3.4 Creating Password Policies
Use the Password Policy Wizard in iManager to create new password policies.
See the online help for information about each step in the wizard, as well as the information in Section 3.0, Managing Passwords by Using Password Policies and in Section 4.0, Password Self-Service.
-
Make sure you have completed the steps in Section 3.3, Prerequisite Tasks for Using Password Policies.
These steps prepare you to use all the features of password policies.
-
In iManager, in the view, click > .
-
Click to create a new password policy.
-
Follow the steps in the wizard to create Advanced Password Rules, Universal Password Configuration Options, and Forgotten Password selections for the policy.
-
Assign the password policy to individuals, organizations, or your entire company, as necessary.
-
Review the settings for the new policy and click , then click to close the wizard.
3.4.1 Advanced Password Rules
Figure 3-1 shows the first section of the advanced password rules:
Figure 3-1 Advanced Password Rules
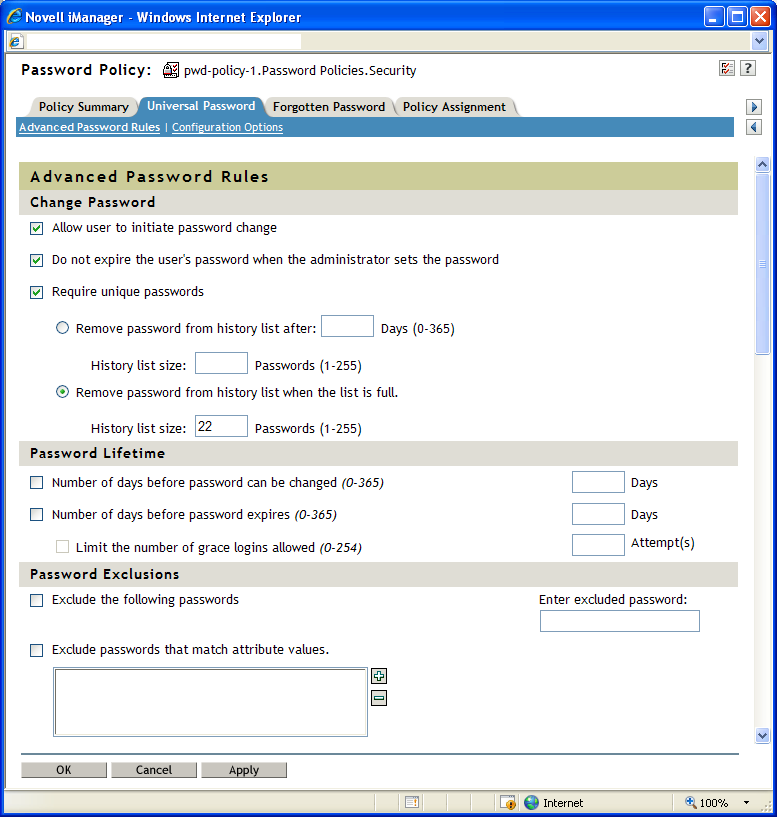
Password Syntax
You can specify one of three password syntax options to use for a password policy:
WARNING:iManager allows you to create a policy using the Microsoft Server 2008 Password Policy type, regardless of the version of NMAS installed on your server. However, you must have NMAS 3.3.4 or later installed to use this option. If you have a previous version of NMAS installed, the new password policy does not function properly. NMAS 3.3.4 is included with eDirectory 8.8 SP7.
-
This setting allows you to use the Microsoft* Complexity Policy requirements. Use this option if you must synchronize passwords between eDirectory and Microsoft Active Directory.
If you select this option for a policy, all users to which the policy is assigned must create passwords that meet the criteria of the Microsoft Complexity Policy as implemented in Universal Password. The criteria include:
-
Minimum password length is 6 characters.
-
Maximum password length is 128 characters.
-
The password must contain at least one character from three of the four types of character, uppercase, lowercase, numeric, and special:
-
Uppercase characters - all uppercase characters in the Basic Latin and the Latin-1 character sets.
-
Lowercase characters - all lowercase characters in the Basic Latin and the Latin-1 character sets.
-
Numeric characters - 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9.
-
Special characters - all other characters.
-
-
The values of the following user attributes can not be contained in the password: CN, Given Name, Surname, Full Name, and displayName.
-
-
This setting allows you to use the Microsoft* Windows Server 2008 password policy complexity requirements. Use this option if you must synchronize passwords between eDirectory and Microsoft Active Directory.
If you select this option for a policy, all users to which the policy is assigned must create passwords that meet the criteria of the Microsoft Windows Server 2008 Complexity Policy as implemented in Universal Password. If you select this option, several options on the Advanced Password Rules page are set to meet the criteria of the Complexity Policy. The criteria include:
-
Minimum password length is 6 characters, by default. You can configure the minimum password length in your environment using the option. For more information about configuring the minimum number of characters, see Password Length.
-
Maximum password length is 512 characters.
-
The password must contain at least one character from three of the five types of character, uppercase, lowercase, numeric, non-alphanumeric characters, and other characters:
-
Uppercase characters - all uppercase European-language characters, with diacritical marks, as well as Greek and Cyrillic characters.
-
Lowercase characters - all lowercase European-language characters, with diacritical marks, as well as Greek and Cyrillic characters.
-
Numeric characters - 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9.
-
Non-alphanumeric characters - any of the following special characters: ( ) ` ~ ! @ # $ % ^ & * - + = | \ { } [ ] : ; " ' < > , . ? / _.
-
Other characters - any Unicode character that is categorized as an alphabetic character but is not uppercase or lowercase. This includes Unicode characters from Asian languages.
-
-
The password cannot contain the full value of the CN user attribute for the eDirectory account. NMAS does not perform this check if the length of the attribute is less than three characters.
-
The password cannot contain any word from the list of excluded passwords. NMAS does not perform this check if the length of the excluded password is less than three characters. For more information about excluding passwords, see Password Exclusions.
-
The password cannot contain the full value or any part of the value of the Full Name attribute for the account, if the attribute contains at least three characters and is a single word. A part of the attribute value is defined as three or more consecutive characters delimited on both ends by the following characters: commas; periods; dashes; hyphens; underscores; spaces; pound signs; or tabs.
-
The maximum number of complexity policy violations allowed in a password is 2 by default. You can configure the number of complexity violations allowed using the option. For more information about configuring the maximum violations allowed, see Password Complexity Violations.
-
-
This allows you to use the Novell syntax for the password policy. This option is selected by default. Standard settings for policies using Novell syntax include:
-
Minimum password length is 4 characters, by default. You can configure the minimum password length in your environment using the option. For more information about configuring the minimum number of characters, see Password Length.
-
Maximum password length is 12 characters, by default. You can configure the maximum password length in your environment using the option. For more information about configuring the maximum number of characters, see Password Length.
-
Password Syntax Precedence
If you modify the attributes of a password policy using Directory Administration or LDAP, outside of the iManager Password Management plug-in interface, you may set up a conflict between one or more of the password policy types. For example, you could use LDAP to enable both the Microsoft complexity policy and Microsoft Windows 2008 Password Policy types for the same policy.
In the event of a conflict, eDirectory uses the following order of precedence:
-
Microsoft Windows 2008 Password Policy
-
Microsoft complexity policy
-
Novell syntax
For more information about modifying password policies outside of the Password Management interface, see Modifying Password Policies Outside of the Password Policies Interface.
Change Password
-
This allows the user to use the password self-service features. This option is selected by default. For information about password self-service, see Section 4.0, Password Self-Service.
-
This option requires the user to go and change his or her password. This feature allows you to override the default. The default behavior in eDirectory, when password expiration is set, is to expire the user’s password when the administrator sets the password.
-
When this option is selected, the user is prevented from changing the password to one that is already in the history list. If a user tries to change the password and reuse one that is in the history list, the password policy rejects the password and the user is prompted to specify a different one.
You can specify how unique passwords are enforced by using one of the following two values:
-
and a specified .
If you require unique passwords, you can specify how many days a previous password remains stored in the history list for comparison.
For example, if you specify a limit of 30 days, and the user's previous password was “mountains99,” that password remains in the history list for 30 days. During that time, if the user tries to change his or her password and reuse “mountains99,” the password policy rejects that password, and the user is prompted to specify a different one. After the 30-day period, the old password is no longer stored for comparison, and the password policy allows it to be reused.
If you require unique passwords, you can also indicate how many passwords are stored in the history list for comparison. For example, if you specify 3, then the user's previous three passwords are stored. If a user tries to change his or her password and reuse one that is in the history list before the number of days specified for removal from the history list, the password policy rejects the password, and the user is prompted to specify a different one.
NOTE:
-
If the option is selected, the option is also selected by default.
-
If is selected and you select but don’t specify a number of days, the password is on the history list for 8 times the value set in the field, in the Password Lifetime section. If neither field has a value, the password is on the history list for 365 days.
-
If you specify a password history list size and a number of days, and the number of passwords in the password history list size has been met, the user cannot change his or her password unless the password has expired. An administrator can change or set a user password even if the password list size has been met.
-
After one or more passwords expire in the password history list, the list is no longer full, and a user is again able to change his or her password. This limitation is included to prevent users from changing their passwords so many times that a password is no longer included in the password history list, and they can re-use it.
-
If a password history list size is not specified, the password history is never full.
-
When comparing a specified password against previous passwords in the password history, eDirectory differs from Active Directory. If the size of the password history list is “N,” Active Directory compares a specified password against “N” previous passwords. However, eDirectory compares a specified password against “N+1” previous passwords.
-
-
and the number of passwords reaches the specified (1-255).
If you require unique passwords, you can indicate how many passwords are stored in the history list for comparison. This option works on a first-in, first-out basis, where the oldest passwords are removed from the history list first. For example, when a user creates a new password that is not currently in the history list, the oldest password in the history list is removed if the history list is full.
NOTE:
-
If the option is selected, the option is also selected by default. With the Microsoft Server 2008 syntax enabled, the range is 0-24 passwords.
-
If this option is selected, you should also select both the and options, with at least the minimum number of days for each.
-
If you specify a password history list size of 0, NMAS only compares any new password created by a user against that user’s current password.
-
-
-
and a specified number of characters
When this option is selected, the user must specify a password that includes at least as many “new” characters, characters unused in previous passwords, as specified in the setting. This option is selected by default.
You can specify how unique the unused characters must be by using the following value:
-
and a specified number of characters
If you require a certain number of unused characters for any new password, you can specify how many previous passwords to consider when checking a password for previously-used characters.
For example, if you specify a minimum of three new characters and specify that five previous passwords should be considered for character exclusion, and a user creates the new password “mountains99,” that password must include at least three characters not in any of the previous five passwords. If the user’s password two changes previous was “maintains99,” only two characters different from the new password, the password policy rejects that password, and the user is prompted to specify a different one.
NOTE:
-
Both the and options are selected by default. However, the values of both options are set to 0 by default.
-
If the value of the option is set to 0, the option is disabled.
-
If the value of the option is set to 0, only the current password is considered when eDirectory checks for “new” characters.
-
Password Lifetime
-
This option restricts the user from changing their Universal Password before the specified time has elapsed. For example, if this value is set to 30, a user must keep the same password for 30 days before he or she can change it.
-
This option causes a user’s password to expire after a specified time has elapsed. For example, if this value is set to 90, a user's password expires 90 days after it has been set. If grace logins are not enabled, the user cannot log in after a password has expired, and administrator assistance is needed to reset the password. However, if you enable grace logins, the user can log in with the expired password the specified number of times. Also, if you do not select the option, unlimited grace logins are allowed.
NOTE:
-
If the option is selected, the and options are also selected by default. With the Microsoft Server 2008 syntax enabled, the range for both options is 0-999 days.
-
If an administrator changes a user's password, such as when creating a new user or in response to a help desk call, the password is automatically expired if you have enabled the setting to expire passwords in the password policy. For this particular feature, the number of days is not important, but this setting must be enabled. Selecting the option overrides this security enhancement.
-
When the password expires, this value indicates how many times a user is allowed to log in to eDirectory by using the expired password. If grace logins are not enabled, the user cannot log in after a password has expired, and he or she requires administrator assistance to reset the password. If the value is 1 or more, the user has a chance to log in additional times before being forced to change the password. However, if the user does not change the password before all the grace logins are used, he or she is locked out and is unable to log in to eDirectory. Also, if you have not selected the option, unlimited grace logins are allowed.
-
Password Exclusions
-
This allows you to manually specify the passwords you want to exclude. You can use this option to exclude specific words or single characters, not a pattern or an eDirectory attribute. You can also exclude passwords containing a specific special character, including a *, +, %, or space character. For example, if you add the character * to the list of excluded passwords, a user who tried to specify the password “Pa55w0rd*!” would receive an error saying that the specified password is invalid. This can be useful if you need to restrict users from specifying passwords containing special characters that cause issues with applications in your environment.
For NMAS 3.1.3 and later, the strings in the exclude list cannot be contained in the password, and the comparison is case-insensitive. For example, if “test” is in the exclude list, then the following cannot be passwords: Test, TEST, ltest, test1, and latest.
Keep in mind that password exclusions can be useful for a few words that you think would be security risks. Although an exclusion list feature is provided, it is not intended to be used for a long list of words, such as a dictionary. Long lists of excluded words can affect server performance. Instead of a long exclusion list to protect against “dictionary attacks” on passwords, we recommend that you use the Advanced Password Rules to require numbers to be included in the password.
-
This allows you to select User object attributes that you want to exclude from being used as passwords. For example, if you add the Given Name attribute to the list, and the Given Name attribute contained the value of Frank, then neither frank, frank1, nor 1frank could be used as the password.
Use the plus and minus buttons to add and delete attribute values from the list.
NOTE:If the option is selected, the option is also selected by default. With the Microsoft complexity policy syntax enabled, the list of attribute values to match is prepopulated with the following attributes: Common name; Display name; Full name; First name; and Last name.
Figure 3-2 Advanced Password Rules Continued
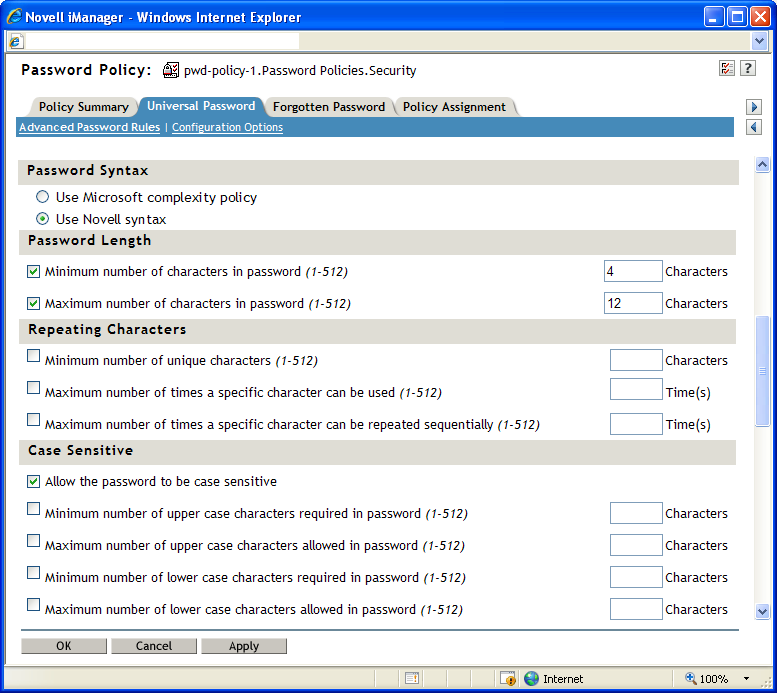
Password Length
-
-
NOTE:
-
The maximum length for any password created using NMAS is 512 characters.
-
If the option is selected, neither the nor option is available.
-
If the option is selected, only the option is available. The option is selected by default.
-
If the option is selected, both the and options are also selected by default.
-
Password Complexity Violations
-
This option allows you, as an administrator, to configure the number complexity policy violations you want to allow in passwords in your environment. By default, the Microsoft Server 2008 Password Policy requires that a password include at least one character from three of the five types of character, uppercase, lowercase, numeric, non-alphanumeric characters, and other characters. Therefore, the default number of violations allowed is 2. For more information on policy requirements for Microsoft Server 2008 Password Policy, see Password Syntax.
However, if you want to make your password policy more or less restrictive, you can modify the default number of violations allowed. For example, if you change the default setting to 1, all passwords must include at least one character from four of the five character types listed above. If the setting is 4, passwords must include a character from only one of the five character types.
NOTE:The option is only available if you select the option. The option is selected by default.
Repeating Characters
-
-
-
NOTE:If either the or options is selected, the , , and options are unavailable.
Case Sensitive
In eDirectory 8.7.1 and 8.7.3, you needed to use the Novell Client for case sensitivity to work. In eDirectory 8.8 or later, you can use the option to make your passwords case sensitive for all the clients that are upgraded to eDirectory 8.8. See the Novell eDirectory 8.8 SP7 Administration Guide for more information.
NOTE:
-
NMAS does not currently support case sensitive password checking when using Unicode characters.
-
The option is only available if you select the option. The option is selected by default.
The option is only available if you select the option. The option is selected by default.
With selected, you have four options:
When is not selected, the passwords are case insensitive, and you have two options:
IMPORTANT:Passwords are stored with case, and are synchronized between systems with case sensitivity, even though the option is not selected. The case of password characters is ignored if the option is not selected.
Figure 3-3 Advanced Password Rules Final
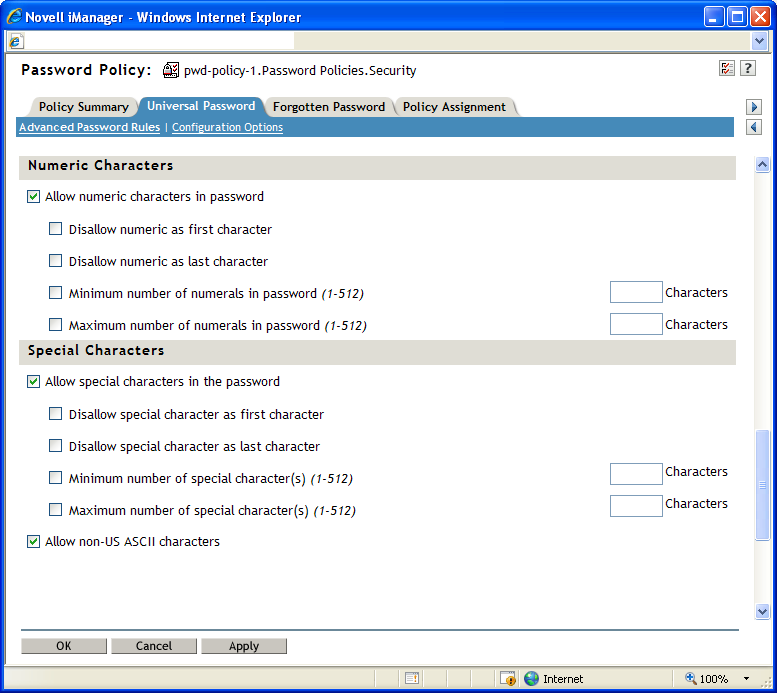
Numeric Characters
NOTE:The option is only available if you select the option. The option is selected by default.
Non-alphanumeric Characters
Non-alphanumeric characters are characters that are not numbers (0-9) or alphabetic characters. Alphabetic characters are defined as a-z, A-Z, and alphabetic characters in the Latin-1 code page 850.
-
-
-
This option allows a password to include characters outside of the Basic Latin character set, also known as extended characters.
NOTE:The option is only available if you select the option. The option is selected by default.
Non-alphabetic characters
Non-alphabetic characters are the characters that are not alphabetic characters. Alphabetic characters are defined as a-z, A-Z, and alphabetic characters in the Latin-1 code page 850.
NOTE:
-
The option is only available if you select the option.
-
If you use the option, ensure your policy does not unduly restrict possible passwords. For example, you can create a policy that requires multiple non-alphabetic characters or numerals but also limits the number of non-alphabetic characters allowed.
3.4.2 Modifying Password Policies Outside of the Password Policies Interface
In addition to creating, modifying, and assigning password policies using the iManager Password Management plug-in, you can modify policies outside of the Password Policies interface in one of the following ways:
-
Modify the policy object directly using the Directory Administration interface.
-
Modify the policy object directly using the ldapmodify command line tool.
However, it is not recommended that you manipulate password policies outside of the Password Policies interface, as this manipulation might cause issues in your environment if all attributes are not properly set. If you set multiple policy types for a single policy, for example, only the “highest” policy type in the order of precedence takes effect, and eDirectory ignores any policy rules for the “lower” policy types applied. For more information about password policy type precedence, see Password Syntax Precedence.
In addition, if you change the type of a password policy from the Microsoft Server 2008 Password Policy type to the Microsoft complexity policy type without using the Password Policies interface, iManager does not delete the existing Microsoft Server 2008 Password Policy attribute (nspmAD2K8Syntax) in the policy object. Instead, iManager sets the value of the attribute to False. In this situation, eDirectory ignores all policies and rules set for either policy type.
Another issue can occur when you use LDAP to modify specific rules for a policy. If you modify a policy so that two rules conflict, eDirectory applies a rule that is selected or is set to True in the policy instead of a conflicting rule that is not selected or is set to False.
For example, you can create a policy and then modify that policy to both not allow numeric characters and allow non-alphabetic characters. Because the value of the nspmNonAlphaCharactersAllowed attribute is set to True, all non-alphabetic characters are allowed, including numeric characters, even though the nspmNumericCharactersAllowed is set to False.
3.4.3 Random Password Generation
Instead of specifying a particular password, users can also request a randomly-generated password. Randomly-generated passwords automatically conform to the complexity requirements and other restrictions of the password policy assigned to the user.
Randomly-Generated Microsoft Server 2008 Passwords
Randomly-generated passwords for Microsoft Server 2008 Password Policy policies differ in the following ways from randomly-generated passwords using other password policy types:
-
If a user is assigned a password policy that uses the Microsoft Server 2008 Password Policy type and requests a randomly-generated password, NMAS generates the password based on the number of password complexity violations allowed for the policy.
-
If the number of password complexity violations allowed is set to the maximum value of 5, any randomly-generated password consists only of uppercase or lowercase alphabetic characters.
-
If the configured password complexity requirements are extremely strict, even randomly-generated passwords may not be valid for the password policy.
-
The maximum length of any randomly-generated Microsoft Server 2008 Password Policy password is 16 characters, unless the minimum length configured in the policy is more then 16 characters. If the minimum length is more than 16, the length of the generated password is the minimum length set in the policy. For example, if the minimum length of a password is set to 20 characters using a Microsoft Server 2008 policy, the randomly-generated password is always 20 characters long.
3.4.4 Universal Password Configuration Options
The following figure shows an example of the Universal Password configuration options:
Figure 3-4 Configuration Options
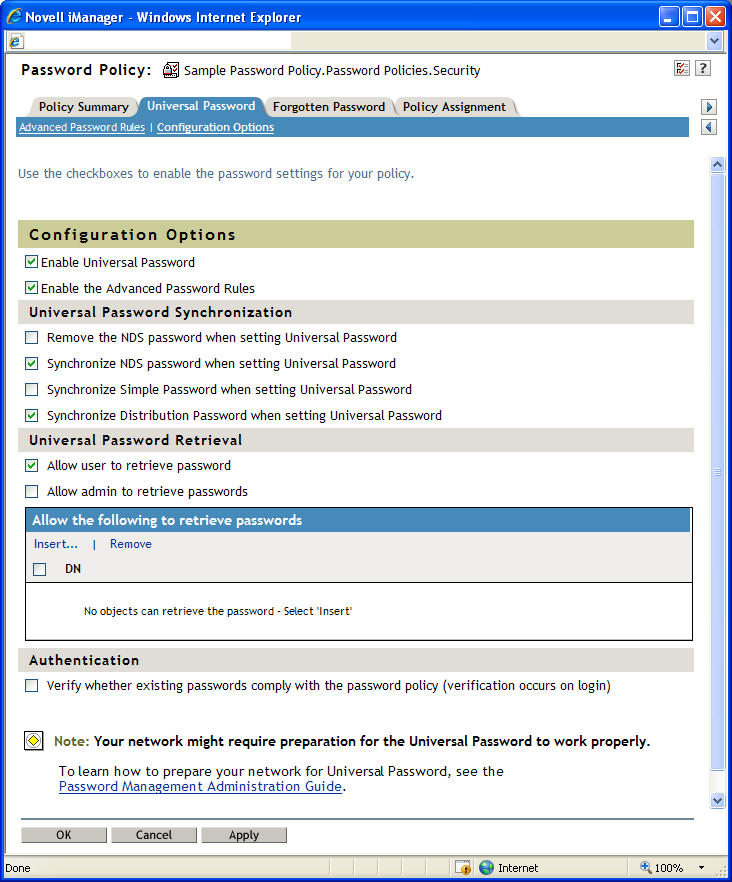
-
Enables Universal Password for this policy. You must enable Universal Password if you want to use the other password policy features.
-
Enables the Advanced Password Rules found on the Advanced Password Rules page for this policy. These advanced password rules help secure your environment by giving you control over password lifetime and what the password can contain.
-
-
If this option is selected, the NDS password is disabled when the Universal Password is set. Also, when the NDS password is set, the NDS password hash is set to a random value that is not known except to eDirectory. There might or might not be a password that could be hashed to the random value.
-
If this option is selected, and the Universal Password is set, the NDS password is set at the same time and with the same password.
-
Provided solely for backward compatibility with NetWare 6.0 servers that contain AFP/CIFS users. If you have NetWare 6.0 servers in the tree that contain AFP/CIFS users, you should select this option.
NOTE:The setting of this option does not affect your ability to import user passwords by using ICE.
If this option is selected, and the Universal Password is set, the Simple Password is set at the same time and uses the same password.
-
Determines whether the Identity Manager Metadirectory engine can retrieve or set a user’s Universal Password in eDirectory.
If this option is selected, and the Universal Password is set, the Distribution Password is set at the same time and uses the same password.
The Distribution Password can be used with Identity Manager to perform password synchronization to connected systems. This option also allows the Metadirectory engine to retrieve a user’s Universal Password in eDirectory.
-
-
-
Determines whether the Forgotten Password Self-Service feature can retrieve a password on behalf of a user, so that the password can be e-mailed to the user. If this option is not selected, the corresponding feature is dimmed on the Forgotten Password page in the Password Policy.
This option allows users to retrieve their own passwords by using NMAS LDAP extensions.
-
Lets you retrieve users' passwords by using a third-party product or service that uses this functionality.
This option is not recommended with NMAS 3.2 and later. Instead, you should use the option to assign password read rights to specific objects, such as the SAMBA or freeRADIUS service objects, that need this ability to perform their functions.
If is selected, then users that have write privileges on the target object’s ACL attribute can retrieve the target object’s password.
-
Lets you insert an object that has the ability to retrieve passwords.
-
-
-
If this option is selected, and users log in through iManager or the iManager self-service console, their existing passwords are checked to make sure they comply with the Advanced Password Rules in the users’ password policy. If an existing password does not comply, users are required to change it.
-