5.1 Overview
Correlation adds intelligence to security event management by automating analysis of the incoming event stream to find patterns of interest. Correlation allows you to define rules that identify critical threats and complex attack patterns so that you can prioritize events and initiate effective incident management and response.
5.1.1 How Correlation Works
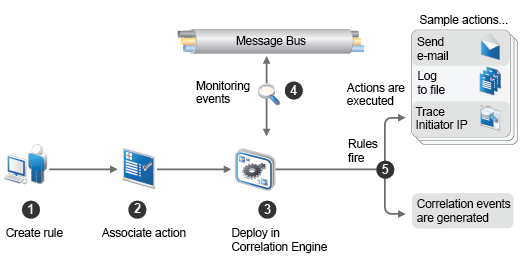
The following illustration shows how Correlation works:
Figure 5-1 Correlation Workflow
-
A user creates a Correlation rule.
-
The user associates one or more actions to the Correlation rule.
-
The user deploys the rule in the Correlation Engine.
-
The Correlation Engine processes events from the real-time event stream to determine whether they should trigger any of the active rules to fire the associated actions.
-
If events match the rule criteria, correlation events are generated and associated actions are executed.
Sentinel’s correlation is near real-time and depends on the time stamp of the individual events. When an event arrives at the Correlation Engine, the engine reorders the events in a buffer based on the event time stamp (dt) field so that the events are evaluated in time order. This is done partly to evaluate sequence rules in which the rule only fires if events occur in a specific order.
The buffer is 30 seconds long, so if the event time stamp (dt) is more than 30 seconds older than the Collector Manager time stamp, the event is not evaluated. To minimize false time differences, you must use an NTP (Network Time Protocol) server to synchronize the time settings on the relevant machines. For more information, see Configuring Time
in the NetIQ Sentinel Installation and Configuration Guide.
5.1.2 Correlation Rules
Correlation rules define a pattern of events that should trigger a rule. You can create rules that range from simple to extremely complex. For example:
-
High severity event from a finance server
-
High severity event from any server brought online in the past 10 days
-
Five failed logins in 2 minutes
-
Five failed logins to the same server from the same username in 2 minutes
-
Intrusion detection event targeting a server, followed by an attempted login to root originating from the same server within 60 seconds
-
A service stop event is not followed by the service start within 5 minutes
A rule can have one or more subrules:
Simple Rule
The simple rule has just one subrule. You can specify additional criteria if you want the rule to fire when all or any of the specified criteria are met. You can also specify the number of times the event should occur for the rule to fire. For example, to monitor a situation with five failed logins within a minute on a finance server.
For information on creating a simple rule, see Section 5.4.2, Creating a Simple Rule.
Sequence Rule
The Sequence rule has two or more subrules that fire in a sequence. You can use a Sequence rule when you want the rule to fire if its subrules meet the specified criteria in the specified sequence within the defined time frame. For example, to monitor a situation where there has been a successful login after three failed logins by the same user within five minutes.
The Sequence rule can also fire even when a single event can satisfy multiple or all of the subrules within the time frame and the times at which they were satisfied are in ascending order. For information about creating a Sequence rule, see Section 5.4.3, Creating a Sequence Rule.
For more information on Sequence rule expression syntax, see Section B.2.5, Sequence Operation.
Composite Rule
The Composite rule has two or more subrules that fire according to the criteria you define. There are two types of Composite rules:
-
Composite (AND): Indicates that all subrules must fire.
-
Composite (OR): Indicates that a specified number of subrules must fire.
For example, you can create a Composite (AND) rule to monitor a situation where there have been failed logins on a finance server and a database server within two minutes.
Similarly, for example, you can create a Composite (OR) rule, if you have three or more subrules and you want the rule to fire if a maximum of two subrules meet the specified criteria.
The Composite rule can also fire even when a single event can satisfy multiple or all of the subrules. For information on creating a Composite rule, see Section 5.4.4, Creating a Composite Rule.
For information about Composite rule expression syntax, see Section B.2.4, Gate Operation.
Sequence Timeout Rule
The Sequence Timeout rule fires when an event that matches the first subrule is not followed by an event that matches the second subrule in a specified time frame.
For example, you can create a Sequence Timeout rule to detect a scenario where the server stopped but did not start again within an interval of 5 minutes.
Similarly, you can also create a Sequence Timeout rule to detect a scenario where a firewall security update started but was not followed by successful installation of updates within the specified time interval.
For information about creating a Sequence Timeout rule, see Section 5.4.5, Creating a Sequence Timeout Rule.
For information about Sequence rule expression syntax, see Section B.2.6, Sequence Timeout Operation.
Free-form Rule
If you are familiar with the rule expression syntax, you can create correlation rules by manually specifying the rule expression. You can use free-form rules to create complex rules by using additional operators such as Window, Intersection, and Union.
For information about the rule expression syntax, see Section B.0, Correlation Rule Expression Syntax.
For information about creating a free-form rule, see Section 5.4.6, Creating a Free-Form Rule.
Combining Different Rule Types
You can create correlation rules with a combination of different rule types to detect complex scenarios.You can create rule combinations such as a Sequence rule with a Composite rule or a Sequence Timeout rule with a Sequence rule, and so on. You can create a combination of different rule types either by using the free-form view or by using a combination of structured view and the free-form view.
Consider a scenario where you want a correlation rule to fire when a system scan (Event A) detects a virus (Event B), but is not followed by a quarantine (Event C) in 30 seconds. The overall timeframe for this complete activity is 1 hour. For this scenario, you can create a combination of Sequence and Sequence Timeout rules.
For information about combining different rule types, see Section 5.4.7, Creating a Combination Rule.
5.1.3 Correlation Engine
To monitor events according to the correlation rules, you must deploy the rules in the correlation engine. When an event occurs that satisfies the rule criteria, the correlation engine generates a correlation event describing the pattern.
NOTE:Events that are sent directly to the event store or dropped by event routing rules are not processed by the correlation engine.
The Sentinel correlation engine provides specific advantages over database-centric correlation engines.
-
By relying on in-memory processing rather than database inserts and reads, the correlation engine performs during high steady-state volumes as well as during event spikes when under attack, which is the time when correlation performance is most critical.
-
The correlation volume does not slow down other system components, so the user interface remains responsive, especially with high event volumes.
-
The correlation engine can add events to incidents after an incident has been created.
-
You can deploy multiple correlation engines, each on its own server, without the need to replicate configurations or add databases. The correlation engine is built with a pluggable framework that allows the addition of new correlation engines. Independent scaling of components provides cost-effective scalability and performance.
NOTE:You cannot install more than one correlation engine on a single system. You can install additional correlation engines on remote systems, and then connect them to the Sentinel server.
For more information about installing the Correlation Engine, see “Installing Collector Managers and Correlation Engines” in NetIQ Sentinel Installation and Configuration Guide > Installing Sentinel.