2.8 Implementing Token-Based Logins
Systems that use tokens (also called smart cards) as login credentials require a modified configuration. In these systems, a token is passed from server to client, and the client uses the token to log in to the server.
Figure 2-1 shows the components and communications involved in issuing requests and validations for tokens.
Figure 2-1 Process for Implementing Token-Based Logins
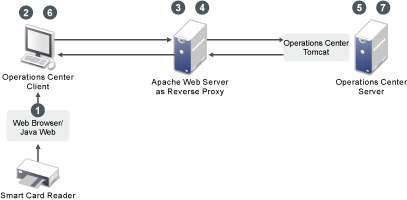
The following is the process for implementing taken-based logins. Refer to numbered steps in the diagram and see the description of each step:
-
The Web browser and Java Web Start are configured to acquire certificates from the smart card reader. Web Start applications are configured to use these certificates.
-
The Operations Center client is launched by Java Web Start and uses the Java Web Start certificates. The Operations Center client makes an HTTP Request to the Operations Center Server (through the Apache Web Server as Reverse Proxy).
-
The Apache Web Server has a security plug‑in that authenticates a user based on the incoming SSL certificate.
-
For an authenticated user, the security plug‑in adds HTTP headers (i.e. “remote-user”) to the HTTP request that is sent to the Operations Center Server.
-
An HTTP request comes in to the Operations Center Server. If it is configured for auto-login through the formula.properties and the required HTTP header is present, then the Operations Center Server creates a temporary token. This token can be redeemed by the Operations Center client to automatically log in the user specified in the required HTTP header. Headers for the user name and the token value are added to the HTTP Response, which is sent to the Operations Center client.
-
If the Operations Center client has been configured for auto-login, then the HTTP response is examined for HTTP headers specifying the user name and a token value. If found, the Operations Center client requests a Operations Center Server login using the user name and token provided.
-
The Operations Center Server verifies the token, and if it is valid, auto-logins the user.
To implement token-based logins:
-
Configure the following properties in the /OperationsCenter_install_path/config/Formula.custom.properties file:
# Server.allow.auth.principal # # Allow token based logins if true. Server.allow.auth.principal=true # Server.header.auth.principal # # Header used for the token login principal. Server.header.auth.principal=HTTP Header Name # Server.header.auth.token # # Header used for the token login token. Server.header.auth.token=auth-token
For Server.header.auth.principal, replace HTTP Header Name with the actual HTTP header, such as “remote-user” that is added by the security plug‑in to the HTTP request sent to the Operations Center server.
For more information about using the Formula.custom.properties file to customize configuration options, see Making Custom Changes in the Operations Center 5.6 Server Configuration Guide.
-
Configure the following properties in the applet-param.xml file:
<param name="Connection.allow.auth.principal" value="true" /> <param name="Connection.header.auth.principal" value="auth-principal" /> <param name="Connection.header.auth.token" value="auth-token" />
The Connection.header.auth.principal and Connection.header.auth.token values must be the same as those in the formula.properties file.