1.0 Introduction to Risk Service
Risk Service evaluates the risk level during each access attempts using the contextual information without influencing the end-user experience. For example, the contextual information can be IP address and device information. This enhances the authentication and access processes, user governance, and prevents fraudulent access to the secured web application or network.
Risk Service uses deterministic, rule-based computation. It enables organizations to find threats quickly with known attack patterns and take appropriate actions. You can integrate your access management solution with Risk Service to assess the risk based on the contextual information associated with an access attempt. You can define an appropriate action for each risk level. For example, granting access or asking for additional authentication.
To enable the unknown threat or anomaly detection, Risk Service integrates with ArcSight Intelligence (formerly Interset) to leverage its User and Entity Behavioral Analytics (UEBA) capability. Using the organization's data, Interset establishes the normal behavior for the organizational entities and then, using advanced analytics and machine learning, identifies the anomalous behaviors that constitute potential risks such as compromised accounts, insider threats, or other unknown cyber threats.
For more information about UEBA and its integration with Risk Service, see the following resources:
In this section:
Risk Service Key Terms
|
Term |
Description |
|---|---|
|
Rule |
A rule indicates a condition that you want to evaluate the risk associated with each login attempt. For evaluation, a rule is assigned to a risk policy. You can assign a single rule to multiple risk policies. You can combine multiple rules in a risk policy. |
|
Risk Policy |
A risk policy is a group of risk rules. Ensure to assign a rule to a risk policy for the evaluation process. You can combine multiple rules in a risk policy. |
|
Risk Score |
The value that is returned when the rule condition is not met. By default, a user's risk score increases by 100 for each failed rule condition. The higher the score, the higher is the risk. In the advanced mode, you can fine-tune the risk assessment by changing the risk score of a rule from 100 to another value. This helps you alter the weightage of that rule compared to other rules in the policy. |
|
Is/Is Not condition |
When you configure a rule and select a parameter for assessment, you can determine how the conditions must match for each of the sub-parameters. For example, if you configure a rule to assess the IP address of a user, you can configure whether the IP address must be specific, be in a range, or be in a particular subnet. If you want to assess whether the IP address of a user is within a range of 10.10.10.1 to 10.10.10.10, you can specify the Is condition in the rule configuration. This indicates that when the rule is evaluated, only IP addresses in the range of 10.10.10.1 to 10.10.10.10 will be considered as a valid IP addresses. During the rule evaluation, if you want a rule to be passed when it does not meet a specific criteria, select Is Not in the rule configuration screen. For example, if you want to stop all login attempts from a particular IP address, configure the rule using the Is Not condition. |
|
Risk Level |
A risk level indicates the status of each login attempt that the risk service returns after comparing the parameters associated with each attempt against the defined rules in a policy. You can configure the risk level based on the number of rules that failed during evaluation. The available risk levels are low, medium, and high. For example, define a policy with three rules and set the risk level as follows:
For each risk level, you can define a subsequent action. |
|
Action If Condition Succeeds |
When a policy contains more than one rule, you can make a specific rule as a decisive rule and define an action if that rule condition succeeds. Actions available are:
For example, a policy contains IP Address Rule and User Last Login Rule. You want the policy to evaluate the IP address Rule first. If the rule meets the condition, allow access without validating another rule in the policy. To promote the IP Address Rule as the decisive rule, select the IP Address Rule, click the Rule Action icon, and select Allow Access. Risk Service executes the IP Address Rule first. If the rule meets the defined condition, the User Last Login Rule is not executed. |
How It Works
The following illustration depicts the Risk Service process:
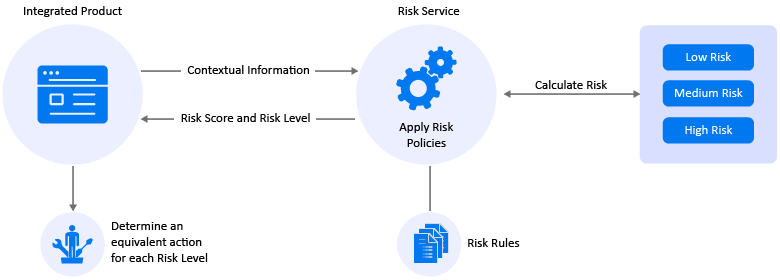
For information about Risk Rules, see Table 2-1, Risk Rules.
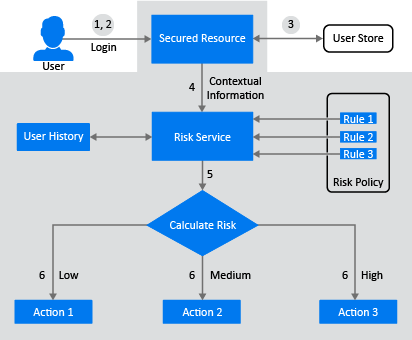
The following diagram illustrates the basic flow of authentication using Risk Service:
-
A user tries to log in to a web application.
-
The user specifies login credentials.
-
The integrated access management solution identifies the user.
-
The integrated access management solution provides the contextual data to Risk Service.
-
Risk Service calculates the risk level based on the defined set of rules and returns one of the following risk levels:
-
Low
-
Medium
-
High
-
-
The administrator configures appropriate action (authentication chains) based on the risk level.
Benefits of Risk Service
Risk Service enables you to accomplish the following goals:
-
Enhance the security of a web application or network by reducing and preventing fraudulent access.
-
Assess the risk level based on different parameters and users’ behavioral patterns (for example, browser type, time of login).
-
Improve user experience. Users need to provide additional details for authentication only whenthe associated risk prevails.