14.3 iTRAC
This section gives and idea relevant to iTRAC.
14.3.1 Instantiating a Process
An iTRAC process can be instantiated in the iTRAC server by associating an iTRAC process to an incident the following methods:
-
Associate an iTRAC process to the incident at the time of incident creation
-
Associate an iTRAC process to incident after an incident has been created
-
Associate an iTRAC process to an incident as an action when deploying a correlation rule
For more information on association a process to an incident, see Section 3.0, Correlation Tab and Section 4.0, Incidents Tab.
Example Scenario – Creating a Simple Two Tiered iTRAC Process for a Possible Network Attack
NOTE:To perform all of the scenarios in the iTRAC section, iTRAC scenario sections must be followed in the order presented.
This discusses how to make a simple two tiered iTRAC Process. The process is flow of steps that can be taken in the event there is a possible attack on your system.
The example process is:
-
Asks the question (in the first step – a manual step [Decide if Hacked]), from a preliminary look has the network been attacked? This leads to a Decision Step.
NOTE:All Decision Steps provide different execution paths depending on the value of the variable defined in the previous step.
-
If there has been an attack, go collect necessary data to determine if there has been an attack. If there is no attack, send an email out to the supervisor that there is not an attack.
-
The Collect Data step is to review the data to make a better determination if there has been an attack.
-
If there has been an attack, take measures to prevent another attack and send an email out to the supervisor that proper measures have been taken. If there is no attack, send an email out to the supervisor that there is not an attack.
Figure 14-3 iTRAC Process

To Create an iTRAC Process:
-
Click the iTRAC tab.
-
In the navigation pane, click iTRAC Administration > Template Manager.
-
In the Template Manager window, click Add.
-
The iTRAC Process Builder displays with a Process Details window. Provide the name iTRAC Tutorial. Optionally, add a description.

-
From the Step Palette pane, drag and drop three Manual Steps, two Mail Steps, and two Decision Steps. Rename and the attributes to the steps as follows by right-clicking and selecting Edit Step.
-
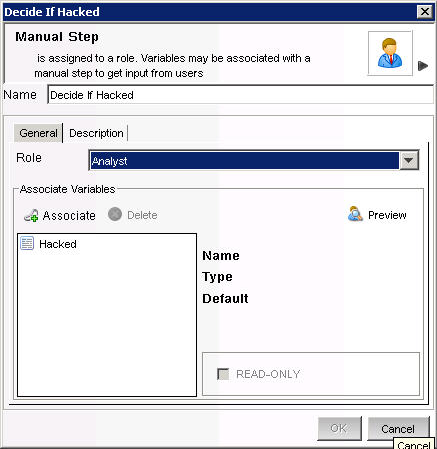
Manual Step-0 to Decide If Hacked
-
set Role to Analyst
-
click Associate
-
click Add
-
provide Hacked in the Name field
-
in the Process Variables window select the Variable Type as String
-
provide Default Value as yes

-
under the Description tab, (optional) specify Initial evaluation of event(s) to determine if there has been an attack
-
click OK
-
highlight the newly created association, continue to click OK until the step is renamed
-
-
Manual Step-1 to Collect Data
-
set Role to Analyst
-
click Associate
-
highlight Hacked, click OK
-
under the Description tab, (optional) specify To further evaluate after collecting of events to determine if there has been an attack.
-
click OK, the step should be renamed
-
-
Manual Step-2 to Prevent Future Attacks
-
set Role to Analyst
-
under the Description tab, (optional) specify Take measures to stop the attack (firewall, router or other intrusion protection method). Also, if possible, determine how the attacked was done.
-
click OK, the step should be renamed
-
-
Mail Step-3 to Not Hacked
-
in the To field, (because this is for tutorial) provide your email address. When this step completes it will send you an email
-
in the From field, provide a made up address such as me@nowhere.com
-
in the Subject field, specify We have not been hacked.

-
Under the Body tab, (optional) specify This email is generated from a tutorial (simulation) iTRAC process.

-
click OK
-
-
Mail Step-4 to Prevent Future Attacks
-
in the To field, specify your email address
-
in the From field, specify a made up email address
-
in the Subject field, specify Proper Attack Measures Taken
-
Under the Body tab, (optional) specify This email is generated from a tutorial (simulation) iTRAC process.
-
-
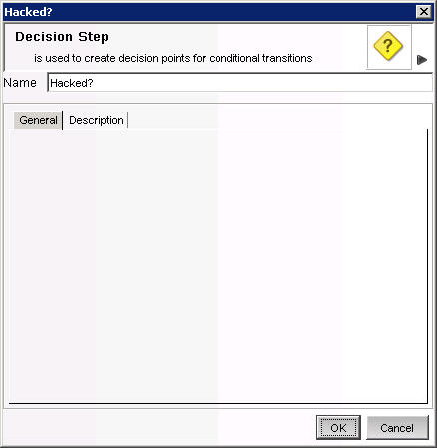
Decision Step-5 to Hacked? (optional) Under the Description tab, (optional) provide a description such as Preliminary decision as to if there has been an attack or not.
-
Decision Step-6 to Hacked or Not. (optional) Under the Description tab, you might provide a description such as Decision as to if there has been an attack or not.

-
-
Right-click Start and select Add Start Transition. Select destination to step Decide If Hacked.
-
Right-click Decide If Hacked and select Add Transition. Select and specify the following:
-
Name, provide Decision
-
Type, select Unconditional
-
Destination: Hacked?

-
Click OK
-
-
Right-click Hacked? and select Add Transition. Select and specify the following:
-
Name, provide Not Hacked
-
Type, select else
-
Destination: Not Hacked
-
Click OK
NOTE:A decision step provides different execution paths depending on the value of the variable defined in the previous step. A Decision Step can have more than two transitions.
-
-
Right-click Not Hacked and select End Transition.
-
Right-click Hacked? and select Add Transition. Select and specify the following:
-
Name, provide Hacked
-
Type, select Conditional
-
Destination: Collect Data

-
Click Set > EXP
-
Select Variables and Values
-
Select Attribute Hacked
-
Select Condition equals
-
Specify Value of yes

-
-
Click OK until the transition is complete
-
-
Right-click Collect Data and select Add Transition. Select and specify the following:
-
Name, Hacked or Not?
-
Type, Unconditional
-
Destination, Hacked or Not
-
-
Right-click Hacked or Not and select Add Transition. Select and specify the following:
-
Name, Not Hacked
-
Type, Else
-
Destination, Not Hacked
-
-
Right-click Hacked or Not and select Add Transition. Select and specify the following:
-
Name, Hack Happened
-
Type, Conditional
-
Destination, Prevent Future Attacks
-
Click Set > EXP
-
Select Variables and Values
-
Select Attribute Hacked
-
Select Condition equals
-
Specify Value of yes
-
-
Click OK until the transition is complete
-
-
Right-click Prevent Future Attacks and select Add Transition. Select and specify the following:
-
Name, Proper Measures Taken
-
Type, Unconditional
-
Destination, Measures Taken
-
-
Right-click Measures Taken and select Add End Transition.

-
Click Save. Your new process should appear in the Template Manager.
Example Scenario – Running an iTRAC Process for a Possible Network Attack
The following example assumes the following:
-
A process named iTRAC Process Tutorial has been assigned to your role (analyst)
NOTE:This is a process created in Section. Example Scenario – Creating a Simple Two Tiered iTRAC Process for a Possible Network Attack.
-
All steps within the process belong to the Analyst group
NOTE:By assigning steps to other roles, will mean having to log out and then log in as a user assigned to that role and accept the process. For simplicity, the following example is assigned to one role.
To run this process, this process must first be assigned to an incident.
To Start or Terminate a Process:
-
Click the Incident tab.
-
Click Incidents > Create Incidents.
-
Specify the following:
-
Title: iTRAC Tutorial
-
Category: Other
-
Responsible: assign this Incident to yourself
-
-
Click the iTRAC tab, select iTRAC Process Tutorial.
-
Click Create.
NOTE:Because this is a tutorial Incident and not a true Incident, it can be deleted without negatively affecting your Sentinel setup.
-
From anywhere in the Sentinel GUI, click the Analyst group (yellow bar) under View work items.

NOTE:Your bar might already be partially green indicating that you have accepted (acquired) an iTRAC Process.
-
All of the processes assigned to the Analyst role displays.

-
To accept a Work Item, highlight iTRAC Tutorial and click Acquire.

If the View Work Item list bar was yellow as illustrated above, it changes with an addition of a green bar.

-
Click the green bar under View work items. In the Work Items window, click View Details.
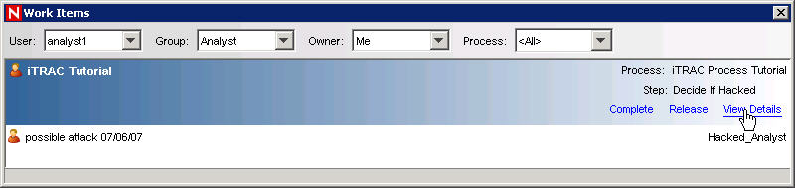

The red highlighted step indicates what step this process is currently in.
-
To start the steps within this process, click the Process Details tab.

For this manual step the variable yes is specified. Providing another value such as no or else (no attack) will result in going to an email that will send an automatic email and complete the process. Let say that initial assessment is that there is an attack, with the hacked variable equal to yes, click Complete (to complete this step, not complete the process).
-
In the Work Items window, highlight the process and click View Details. The Collect Data step should be highlighted in red. As before, this is a manual step.

-
Click the Process Details tab.
-
Again, the variable page displays. In the previous step of the iTRAC Process, Collect Data is a step to further determine by analyzing the event(s) of interest if an attack has occurred. Let’s say that an attack has occurred. Leave the default value of yes. If this were a real attack, it will be beneficial to add clear notes and/or attachments as to the information about this attack. Click Complete.
-
In Work Items window, highlight the process and click View Details. The Prevent Future Attacks step should be highlighted in red. As before, this is a manual step.
-
In this manual step, measures should be taken to harden the network to prevent future attacks. When this is done, as before it will be beneficial to add clear notes and/or attachments as to the information about this attack. Click Complete.
The next step is an automatic email step indicating that proper anti-attack measures have been taken. The iTRAC Process will be removed from the Work Items window.
Also, if you go to the Process View window it indicates as Complete or if you double-click this process, it indicates as Complete.

