10.5 Managing Events
In the table view, you can manage one or more events. Select the event or events you want to manage, then right-click and select the option.
10.5.1 Showing and Hiding Event Details
To show details in a Real Time Event Table of the Navigator or Snapshot, double-click or right-click an event, then click .
The details display in the left panel of the Real Time Event Table.
To close the Event Details window in a Real Time Event Table of the Navigator or Snapshot, right-click an event, then click .
10.5.2 Sending Mail Messages about Events and Incidents
To send mail messages from within the Sentinel Control Center, you must have an SMTP integrator that is configured with connection information and with the SentinelDefaultEMailServer set to True. For more information on configuring the SMTP Integrator, see Configuring Integrators
in the NetIQ Sentinel 7.0.1 Administration Guide.
To send an event message by e-mail:
-
In a Real Time Event Table, right-click an event or a group of events, then select .
The e-mail is sent to the specified recipients.
To e-mail an incident:
-
After you save your incident, click the tab, > .
-
Click in the drop-down list located at the bottom right corner.
-
Double-click an incident.
-
Click the button.
-
Provide the following information:
-
Email Address
-
Email Subject
-
Email Message
-
-
Click .
The e-mail messages have .html attachments that address incident details, events, assets, vulnerabilities, advisor information, attachment information, incident notes, and incident history.
10.5.3 Creating Incidents
Creating an incident is useful in grouping a set of events together to indicate a pattern of interest, such an attack.
You must have the View or create incidents and add events to incidents permission to create incidents.
If events are not initially displayed in a newly created incident, it is probably because of a lag in the time between display in the Real Time Events window and insertion into the event store. It takes a few minutes for the original events to be inserted into the event store and displayed in the incident.
-
Access the tab.
For more information, see Section 10.2, Accessing the Active Views Tab.
-
In a Real Time Event Table, select an event or a group of events and right-click.
-
Select .
-
Follow the steps in Section 12.2, Creating Incidents.
10.5.4 Adding Events to an Incident
You must have the View or create incidents and add events to incidents permission to add events to Incidents.
-
Access the tab.
For more information, see Section 10.2, Accessing the Active Views Tab.
-
In a Real Time Event Table, select an event or a group of events and right-click.
-
Select .
-
Click , then click to list the available incidents.
You can define your criteria to better search for a particular incident or incidents in the Select Incident window.
-
Select an incident, then click .
-
Click .
If events are not initially displayed in a newly created incident, it is probably because of a lag in the time between display in the Real Time Events window and insertion into the event store. It takes a few minutes for the original events to be inserted into the event store and display in the incident.
10.5.5 Viewing Events That Trigger Correlated Events
-
Access the tab.
For more information, see Section 10.2, Accessing the Active Views Tab.
-
In the Real Time Event Table, right-click a correlated event, then select .
The option is enabled only for Correlated events. Section 10.5.13, Viewing the Targets. The events that generated the correlation event are displayed in the Sentinel Web interface.
10.5.6 Executing Actions on Events
You can execute the following actions on events:
-
Log to File
-
Log to Syslog
-
Send Email
-
Send SNMP trap
-
Send via Sentinel Link
-
Access the tab.
For more information, see Section 10.2, Accessing the Active Views Tab.
-
In a Real Time Event Table, select an event or a group of events, right-click, then select the action you want to execute.
10.5.7 Investigating an Event or Events
You can use the Active Views tab to investigate events in two ways:
-
You can perform an event query for the last hour on a single event for:
-
Other events with the same target IP address
-
Other events with the same source (initiator) IP address
-
Other targets with the same event name
NOTE:You cannot perform a query on a null (empty) field.
-
-
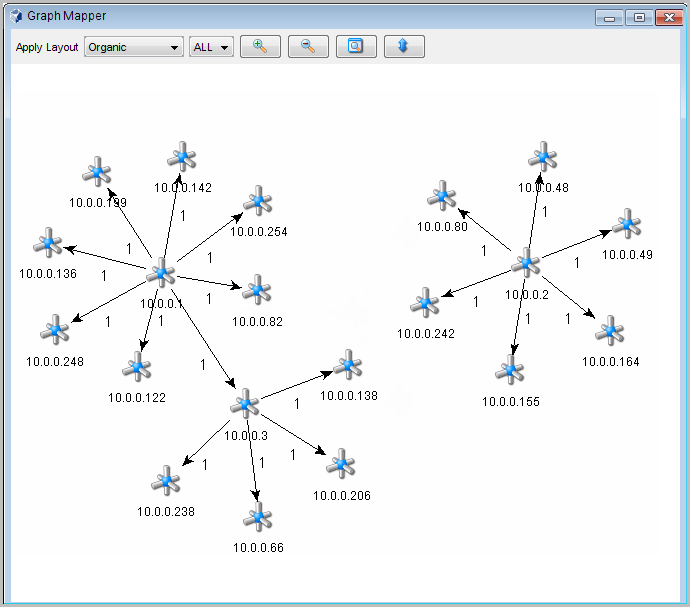
You can graphically display the mappings between any two fields in the selected events. This is particularly useful to view the relationship between the initiatiors (IP, port, event, sensor type, Collector) and the targets (IP, port, event, sensor type, Collector name) of the selected events, but any fields can be used
The following illustration shows initiator IP addresses mapped to target IP addresses.
Figure 10-3 Graph Mapper
Using the Investigate Option for an Event Query
You can perform an event query within the last hour for events similar to the selected event.
-
In a Navigator or Snapshot window, right-click an event, then click and select one of the options below:
Show More Events to this target: Events with the same destination IP address
Show More Events from this source: Events with the same initiator IP address
What are the target objects of this event?: Events with the same event name as the selected event.
The chosen event information is displayed in the Sentinel Web interface.
Using the Investigate Option with the Graph Mapper
To create a graph map:
-
In a Real Time Event Table, right-click one or more events, then select > .
-
Select the desired information in the and fields, then click .
-
In the Graph Mapper window, select how the information is displayed:
-
Circular
-
Hierarchical
-
Organic
-
Orthogonal
-
10.5.8 Accessing the Active Browser
The Active Browser provides the ability to browse through a selected set of data to look for patterns and perform investigation. You can view the selected events in the Active Views in the Active Browser. You can also perform all the right-click activities that are available in Active Views in the Active Browser.
Viewing Events in the Active Browser
-
Access the tab.
For more information, see Section 10.2, Accessing the Active Views Tab.
-
Select the events you want to view in the Active Browser.
-
Right-click the events, then select .
The selected events display in the Active Browser window.
Searching in the Active Browser
-
Access the Active Views tab.
For more information, see Section 10.2, Accessing the Active Views Tab.
-
Specify the value or text you want to search for in the field, then click the button.
You can move between the various searches by using the and buttons above the search field.
Adding Attributes in the Active Browser
-
Access the Active Views tab.
For more information, see Section 10.2, Accessing the Active Views Tab.
-
Click the button.
-
Select an attribute from the list.
-
Click .
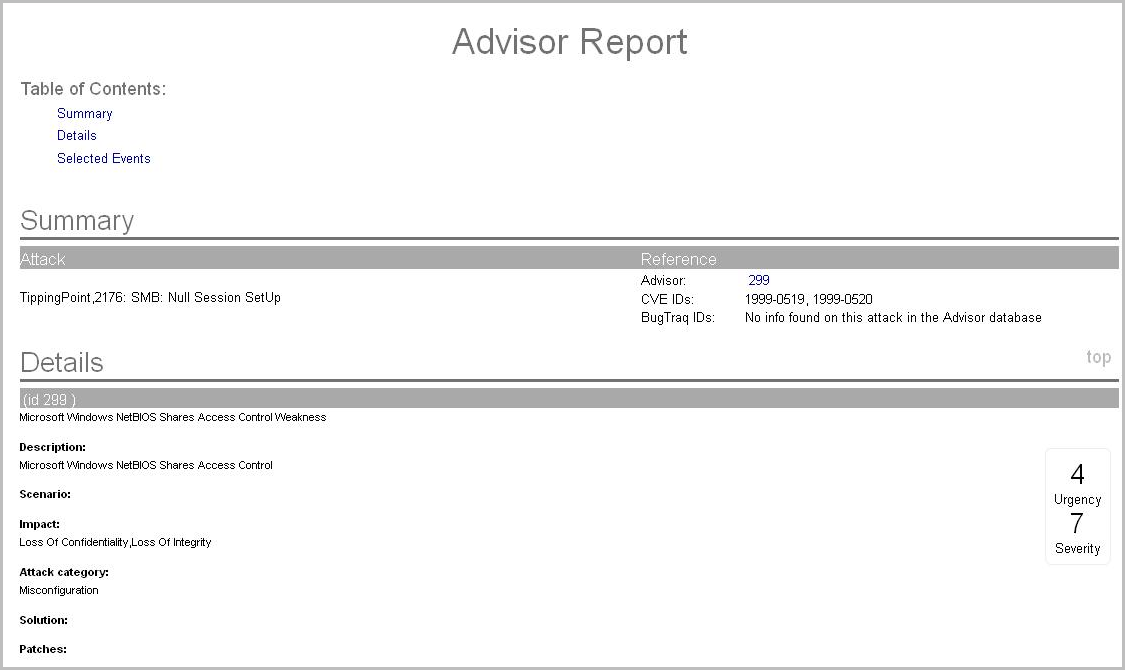
10.5.9 Viewing Advisor Data
Advisor provides a cross-reference between real-time intrusion detection system (IDS) attack signatures and Advisor's knowledge base of vulnerabilities. The supported intrusion detection systems are listed in Configuring Advisor
in the NetIQ Sentinel 7.0.1 Administration Guide.
To view Advisor data:
-
In a Real Time Event Table, right-click one or more events, then click > .
If the field is properly populated, a report similar to the one below is displayed in the Sentinel Web interface.
10.5.10 Viewing Asset Data
This feature allows you to view and save your view as an HTML file of your Asset Report. To view the Asset data, you must run an asset management tool such as NMAP and bring the results into Sentinel by using an Asset Collector. The available data for viewing are:
-
Hardware
-
MAC Address
-
Name
-
Type
-
Vendor
-
Product
-
Version
-
Value
-
Criticality
-
-
Network
-
IP Address
-
Hostname
-
-
Software
-
Name
-
Type
-
Vendor
-
Product
-
Version
-
-
Contacts
-
Order
-
Name
-
Role
-
Email
-
Phone Number
-
-
Location
-
Location
-
Address
-
If both the Source IP and Destination IP are populated in an event, the asset data is displayed for both. If either of them is populated, the respective asset data is displayed.
To view asset data:
-
In a Real Time Event Table, right-click one or more events, then click > .
The Asset data is displayed in the Sentinel Web interface.
10.5.11 Viewing Vulnerabilities
Vulnerability Visualization provides a textual or graphical representation of the vulnerabilities of selected destination systems. Vulnerabilities for the selected destination IPs can be seen for the current time or for the time of the selected events.
Vulnerability Visualization requires that a vulnerability Collector is running and is adding vulnerability scan information to the Sentinel database. The Sentinel Plug-in Web site provides Collectors for several industry-standard vulnerability scanners, and additional vulnerability Collectors can be written by using the Collector Builder.
NOTE:Vulnerability Collectors are distinct from Event Collectors and use different commands.
There are several Vulnerability Visualization views:
-
HTML
-
Graphical
-
Circular
-
Organic
-
Hierarchical
-
Orthogonal
-
The HTML view is a report view that lists relevant fields, depending on which vulnerability scanner you have:
-
IP
-
Host
-
Vulnerability
-
Port/protocol
The graphical display is a rendering of vulnerabilities that links them to an event through common ports. There are four available views:
-
Organic view
-
Hierarchical view
-
Circular view
-
Orthogonal view
The graphical display has four panels:
-
Graph panel
-
Tree panel
-
Control panel
-
Details/events panel
The graph panel display associates vulnerabilities to a port/protocol combination of a resource (IP address). For example, if a resource has five unique port/protocol combinations that are vulnerable, there are five nodes attached to that resource. The resources are grouped together under the scanner that scanned the resources and reported the vulnerabilities. If two different scanners are used, such as ISS and Nessus, there are two independent scanner nodes that have vulnerabilities associated with them.
NOTE:Event mapping takes place only between the selected events and the vulnerability data returned.
The tree panel organizes data in same hierarchy as the graph. The tree panel also allows users to hide or show nodes at any level in the hierarchy.
The control panel exposes all the functionality available in the display. This includes:
-
Four different algorithms to display
-
The ability to show all or selected nodes that have events mapped to them
-
Zooming in and out of selected areas of the graph
There are two tabs. When you are in the tab, click on a node displays node details. When you are in the tab, clicking an event associated with a node displays a table in a Real Time window.
To run a vulnerability visualization:
-
In a Real Time Event Table, right-click one or more events, then click and select one of the following options:
Current Vulnerability: Queries the database for vulnerabilities that are active (effective) at the current date and time.
Event Time Vulnerability: Queries the database for vulnerabilities that were active (effective) at the date and time of the selected event.
10.5.12 Viewing User Information
NetIQ provides optional integration with Novell Identity Manager. With this integration, user identity information is added to incoming events when the account name matches one from Novell Identity Manager. When the InitUserIdentity or TargetUserIdentity column is populated in an event, a right-click menu is enabled to open the user’s page in the Identity Browser.
When you right-click an event and select , you can choose to view the identity of the Initiator user, the Target user, or both. The Identity Browser opens and shows identifying information about the user (or users) from the identity management system, all the accounts to which the user is provisioned, and the recent activity by that user. For more information on the Identity Browser, see Section 7.0, Integrating Identity Information with Sentinel Events.
10.5.13 Viewing the Targets
You can view the targets of the events in the Real Time Event Table.
-
In an existing Real Time Event Table, right-click an event, then click .
-
Select one of the following options:
The selected information is displayed.
-