4.2.3 Configuring User Identification Methods for Federation
Configuring authentication involves determining how the service provider interacts with the identity provider during user authentication and federation. Three methods exist for you to identify users from a trusted identity provider:
-
You can identify users by matching their authentication credentials
-
You can match selected attributes and then prompt for a password to verify the match, or you can use just the attributes for the match.
-
You can assume that the user does not have an account and create new accounts with user provisioning. You can also allow for provisioning when the matching methods fail. If there are problems during provisioning, you see error messages with more information.
The following sections describe how to configure these methods:
Defining User Identification for Liberty and SAML 2.0
Selecting a User Identification Method for Liberty or SAML 2.0
User identification determines how an account at the identity provider is matched with an account at the service provider. If federation is enabled between the two, the user can set up a permanent relationship between the two accounts. If federation is not enabled (see Configuring a SAML 2.0 Authentication Request and Configuring a Liberty Authentication Request), you cannot set up a user identification method.
-
Click Devices > Identity Servers > Edit > Liberty [or SAML 2.0] > [Identity Provider] > User Identification.
-
Specify how users are identified on the SAML 2.0 or Liberty provider. Select one of the following methods:
-
Authenticate: Select this option when you want to use login credentials. This option prompts the user to log in at both the identity provider and the service provider on first access. If the user selects to federate, the user is prompted, on subsequent logins, to authenticate only to the identity provider.
-
Allow ‘Provisioning’: Select this option to allow users to create an account when they have no account on the service provider.
This option requires that you specify a user provisioning method.
-
-
Provision account: Select this option when the users on the identity provider do not have accounts on the service provider. This option allows the service provider to trust any user that has authenticated to the trusted identity provider
This option requires that you specify a user provisioning method.
-
Attribute matching: Select this option when you want to use attributes to match an identity server account with a service provider account. This option requires that you specify a user matching method.
-
Prompt for password on successful match: Select this option to prompt the user for a password when the user’s name is matched to an account, to ensure that the account matches.
-
NOTE:If you have selected Transient user mapping while configuring the name identifier format, the Authenticate and Provision account options are not displayed for SAML 2.0.
-
-
Select one of the following:
-
If you selected the Attribute matching option, select a method, then click OK. If you have not created a matching method, continue with Configuring the Attribute Matching Method for Liberty or SAML 2.0.
-
If you selected the Provision account option, select a method, then click OK. If you have not created a provisioning method, continue with Defining the User Provisioning Method.
-
If you selected the Authenticate option with the Allow Provisioning option, select a method, then click OK. If you have not created a provisioning method, continue with Defining the User Provisioning Method.
-
If you selected the Authenticate option without the Allow Provisioning option, click OK.
-
-
Configure the authentication methods that must be used before authenticating the users.
Step Up Authentication methods: These are the existing configured authentication methods that you can use for secondary authentication. Use the arrow keys to move methods from the available methods list to the step up methods list. The selected methods are used in the same order as listed for the step up authentication. The step up authentication does not require to identify the user because identity provider already authenticates the user. The step up authentication is used for additional authentication to access the services. Hence, the selected methods must not have Identifies User selected in its configuration. After an identity provider authenticates, the Identity Server (service provider) prompts for step up authentication for additional security. If the step up authentication method is not satisfied, authentication fails.
NOTE:To enable the audit events for step up authentication, select the Federation Step-up audit event.
-
Configure the post authentication method. These are the existing methods that can be used after the authentication is successful. These are not used for authenticating a user but to perform custom tasks post authentication, such as password fetch. For information about password fetch, see Section 4.1.10, Password Retrieval. If the post authentication method fails, the session will remain valid.
Selected Methods: Using the arrow keys to move methods from the Available Methods list to the Selected Methods list. The selected method is executed when post remote authentication completes.
For example if you select the passwordfetch method, this method is executed at the service provider after the identity provider authentication and federation completes.
Logout on method execution failure: If you select this check box, then whenever there is a session failure, the user is logged out automatically.
-
Configure the session options.
Allow IDP to set session timeout: Select Allow Identity Provider to set session time-out between the principal identified by the subject and the SAML authority based on SessionNotOnOrAfter attribute in SAML assertion of authnStatement.
Overwrite Temporary User: If you select this check box, then the temporary user credentials profile got from previous authentication method in the same session will be overwritten with real user credentials profile got from this authentication method.
Overwrite Real User: If you select this check box, then the real user credentials profile got from previous authentication method in the same session will be overwritten with real user credentials profile got from this authentication method
Assertion Validity Window: You can manually set the assertion validity time for SAML Service Provider (SP) to accommodate clock skew between Service Provider and SAML Identity (IDP) Server.
-
Click OK twice, then update Identity Server.
Configuring the Attribute Matching Method for Liberty or SAML 2.0
If you enabled the Attribute matching option when selecting a user identification method, you must configure a matching method.
The Liberty Personal Profile is enabled by default. If you have disabled it, you need to enable it. See Managing Web Services and Profiles.
-
Click Devices > Identity Servers > Servers > Edit > Liberty [or SAML 2.0] > [Identity Provider] > User Identification.
-
Click Attribute Matching settings.
-
Select and arrange the user stores you want to use.
Order is important. The user store at the top of the list is searched first. If a match is found, the other user stores are not searched.
-
Select a matching expression, or click New to create a look-up expression. For information about creating a look-up expression, see Section 2.3.8, Configuring User Matching Expressions.
-
Specify what action to take if no match is found.
-
Do nothing: Specifies that an identity provider account is not matched with a service provider account. This option allows the user to authenticate the session without identifying a user account on the service provider.
IMPORTANT:Do not select this option if the expected name format identifier is persistent. A persistent name format identifier requires that the user be identified so that information can be stored with that user. To support the Do nothing option and allow anonymous access, the authentication response must be configured for a transient identifier format. To view the service provider configuration, see Section 2.7.8, Configuring an Authentication Response for a Service Provider.
-
Prompt user for authentication: Allows the user to specify the credentials for a user that exists on the service provider. Sometimes users have accounts at both the identity provider and the service provider, but the accounts were created independently, use different names (for example, joe.smith and jsmith) and different passwords, and share no common attributes except for the credentials known by the user.
-
Provision account: Assumes that the user does not have an account at the service provider and creates one for the user. You must create a provisioning method.
-
-
Click OK.
-
(Conditional) If you selected Provision account when no match is found, select the Provision settings icon. For information about this process, see Defining the User Provisioning Method.
-
Click OK twice, then update Identity Server.
Defining User Identification for SAML 1.1
Selecting a User Identification Method for SAML 1.1
Two methods exist for identifying users from an identity provider when using the SAML 1.1 protocol. You can specify that no account matching needs to occur, or you can configure a match method. You configure a match method when you want to use attributes from the identity provider to uniquely identify a user on the service provider.
-
Click Devices > Identity Servers > Edit > SAML 1.1 > [Identity Provider] > User Identification.
-
In the Satisfies contract option, specify the contract that can be used to satisfy the assertion received from the identity provider. Because SAML 1.1 does not use contracts and because Identity Server is contract-based, this setting permits an association to be made between a contract and a SAML 1.1 assertion.
Use caution when assigning the contract to associate with the assertion, because it is possible to imply that authentication has occurred, when it has not. For example, if a contract is assigned to the assertion, and the contract has two authentication methods (such as one for name/password and another for X.509), the server sending the assertion might use only name/password, but the service provider might assume that X.509 took place and then incorrectly assert it to another server.
-
Select one of the following options for user identification:
-
Do nothing: Specifies that an identity provider account is not matched with a service provider account. This option allows the user to authenticate the session without identifying a user account on the service provider.
-
Attribute matching: Authenticates a user by matching a user account on the identity provider with an account on the service provider. This option requires that you set up the match method.
-
Prompt for password on successful match: Specifies whether to prompt the user for a password when the user is matched to an account, to ensure that the account matches.
-
-
-
Select one of the following:
-
If you selected Do nothing, continue with Step 6.
-
If you selected Attribute matching, continue with Configuring the Attribute Matching Method for SAML 1.1.
-
-
You can also configure the assertion time manually.
-
Assertion Validity Window: You can manually set the assertion validity time for SAML Service Provider (SP) to accommodate clock skew between Service Provider and SAML Identity (IDP) Server.
-
-
Click OK twice.
-
Click Apply to make the user identification configuration changes.
-
Update Identity Server.
Configuring the Attribute Matching Method for SAML 1.1
A user matching expression is a set of logic groups with attributes that uniquely identify a user. User matching expressions enable you to map the Liberty attributes to the correct LDAP attributes during searches. You must know the LDAP attributes that can be used to identify unique users in the user store.
To use user matching, the Personal Profile must be enabled. It is enabled by default. If you have disabled it, you need to enable it. See Managing Web Services and Profiles.
-
Click Devices > Identity Servers > Servers > Edit > SAML 1.1 > [Identity Provider] > User Identification.
-
To configure the match method, click Attribute Matching settings.
-
Select and arrange the user stores you want to use.
Order is important. The user store at the top of the list is searched first. If a match is found, the other user stores are not searched.
-
Select a matching expression, or click New to create a look-up expression. For information about creating a look-up expression, see Section 2.3.8, Configuring User Matching Expressions.
-
Click OK.
-
Update Identity Server.
Defining the User Provisioning Method
If you have selected Provision account as the user identification method or have created an attribute matching setting that allows for provisioning when no match is found, you need to create a provision method. This procedure involves selecting required and optional attributes that the service provider requests from the identity provider during provisioning.
IMPORTANT:When a user object is created in the directory, some attributes are initially created with the value of NAM Generated. Afterwards, an attempt is made to write the required and optional attributes to the new user object. Because required and optional attributes are profile attributes, the system checks the write policy for the profile’s Data Location Settings (specified in Liberty > Web Service Provider) and writes the attribute in either LDAP or the configuration store. For the LDAP write to succeed, each attribute must be properly mapped as an LDAP Attribute. Additionally, you must enable the read/write permissions for each attribute in the Liberty/LDAP attribute maps. See Mapping LDAP and Liberty Attributes.
To configure user provisioning:
-
Click Devices > Identity Servers > Servers > Edit > Liberty [or SAML 2.0] > [Identity Provider] > User Identification.
-
Click the Provisioning settings icon.
-
Select the required attributes from the Available Attributes list and move them to the Attributes list.
Required attributes are those used in the creation of a user name, or that are required when creating the account.
-
Click Next.
-
Select optional attributes from the Available Attributes list and move them to the Attributes list.
This step is similar to selecting required attributes. However, the user provisioning request creates the user account whether the optional attributes exist on the service provider.
-
Click Next.
-
Define how to create the username.
You can specify whether users are prompted to create their own usernames or whether the system automatically creates usernames. Selecting an attribute for the username segments from the required attributes list improves the chances that a new username is successfully created.
Maximum length: The maximum length of the user name. This value must be between 1 and 50.
Prompt for user name: Enables users to create their own usernames.
Automatically create user name: Specifies that the system creates usernames. You can configure the segments for the system to use when creating usernames and configure how the names are displayed.
For example, if you are using the required attributes of Common First Name and Common Last Name, a username for Adam Smith might be generated as A.Smith_02, as shown in the following illustration:
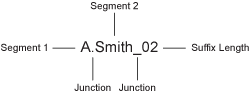
Use the following settings to specify how this is accomplished:
-
Segment 1: The required attribute to use as the first segment for the user name. The values displayed in this drop-down menu correspond to the required attributes you selected. For example, you might select Common First Name to use for Segment 1.
-
Length: The length of the first attribute segment. For example, if you selected Common First Name for the Segment 1 value, setting the length to 1 specifies that the system uses the first letter of the Common First Name attribute. Therefore, Adam Smith would be ASmith.
-
Junction: The type of junction to use between the attributes of the user name. If a period is selected, Adam Smith would display as A.Smith.
-
Segment 2: The required attribute to use as the second segment for the user name. The values displayed in this drop-down menu correspond to the required attributes you selected. For example, you might select Common Last Name to use for Segment 2.
-
Length: The length of the second attribute segment. For example, if you selected Common Last Name for the Segment 2 value, you might set the length to All, so that the full last name is displayed. However, the system does not allow more than 20 characters for the length of segment 2.
-
Ensure name is unique: Applies a suffix to the colliding name until a unique name is found, if using attributes causes a collision with an existing name. If no attributes are provided, or the lengths for them are 0, and this option is selected, the system creates a unique name.
-
-
Click Next.
-
Specify password settings.
Use this page to specify whether to prompt the user for a password or to create a password automatically.
Min. password length: The minimum length of the password.
Max. password length: The maximum length of the password.
Prompt for password: Prompts the user for a password.
Automatically create password: Specifies whether to automatically create passwords.
-
Click Next.
-
Specify the user store and context in which to create the account.
User Store: The user store in which to create the new user account.
Context: The context in the user store you want accounts created.
The system creates the user within a specific context; however, uniqueness is not guaranteed across the directory.
Delete user provisioning accounts if federation is terminated: Specifies whether to automatically delete the provisioned user account at the service provider if the user terminates his or her federation between the identity provider and service provider.
-
Click Finish.
-
Click OK twice, then update Identity Server.
User Provisioning Error Messages
The following error messages are displayed for the end user if there are problems during provisioning:
Table 4-1 Provisioning Error Messages
|
Error Message |
Cause |
|---|---|
Username length cannot exceed (?) characters. |
The user entered more characters for a user name than is allowed, as specified by the administrator. |
Username is not available. |
The user entered a name that already exists in the directory. |
Passwords don't match. |
The user provided two password values that do not match. |
Passwords must be between (x) and (y) characters in length. |
The user provided password values that are either too short or too long. |
Username unavailable. |
The provisioned user account was deleted without first defederating the user. Remove orphaned identity objects from the configuration datastore. IMPORTANT:Only experienced LDAP users must remove orphaned identity objects from the configuration datastore. You must ensure that the objects you are removing are orphaned. Otherwise, you create orphaned objects by mistake. |
Unable to complete authentication request. |
The password provided does not conform to the Windows password complexity policy in Active Directory. Ensure that Active Directory is configured to use a secure port, such as 636, and that the user’s password conforms to the complexity policy. If you encounter this error, you must reset the password on the Windows machine. Can occur when users are allowed to create accounts from a service provider’s login page, when the service provider uses Active Directory for the user store. |