1.3 Access Manager Components and Their Features
1.3.1 Administration Console
Administration Console is the central configuration and management tool for the product. It contains a Dashboard option, which allows you to assess the health of all Access Manager components.
Administration Console allows you to configure and manage each component. It also allows you to manage resources, such as policies, hardware, and certificates, which are used by multiple components.
1.3.2 Identity Servers
Identity Server is the central authentication and identity access point for all other services. It is responsible for authenticating users and distributing role information to facilitate authorization decisions. It also provides the Liberty Alliance Web Service Framework to distribute identity information.
An Identity Server always operates as an identity provider and can optionally be configured to run as an identity consumer (also known as a service provider), by using Liberty, SAML 1.1, SAML 2.0 or OAuth protocols. As an identity provider, Identity Server validates authentications against the supported identity user store. It is the heart of the user’s identity federations or account linkage information.
In an Access Manager configuration, Identity Server is responsible for managing the following tasks:
-
Authentication: Verifies user identities through various forms of authentication, both local (user supplied) and indirect (supplied by external providers). The identity information can be some characteristic attribute of the user, such as a role, e-mail address, name, or job description. Advanced authentication mechanisms include Time-Based One-Time Password(TOTP), social authentication using external OAuth providers, and risk-based authentication.
-
Identity Stores: Links to user identities stored in eDirectory, Microsoft Active Directory, or Sun ONE Directory Server.
-
Identity Federation: Enables user identity federation and provides access to Liberty-enabled services.
-
Account Provisioning: Enables service provider account provisioning, which automatically creates user accounts during a federation request.
-
Custom Attribute Mapping: Allows you to define custom attributes by mapping Liberty Alliance keywords to LDAP-accessible data, in addition to the available Liberty Alliance Employee and Person profiles.
-
SAML Assertions: Processes and generates SAML assertions. Using SAML assertions in each Access Manager component protects confidential information by removing the need to pass user credentials between the components to handle session management.
-
Single Sign-On and Logout: Enables users to log in only once to gain access to multiple applications and platforms. Single sign-on and single logout are primary features of Access Manager and are achieved after the federation and trust model is configured among trusted providers and the components of Access Manager.
-
Identity Integration: Provides authentication and identity services to Access Gateways that are configured to protect web servers. Access Gateway and other Access Manager components include an embedded service provider that is trusted by Access Manager Identity Servers.
-
Roles: Provides RBAC (role-based access control) management. RBAC is used to provide a convenient way to assign a user to a particular job function or set of permissions within an enterprise to control access. Identity Server establishes the active set of roles for a user session each time the user is authenticated. Roles can be assigned to particular subsets of users based on constraints outlined in a role policy. The established roles can then be used in authorization policies to form the basis for granting and restricting access to particular web resources.
1.3.3 Access Gateways
An Access Gateway provides secure access to existing HTTP-based web servers. It provides security services (authorization, single sign-on, and data encryption) integrated with the identity and policy services of Access Manager.
Access Gateway is designed to work with Identity Server to enable single sign-on to protected web services. The following features facilitate single sign-on to web servers that are configured to enforce authentication or authorization policies:
-
Identity Injection: Injects the information into HTTP headers that the web server requires.
-
Form Fill: Automatically fills in the requested form information.
If your web servers have not been configured to enforce authentication and authorization, you can configure Access Gateway to provide these services. Authentication contracts and authorization policies can be assigned so that they protect the entire web server or a single page.
Access Gateway can also be configured to cache requested pages. When a user meets the authentication and authorization requirements, the user is sent the page from cache rather than requesting it from the web server, which enhances the content delivery performance.
There are two types of Access Gateways. Both are based on the same core technology and differ only in their deployment method.
Access Gateway Appliance: It is installed as a soft appliance, which includes the operating system.
Access Gateway Service: It requires you to provide the operating system.
Features of Access Gateway Appliance and Access Gateway Service are same but differ from the Linux Access Gateway.
For more information about the differences, see Feature Comparison of Different Types of Access Gateways in the NetIQ Access Manager 4.3 Installation and Upgrade Guide.
For information about how to upgrade your chosen Access Gateway technology, see Upgrading Access Manager in the NetIQ Access Manager 4.3 Installation and Upgrade Guide.
Embedded Service Provider
Access Gateway uses an Embedded Service Provider (ESP) to redirect authentication requests to Identity Server. Identity Server allows only trusted devices to participate. To trust each other, devices must exchange metadata. The Embedded Service Provider performs this task automatically for Access Gateway. The logout requests to Identity Server must be digitally signed.
Figure 1-3 Access Gateway Component
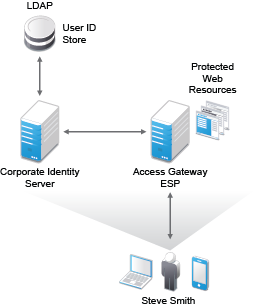
1.3.4 Analytics Server
Analytics Server is a component of Access Manager that analyses the usage, performance, and events of Access Manager. The events are captured and filtered through Analytics Server.
Analytics Server filters and analyzes the events that are generated from the Access Manager components (Access Gateway and Identity Provider). You can view the analyzed information in the following ways:
-
Dynamic graphs in Analytics Dashboard
-
Reports that can be generated in different formats
-
Raw auditing records
Analytics Server helps the administrators to accomplish these purposes with a single soft appliance.
The events that are generated from the Access Manager components (Identity Provider and Access Gateway) are collected, filtered, and saved in Analytics Server, then required events are displayed in Analytics Dashboard. For more information about Analytics Dashboard, see Section 18.0, Analytics Dashboard.
1.3.5 MobileAccess
Access Manager allows to manage users’ access to resource through mobile devices easily. You create appmarks for each of the Access Manager resource that you want your users to access. The appmark acts as a bookmark for the resource. You can control access to your resources no matter the type of device or location of the device.
Access Manager allows you to manage the users’ devices and allows users also to manage their own devices. When users lose devices, you can easily remove access to protected resources from those devices through Administration Console. Users can manage their own devices from a dedicated portal page.
The new user portal page displays any appmarks you have created and assigned to the user through the existing Access Manager roles. The user portal page also presents the different authentication methods assigned to the different resources. Plus you can change easily the branding of the user portal page without editing any JSP files.
1.3.6 User Portal
If you want complex customization of the user portal page, Access Manager provides a customizable user portal page that is an application where end users can access and manage their authentications, federations, and profile data. The authentication methods you create in Administration Console are reflected in the Portal.
Help information for the end users is provided in the user interface. If you know how to customize JSP pages, you can customize the portal for rebranding purposes and for creating custom login pages.