12.8 Event Configuration
12.8.1 Event Mapping
Event Mapping is a mechanism that allows you to add data to an event by using data already in the event to reference and pull in data from an outside source. The outside data source is a map, which is defined by using Map Data Configuration. The data already in the event that should be used as the reference into the map and the data to be pulled from the map into the event are specified by using the tab.
Because virtually any data set can be made into a map, Event Mapping is useful for incorporating data from elsewhere in your organization into the event stream. Some opportunities Event Mapping provides are:
-
Regulatory compliance monitoring
-
Policy compliance
-
Response prioritization
-
Enabling security data to be analyzed related to business operations
-
Enhancing accountability
When an Event Mapping is defined, it is applied system-wide to all events from all Collectors. Additionally, Sentinel automatically distributes map data to all processes that perform event mappings as well as keeping the map data in these processes up-to-date. For these reasons, Event Mapping provides significant capabilities to support enterprise deployments.
Event Mapping is made up of four main parts:
-
Controller: Stores all map information
-
Distributor: Automatically redistributes modified maps to those processes that registered for the map
-
Monitor: A monitor to detect changes in map source data
-
Generator: Generates maps from source data
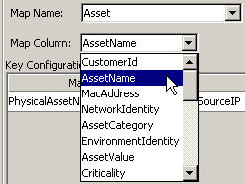
One application of Event Mapping is Sentinel's Asset Data functionality. For example, asset information is collected and stored in the Sentinel Database asset schema and is represented by a Physical Asset Entry. Soft assets, such as services and applications, are represented by an entry that is linked to a physical asset. The primary automated update mechanism for asset data is through an asset Collector reading data from a scanner such as Nmap. The asset Collector automates the retrieval of asset information by reading asset data from the scanner and populating the asset schema tables with this data. For Event Mapping, asset information is mapped from the destination IP and source IP.
There are two types of data sources:
-
External: A Collector populates the value in the event tag.
-
Referenced from Map: Data is retrieved from a map to populate the tag.
Figure 12-15 Data Sources
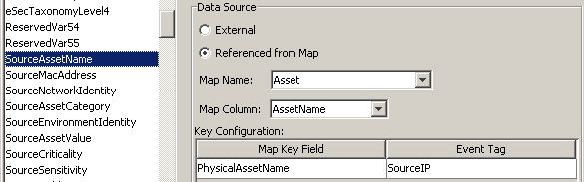
In the above illustration, the SourceAssetName tag is populated from the map called Asset (which has asset.csv as its map data source file). The specific value for SourceAssetName is taken from the AssetName column from the Asset map. The PhysicalAsssetName column is set as the key. When the InitIP tag of the event matches one of the source IP values in the PhysicalAsssetName column of the map, the row with the matching key is used to intersect the AssetName Column. For instance, in the following example the IP corresponds to AssetName Finance35.
NOTE:When a column is set as a key, it does not appear in the Column drop-down field.
Figure 12-16 Physical Assent Name Corresponds to the Asset Name

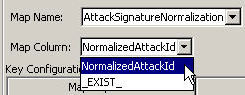
You can have more than one column set as a key if you do not want the map to be a range map (range maps can only have one key column, with that column type set to NumberRange). For instance (with the column type set to String) the AttackId tag has the DeviceName (name of the security device) and DeviceAttackName columns set as keys and uses the NormalizedAttackID column in the AttackNormalization map for its value. In a row where the DeviceName event tag matches the data in the Device map column and the DeviceAttackName matches the data in the AttackSignature map column, the value for AttackId is the value in the NormalizedAttackID column. The configuration for Event Mapping just described is as follows:
Figure 12-17 Event Mapping Configuration
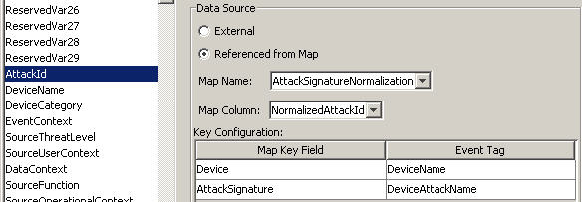
Figure 12-18 Device and Attack Signature Corresponds to the Asset Name
To configure event tags (columns) to use mapping:
-
Navigate to the Admin tab and click Event Configuration in the navigation pane or click the Event Configuration button.
-
Select an event tag entry from the Event Columns list.
The original Event Tag name displays above the Label field. In addition, the description of the event column is provided.
-
Click Referenced from Map to configure the event tag to be populated with data from a map.
or
Click External to keep whatever value the Collector put in the event tag (if any).
-
Click the Map Name field down-arrow.
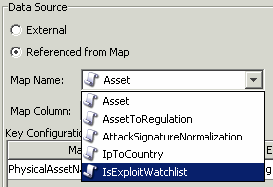
Select one of the available default maps or select a map you have created.
-
Click the Map Column field down-arrow and select a Map Column name. Depending on your Map Name choice in the previous step, these values vary.
-
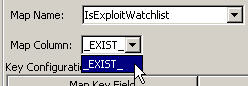
_EXIST_ : This is a special map column that exists in every map. If this map column is selected, a “1” is placed in the event tag if the key is in the map data. If the key is not in the map data, a “0” is placed in the event tag.
-
All other choices: Names of active columns within the map definition that are not set as a key (for example, the CustomerId column in Asset or the NormalizedAttackId column in AttackNormalization)
-
-
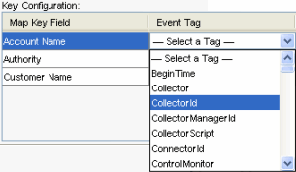
In the key configuration, select the event tag for each row in the table in the Event Tag column that will be matched against the map key column specified in the corresponding Map Key Field column. The rows in the Key Configuration table depend on the Map Name selected.
A key is a unique identifier for the row of data in the map data.
-
Click .
Clicking Apply saves the changes you made for the currently selected event column in a temporary buffer. If you don't click Apply, the changes you made to the previously selected event column are lost when you select a different event column. Changes won’t be saved to the server until you click Save.
-
If you want to edit the event mapping of another Event column, repeat Step 2 through Step 7.
Remember to click Apply after editing the Event Mapping of each Event column.
-
Click Save.
Clicking Save saves your changes to the server. The save function saves all changes stored in the temporary buffer.
12.8.2 Renaming Tags
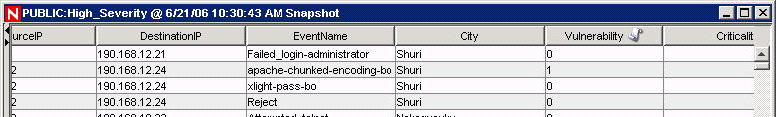
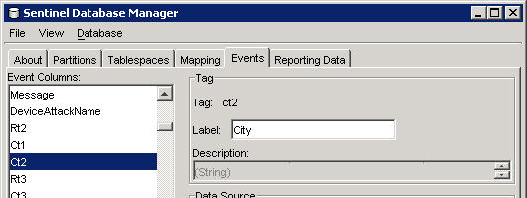
The Event Configuration window also allows you to assign names to existing event tag labels. For example, you can rename the label for event tag Ct2 to City. Doing this results in the event tag that formerly appeared in the Sentinel Control Center as Ct2 to now appear as City. Event tags appear in the Sentinel Control Center in places such as filters, correlation rules, and Active Views.
Renaming tags does not change the name of the variable in Collector scripts or in internal Sentinel representations of the tag. For example, even if the event tag labeled Ct2 is renamed to City, the variable that must be used in a Collector script to reference this meta tag is still s_CT2. Any references to this variable in correlation or filters still work, even if they were originally written using Ct2.
Below is a before and after illustration of this feature in an Active View.
Figure 12-19 Active View Window: Before
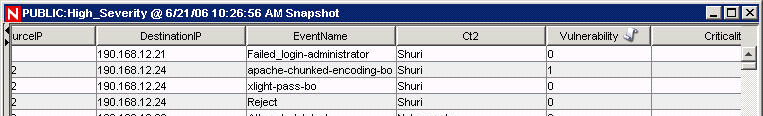
Figure 12-20 Active View Window: After
To rename an event column:
-
Click Event Configuration in the navigation pane or click the Event Configuration button.
The original Event Column name displays above the Label field. In addition, the description of the event column is provided.
-
Select an event column entry.
-
Specify a new value for your Event Column in the field.
-
Click .
Clicking Apply saves the changes you made for the currently selected event tag in a temporary buffer. If you don't click Apply, the changes you made to the previously selected event tag are lost when you select a different event tag. Changes aren’t saved to the server until you click Save.
-
Click .
Clicking saves the changes to the server. The save function saves all changes stored in the temporary buffer.
-
In order for changes to be visible in Sentinel Control Center, close and reopen any Sentinel Control Centers that are running.