10.2.6 Mapping Roles between Trusted Providers
Identity Server can send roles in an authentication assertion. You can map these roles that are received from trusted providers to your own roles. Figure 10-5 illustrates this process.
Figure 10-5 Role Mapping
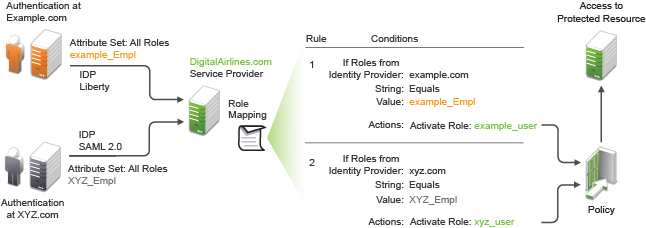
In this example, employees authenticate to identity providers example.com (Liberty) or xyz.com (SAML 2.0). Each user is assigned to a role, such as N_EmployeeRole or XYZ_Empl. Attribute sets at each of the identity providers are configured to exchange the All Roles attribute with the trusted service provider, DigitalAirlines.com. DigitalAirlines.com consumes the authentication assertions, then maps the incoming roles to local roles. The mapped roles at DigitalAirlines.com can be used as evaluated conditions in authorization policies, which can provide access to resources intended for the authenticated employees.
Prerequisites
-
Configure trust between trusted providers, using the Liberty or SAML 2.0 protocol.
You must be familiar with Configuring SAML 2.0 and Configuring Liberty.
-
Configure local authentication.
You must create an external contract at the service provider that matches the contract of the identity provider. See Local Authentication.
-
Create an attribute set and select the local attribute All Roles in the set. This must be done at the identity provider and service provider.
This attribute set is used to pass roles from an identity provider to an external service provider in authentication assertions. See Configuring Attribute Sets.
Procedure
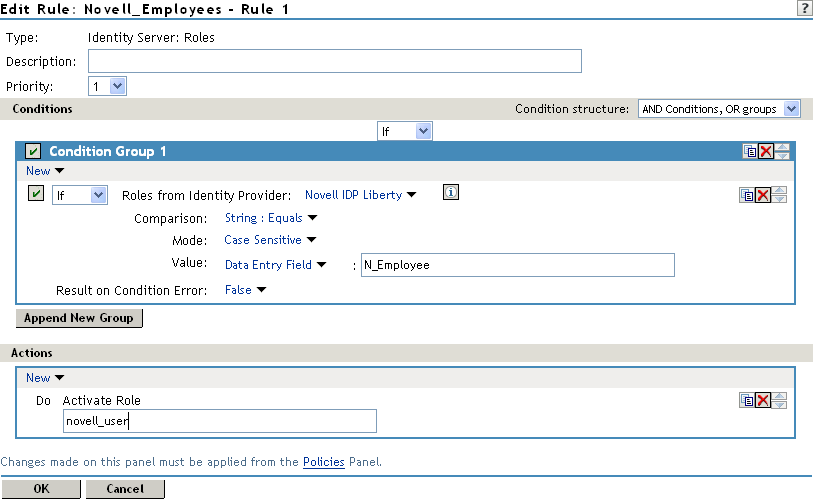
The following procedure describes how the service provider configures this type of role policy for novell.com, mapping the N_Employee role to an Access Manager role:
-
Click Policies > Policies > New.
-
Select Identity Server: Roles for the type, then click OK.
-
Configure the role policy as shown in the following image:
-
In the Conditions section, click New > Roles from Identity Provider.
-
Select the trusted identity provider.
-
For Comparison, select String > Equals.
-
Select Value > Data Entry Field.
-
Type the name of the role used by the trusted identity provider.
-
Under the Actions section, click Activate Role.
-
Type the name of the role you want to activate at the trusted service provider.
-
Click OK.
-
On the Policies page, click Apply Changes.
-
To enable the role so that it can be used in Authorization and Identity Injection policies, click Identity Servers > Servers > Edit > Roles.
-
Select the check box next to the name of the role, then click Enable.
-
Click OK.
-
Update Identity Server.