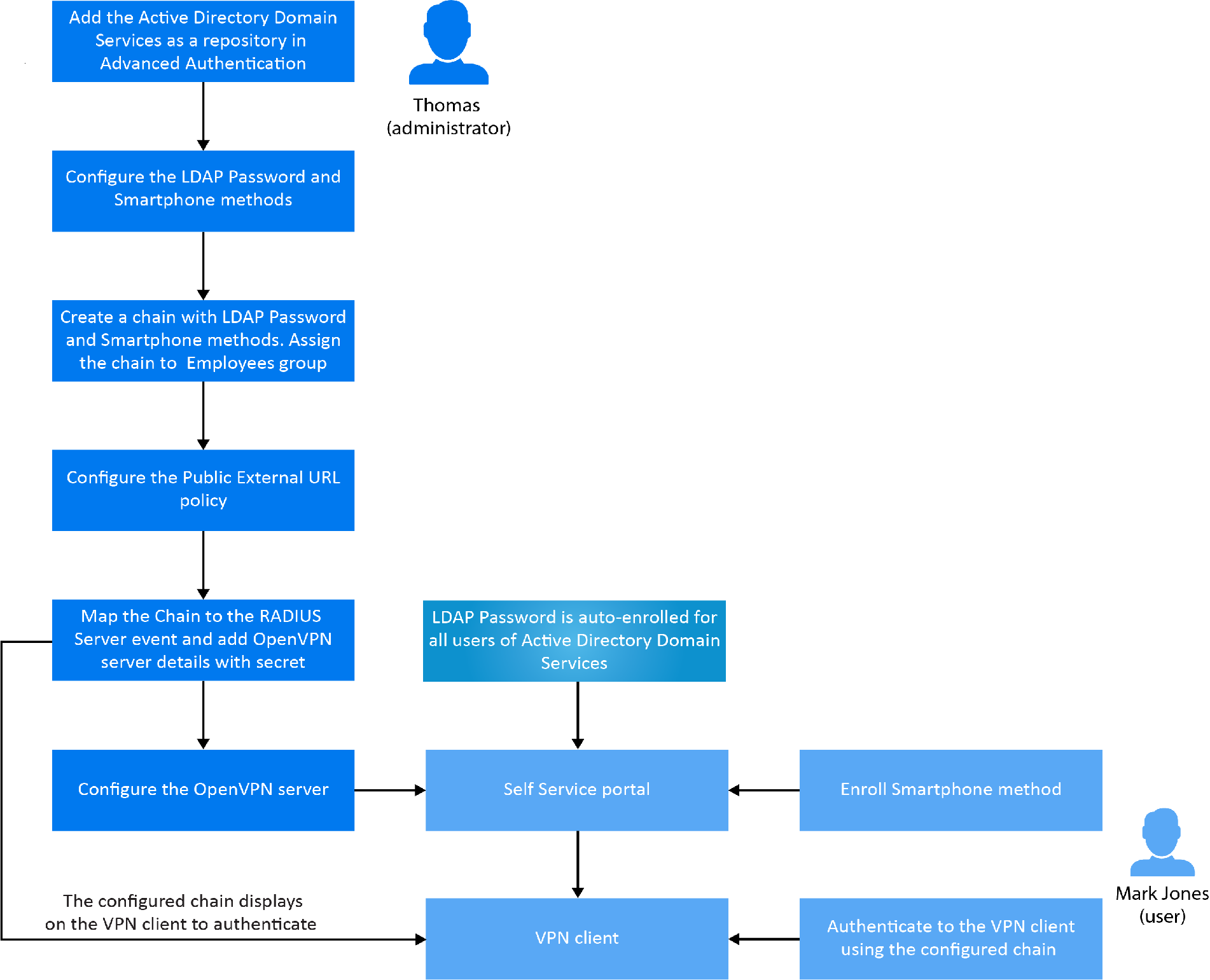
5.1.3 Add a Repository
In Advanced Authentication, add Active Directory of Reltic Data, Inc. as a repository from where the user details are fetched for validation.
Perform the following steps to add Active Directory of Reltic Data, Inc. to Advanced Authentication:
-
Click Repositories on the Advanced Authentication Administration portal.
-
Click Add LDAP repo.
-
Select AD (Active Directory Domain Services) from the LDAP type list.
-
Specify a container for the users in Base DN. When you select the Subtree option, Advanced Authentication performs a search for the users in each child node. You can change the search scope by selecting the Search one level only option.
-
Specify a user account in User and specify the password of the user in Password.
Ensure that the user's password has no expiry.
-
You can specify a container for the groups in Group DN (optional). When you select the Subtree option, Advanced Authentication performs a search for the groups in each child node. You can change the search scope by selecting the Search one level only option.
-
Select DNS discovery to find LDAP servers automatically. Specify DNS zone and Site name (optional) and click Perform DNS Discovery.
When the DNS discovery is done, the DNS servers list is updated every three hours.
-
Click Save.
NOTE:If an LDAP server is unavailable for 2.5 seconds, Advanced Authentication excludes it from the LDAP requests for a period of 3 minutes.
5.1.4 Configure Methods
The LDAP Password and Smartphone methods are configured with pre-defined values. These methods work as expected with the pre-defined values.
For more information, see LDAP Password and Smartphone.
5.1.5 Create a Chain
Perform the following steps to create a chain with LDAP Password and Smartphone methods:
-
Click Chains > Add in the Advanced Authentication Administration portal.
-
Specify the following details:
Field
Description
Name
A name for the chain.
NOTE:Ensure to remember the name of the chain for further use.
Short name
A name that is provided to end user for selecting a chain.
For example, you configure a chain named SMS containing LDAP Password and SMS methods. A user can specify <username> sms and the user is required to use SMS as the chain. This is helpful in scenarios when the primary chain is not available.
Is enabled
Set to ON to enable the chain.
Methods
Select the LDAP Password and Smartphone methods to add to the chain.
Roles and Groups
Specify Employees. This enforces all users of this group to use this authentication chain for accessing the corporate network through VPN.
-
Click Save.
-
Continue with Configure Public External URLs Policy.
5.1.6 Configure Public External URLs Policy
The external URL manages the following activities for the Smartphone method:
-
A push notification that is sent to the NetIQ Advanced Authentication app.
-
User responses from the NetIQ Advanced Authentication app.
Perform the following steps to configure the external URL:
-
Click Policies > Public External URLs on the Advanced Authentication Administration portal.
-
Click Edit and specify the URL in Public URL.
Ensure that the Public URL is accessible from users' smartphone.
-
Click OK.
-
Continue with Assign Chain to RADIUS Server Event.
5.1.7 Assign Chain to RADIUS Server Event
Perform the following steps to assign the chain to RADIUS Server event and configure details of the Open VPN server with a secret:
-
Click Events.
-
Click Edit next to the RADIUS Server event.
-
Ensure that Is enabled is set to ON.
-
Select the chains that you have created in Create a Chain.
-
Click Add to add and assign a RADIUS Client to the event:
-
Specify the IP address of the OpenVPN server in IP Address.
-
Specify the OpenVPN server name in Name.
-
Specify the OpenVPN server secret and confirm the secret.
NOTE:Ensure to make a note of this secret for future reference.
-
Ensure that the RADIUS Client is set to ON.
-
-
Click Save.
-
Continue with Configure the OpenVPN Server.
5.1.8 Configure the OpenVPN Server
Perform the following steps to configure the OpenVPN server and enable the server to connect with Advanced Authentication server:
-
Open the OpenVPN Access server site.
-
Click Authentication > RADIUS.
-
Enable the RADIUS authentication.
-
Select PAP.
-
Add an IP address of the Advanced Authentication server and specify the secret that is set while configuring the RADIUS Server event in the Advanced Authentication Administration portal.
You must specify the <repository name>\<username> or only <username> if you have set the following configurations:
-
You have selected a chain from the Used section in the RADIUS Server settings for connecting to OpenVPN.
-
You have set the default repository name in Policies > Login options of the Advanced Authentication appliance.
5.1.9 End User Tasks
Mark, as an employee, must perform the following actions to access the corporate network of Reltic Data network through OpenVPN:
NOTE:The LDAP Password method enrolls automatically and users cannot remove it.
For more information, see LDAP Password.
Enroll the Smartphone Method
Mark must ensure to install the NetIQ Auth application on his smartphone to enroll the Smartphone method.
For more information about downloading and installing the NetIQ Auth application, see Installing NetIQ Advanced Authentication App.
During the enrollment, Mark must scan a QR code that creates an authenticator on his mobile app. When Mark initiates the authentication, a push notification is sent to the app. Accept the request and get authenticated.
To enroll the Smartphone method with a QR code, perform the following steps:
-
Click the Smartphone icon under the Add Authenticator section of the Self-Service portal.
-
(Optional) Specify a comment related to the Smartphone authenticator.
-
(Optional) Select the required category from Category.
-
Click Save.
A QR code is displayed.
-
Scan the QR code with the NetIQ Auth app. To do this, perform the following steps:
-
Open the NetIQ Auth app.
-
Specify a PIN if applicable.
-
Click the + (plus) icon in the Enrolled Authenticators screen.
-
The camera of your smartphone is launched.
-
Scan the QR code with the camera.
A message Authenticator "Smartphone" added is displayed.
-
-
Specify the user name and an optional comment in the app.
-
Tap Save.
The smartphone authenticator is created.
If Mark does not enroll the Smartphone method within few minutes, an error message Enroll failed: Enroll timeout is displayed. He can refresh the browser and try enrolling again.
HINT:If you users are unable to scan the QR code with the NetIQ Auth app, they can do the following:
-
Zoom the page to 125-150% and scan the zoomed QR code.
-
Ensure that nothing overlaps the QR code (mouse cursor, text).
For more information, see Smartphone.
Authenticate to OpenVPN Using Advanced Authentication
-
Launch the OpenVPN client.
The Login dialog is displayed.
-
Specify Username and LDAP Password.
-
Open the NetIQ Auth app in the mobile phone.
Specify PIN or touch the enrolled finger that you registered for the app.
-
Tap Accept in the Authentication Requests screen to accept the authentication request.
A message Accepted is displayed and Mark authenticates to OpenVPN successfully.