C.1 Access Control Using PUM UserGroup as IDM Entitlements
A PUM UserGroup (UG) defines a users' membership who get's privileged access on the servers. The PUM UserGroup object can be associated with a PUM Rule object to define a user’s privileged access to servers based on the UserGroup membership. In the PUM driver, UserGroup is defined as the Entitlement object. From the IDM RBPM(UserApp), the UserApp administrator can query the PUM Server via with driver and get the lists of UserGroups defined on the PUM system. On the UserApp, the administrator can create Roles/Resources and these can be associated with any of the queried UserGroup entitlements. These Roles and Resources can be associated with an IDM WorkFlow for the approval process. Any UserApp user can request for the created Roles/Resources and when they are granted, the PUM driver updates the UserGroup membership with the user's ID on the PUM server.
In addition, on the PUM server along with UserGroup object, other PUM objects such as HostGroup, AccessTime, Command can also be associated with the PUM Rule object to define more specific access to servers based on the requirement.
The user request and approval process flow are as depicted in the following diagrams:
Figure C-1 Access Provisioning to UNIX/Linux Servers (SSH) Using PUM and PUM Driver
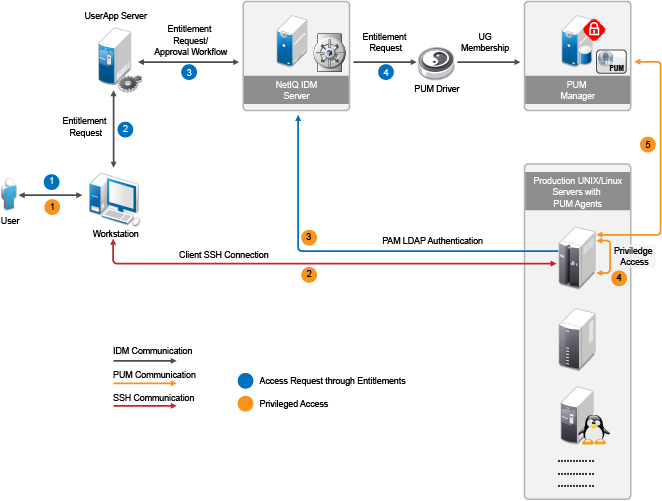
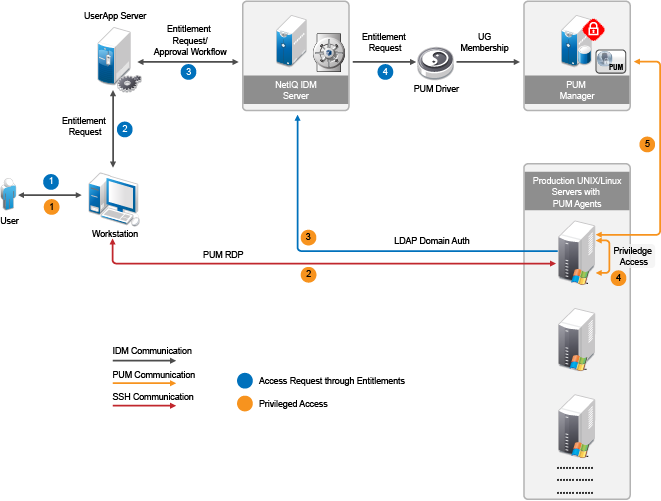
Figure C-2 Access Provisioning to Windows Servers (RDP) Using PUM and PUM Driver
Let us take a simple organization structure and see how to define PUM objects and provide access control to various servers used in the organization. let us assume that the organization has various departments, as shown in the following diagram:
Figure C-3 Organization Structure - Example
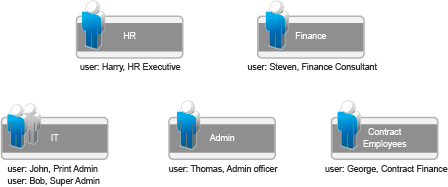
The details of the steps are as described in the following example.
C.1.1 Setting up PUM and IDM
To set up PUM and IDM:
-
Install IDM 4.0.2, iManager, and Designer. For more information, see the NetIQ Identity Manager 4.0.2 Documentation Web site.
-
Install PUM Framework Manager on a SLES machine.
For example: https://<pumManagerDNSorIP>
For more information, see the NetIQ Privileged User Manager 2.4 Documentation Web site.
-
Install PUM Agents on the UNIX/Linux and Windows servers to which privileged access are to be provided to the users. For more information, see the NetIQ Privileged User Manager 2.4 Documentation Web site.
-
Upload sample user objects using the sample-users.ldif file.
C.1.2 Creating the PUM Driver using Designer
To create the PUM driver using Designer, see Section 4.0, Creating a New Driver.
C.1.3 Configure PUM
Log in to PUM at https://<pumManagerDNSorIP> as admin and perform the following procedure:
-
Configure PUM to authenticate users from LDAP server (eDirectory):
-
Go to Home > Command Control > Privileged Accounts, click Add Account Domain, and provide values for the following fields, as specified:
-
Name: LDAP-Auth-Domain
-
Type: LDAP
-
Profile: NetIQ eDirectory
-
LDAP URL: <IP of the eDirectory server where IDM is running>
-
Base DN: ou=users,o=data
-
Account: admin
-
User DN: cn=admin,ou=sa,o=system
-
Password: <eDirectory admin password>
-
-
Go to Home > Framework User Manager > Users > Account Settings. In the Authentication Domain drop-down list, select LDAP-Auth-Domain. Click Finish.
-
-
A sample PUM Configuration to provide the access control to the servers in the various departments is provided in the samples folder. Import the sample PUM configuration file, npumExportSettings-Entitlements.xml, from the samples/ folder:
-
Open the npumExportSettings-Entitlements.xml file in a text editor and copy it to the clipboard.
-
Go to Home > Command Control > Import Settings and paste it in the Import text field. Click Finish.
-
After the import, you can find various PUM objects, such as Rule objects, UserGroup objects, and HostGroup objects, as shown in the following figure:

The following PUM objects are created:
-
HostGroup objects: These objects defines various groups of hosts based on the department. For example the HostGroup 'HR-Servers' would contain the servers belonging to the employees in the HR department and only they should be getting access to those servers.
-
UserGroup objects: These objects represents the groups to which user can get membership. For example, the UserGroup 'Admin Officer' would contain the members of the Administration department.
-
Commands objects: These objects defines the privileged commands that a user can get to run. For example, in the sample there is command called 'printerCommands' which has sample list of printer commands.
-
AccessTime objects: These objects define privileged access time duration. For example, in the sample there is an object 'AT-Contract' with allowed timings from 8am to 5pm on days except, Saturday and Sunday.
-
Rule objects: These are the objects where all of the above mentioned objects are used to define the access policies. For example, the object 'RL-Finance-Contractors' defines that any user having the membership to the UserGroup 'Contract Finance', the server that is being accessed is in the HostGroup 'Finance-Servers' and the time of access is as per the timings defined in the AccessTime 'AT-Contract', then provide the user with access to the privileged account, 'fin-contract-user' on the servers belonging to the Finance department.
-
-
NOTE:
-
For providing privileged access to Windows server, AccountDomain objects and the corresponding Credential objects should be created under the PrivilegedAccounts container in the Command Control. For more information, see
Adding an Account Domain
in the NetIQ Privileged User Manager 2.4 Administration Guide. -
User accounts must be created on the Production servers (see Figure C-1 and Figure C-2). The account name must be consistent with the user requesting for the Roles/Resources through RBPM/UserApp. Drivers for Linux and UNIX can be used to create local accounts on the UNIX/Linux servers.
To avoid creation of user accounts on every server, you can configure Windows servers with LDAP Domain authentication and UNIX/Linux servers with PAM-LDAP authentication.
C.1.4 Creating Roles/Resources in UserApp
-
Log in as uaadmin (UserApp admin) to the UserApp URL: http://<user_app_ip>:8180/IDMProv/.
-
Import the PUM Entitlements. PUM UserGroup objects are defined as the IDM Entitlements objects for the PUM driver.
Go to Roles and Resources > Configure Roles and Resources Settings > Entitlement Query Settings and click Refresh. This queries the UserGroup objects from the PUM server via the PUM driver.
-
Create role/resource objects in the Role/Resource Catalog and associate them with PUM UserGroup Entitlement. All the UserGroups that were queried from the PUM server are listed for entitlement selection, as shown in the following figure.

C.1.5 Getting Privileged Access
-
An UserApp user can now log in to the UserApp URL and request for the roles/resources. When the role/resource is approved, the PUM driver adds the respective user as the member of the corresponding UserGroup.
Now, the user can get the privileged access to the servers. For example, if user bob gets membership to 'Super Admin' UserGroup, then he has root access to the UNIX servers, lnx-finance-server-01.mycompany.com, solaris-it-webserver.mycompany.com, and hp-it-webserver.mycompany.com. For example:
# ssh bob@solaris-it-webserver.mycompany.com # id
This will return uid as bob.
# usrun su
this will return uid as root.
Also, as 'Super Admin', bob has Administrator access to the Windows servers which he can access from PUM RDP relay page by performing the following procedure:
-
Open the following URL in the Internet Explorer:
https://<pum_manager_ip>/rdprelay
Login as bob, with password is bob123, as specified in the sample ldif file.
-
After successful login, bob can view the servers to which he has access. Click any server to start a Remote Desktop session with Administrator privileges. As per the use case, bob will have access to the Windows servers - win2k8-hr-server-01.mycompany.com and win2k8-admin-server-01.mycompany.com.
-
-
Either Admin can revoke the role/resource assignment or the user can delete the assigned role/eesource. This triggers the Role/Resource Revoke process and the PUM driver triggers the removal of the user's UserGroup membership.