8.5 Lost Card Scenarios
8.5.1 Lost Card Scenario Preference
The option determines how SecureLogin handles a user forgetting, losing or damaging a smart card. The option can only be used if, the option is enabled, that is set to either or .
NOTE:For users upgrading from Novell SecureLogin version 5.5, setting to is equivalent to setting the old to .
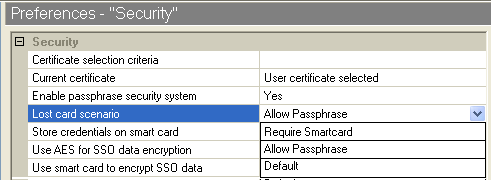
If the lost smart card is used to encrypt single sign-on data and a card is lost, stolen, or damaged, and key escrow or recovery is not used, the user does not have access to single sign-on data unless is set to or .
-
If is set to , if the user has previously set a passphrase, and if is set to , the user is prompted to answer with his or her passphrase before SecureLogin is available.
-
If is set to , the user is not prompted for the answer and SecureLogin loads seamlessly.
Allow Passphrase
This preference allows the user to start Novell SecureLogin using their passphrase if their smart card is not available. The preference must be set to Yes or Hidden for this to work. Hidden replaces a user-generated passphrase with a system-generated passphrase, effectively removing the need for the user to remember the passphrase answer.
IMPORTANT:For the user to decrypt data using their passphrase, the passphrase must already have been set. Administrators cannot simply toggle the preference on the day the user forgets their smart card unless the user has previously set a passphrase (or had it randomly generated using Hidden).
NOTE:Administrators can manually disable inheritance of higher level preferences by selecting the Yes option for in the Novell SecureLogin Administrative Management Utility, Preferences – General options.
Default
The default preference is to allow the user to start Novell SecureLogin using their passphrase, unless it inherits a preference from a higher-level container.
8.5.2 Requiring a Smart Card
The option prevents a user from starting single sign-on without his or her smart card. This option is for high security implementations where organizations want to tie the use of a user's single sign-on credentials to the user's smart card. This means that the user cannot access single sign-on with any other method; that is, they cannot use a username and password without the smart card.
IMPORTANT:If the option is changed while the user is logged in, refreshing the cache using the > option from the taskbar does not refresh the option.
The user must log out and log in again (or restart SecureLogin) for the new option to take effect.
8.5.3 Allowing a Passphrase
The option must be used in conjunction with the option. It allows the user to start SecureLogin by using a passphrase if the smart card is not available. The passphrase security system must be set to or for this setting to apply.
The option replaces a user-generated passphrase with a system-generated passphrase, effectively removing the need for the user to remember the passphrase answer.
IMPORTANT:For the user to decrypt data using a passphrase, the passphrase must already be set. You cannot simply toggle the to on the day the user forgets a smart card unless the user has previously set a passphrase (or had it randomly generated by using the option).
The option allows the user to start SecureLogin by using a passphrase if the smart card is not available through the option. Alternatively, this option inherits the preference set by the higher-level container.
You can manually disable inheritance of higher-level options by selecting the option for (SecureLogin Administrative Management utility > > options.)
8.5.4 Passphrases for Temporary Access
There are a number of options available that permit access if a user loses or forgets his or her smart card. For example, If a user loses or forgets his or her smart card and the option is set to , you can grant temporary access to systems by resetting the user's password. The user is then required to log in and enter the passphrase. This option is possible only if the is turned on.
However, the user should not expect easy or automatic access to the system. Users should understand that, a strong and secure solution has been implemented and that they have the responsibility of looking after their own smart cards.
8.5.5 Using a Card Management System
Enterprise server or web-based card management system (CMS) software enables corporations to implement and easily manage smart card-based identity management, provisioning, and authentication devices and enforce policy across geographically-dispersed locations.
These systems provide a complete and flexible solution to manage the issuance, administration, and configuration required for the successful and seamless smart card integration with SecureLogin 6.0 and later and Smart Card Password Login.
Novell CMS provides a complete and flexible solution to manage the issuance, administration and configuration required for a successful and seamless smart card integration with Novell SecureLogin and Smart Card Password Login (SCPL). It can be configured to perform key escrow, archive and recovery as described throughout this document.
Restoring a Smart Card Using Card Management System
You must then reset the user's corporate passwords and issue a new smart card (with a new key pair) before the user can log in and reconfigure the single sign-on applications using SecureLogin again.
The user must manually enter all application credentials into SecureLogin the first time he or she logs in after the data was cleared from the directory.
Enterprises should consider implementing key escrow, archiving, or backup through a suitable CMS to allow a user's encryption key to be recovered in the event of a lost or damaged smart card. The use of a CMS is crucial if an enterprise opts to deploy corporate smart cards with a very high level of security by disabling the combined with using the set to and the data options of or .
In the event of a lost or damaged smart card, the user can never decrypt their single sign-on data because the key stored on the smart card is not recoverable.
It is recommended that you extensively test the CMS and smart card restoration techniques before selecting the high security options described above that tie single sign-on to the user's smart card.
The procedure to reset a user’s data store is described in Section 2.6, Deleting or Re-setting User Data.
Accessing Without a Card Management System
If an enterprise opts to deploy corporate smart cards without a suitable card management system (CMS) user key escrow, archiving, and backup system combined, you can still create a very high level of security by setting to and selecting the options of or options. However, in the event of a lost or damaged smart card the user can never decrypt the single sign-on data because the key stored on the smart card is not recoverable.
WARNING:Deleting the user's single sign-on datastore permanently deletes the user's corporate applications, credentials, options, and user policies.
If you still decide to delete the user's existing single sign-on configuration data store, delete it from the > tab.
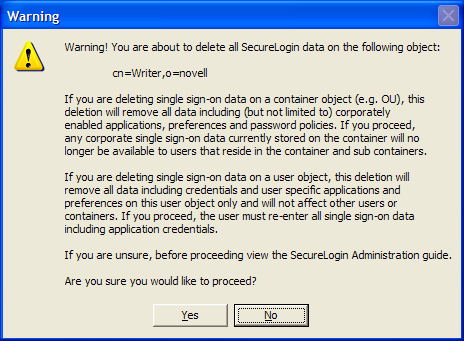
The administrator must then reset the user’s corporate passwords and issue a new smart card (with a new key pair) before the user can log on and reconfigure their single sign-on enabled applications using Novell SecureLogin again.
The user will have to re‑enter all their application credentials into Novell SecureLogin the first time it is used after having them deleted from the directory.
PKI Credentials
If the data option is set to use to encrypt a user's single sign-on data and is set to , in the event of a lost or damaged smart card the user can never decrypt the single sign-on data because the key stored on the smart card is the only key that can be used for decryption and is not recoverable unless key archiving and recovery are implemented.
If a CMS-based key archive is used, then the encryption key needs to be recovered to the new smart card, the single sign-on data unencrypted, and an administrator needs to chose a new certificate to encrypt the user’s data.
If you are using the enterprise CMS-based recovery system, you must issue the user a replacement smart card based on a CMS backup of the user's original key.
Key Generated on Smart Card
Similarly, if the data option is set to use to encrypt a user's single sign-on data, then in the event of a lost or damaged smart card the user can never decrypt the single sign-on data because the key stored on the smart card and is not recoverable.
You should consider setting the option to when the option is used to provide an alternative mechanism for decrypting single sign-on data if the smart card is lost/stolen/damaged.
Using the enterprise CMS-based recovery system, the administrator must issue the user a replacement smart card based on a CMS backup of the user's original key. The replacement card includes the recovered private key and a new key pair so data can be decrypted using the old key and re-encrypted using the new key.