4.11 Feature-Specific Access Control
It is possible to control access to some features of the Operations Server console:
4.11.1 Root Cause
The Show Root Cause feature provides a quick way to identify elements that caused a change in the condition of a higher-level element. Right-click an element in the Explorer pane and select Show Root Cause. The Root Cause dialog box displays Root Causes and Details sections:
Figure 4-10 Root Cause Dialog Box
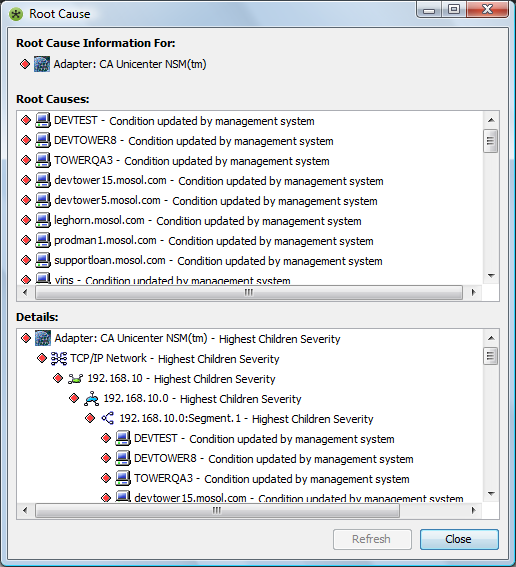
The Details section identifies the hierarchy of the elements involved.
Users who do not have View permissions to an element that is the root cause cannot view the root cause hierarchy that is normally displayed in the Details pane. Therefore, users with restricted access to the element hierarchy might not see all the elements contributing to a higher-level element’s condition.
For more information on the Root Cause feature, see Viewing Root Cause and Impacted Elements in the Operations Center 5.6 User Guide.
4.11.2 Show Impacted
The Show Impacted feature identifies higher-level objects that are affected by the condition of a selected element. To view higher-level objects impacted by a specific element, right-click an element in the Explorer pane and select Show Impacted. The Impacted dialog box displays only the elements for which the user has View access rights. Figure 4-11 shows the parent elements that are identified by the Billing element’s condition:
Figure 4-11 Impacted Dialog Box
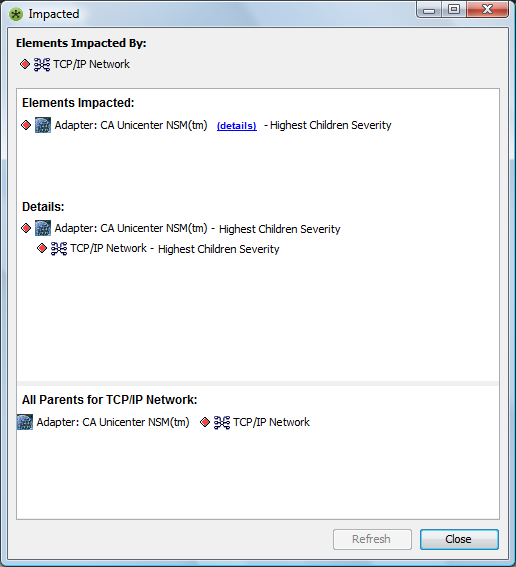
If the impacted objects are not accessible based on security settings, or if the parent object is Enterprise, both the Details and Elements Impacted sections of the dialog box display None.
In some situations, you might want to exclude some Services elements from impact reporting. Excluded element branches do not display in the Impacted dialog box or in related reports, regardless of a user’s access rights. For more information on the Show Impacted feature and disabling element branches from impact reporting, see Viewing Root Cause and Impacted Elements in the Operations Center 5.6 User Guide.
To exclude an element branch from impact reporting:
-
Right-click an element in the Services hierarchy and select Properties.
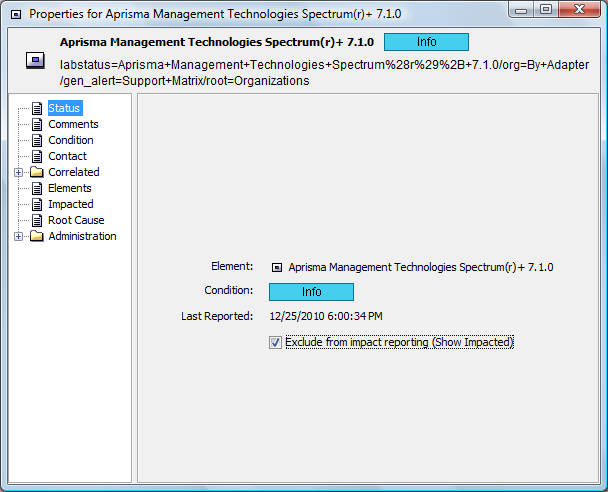
-
In the Status property page, select Exclude from impact reporting.
-
Close the property page.
-
Click Yes when you are asked to save changes.
4.11.3 Suppress and Acknowledge Commands
The Suppress and Acknowledge commands can be enabled for elements and alarms. Administrators can use these features to troubleshoot issues related to an alarm or identify how a new event affects the state of an element.
The Acknowledge command is available only for elements and alarms originating from BMC*, Tivoli*, PATROL, and NetView* adaptors.
Suppressing an element places the element in an Unmanaged condition, which displays the element, but does not provide a condition status. A suppressed element’s condition changes are ignored when calculating the roll‑up state of parent elements. Suppression can be configured for a specific time interval, with an optional timeout. Suppression can be reset by a manual action or can expire. Acknowledgment is available only for elements with a non‑OK condition.
Configuring these commands is explained in Configuring Suppression and Acknowledgement in the Operations Center 5.6 Server Configuration Guide. After suppression and acknowledgement are configured for one adapter, they become available system-wide for all adapters.
One access control feature worth noting is that, by default, users must have the Manage permission on the elements for which the Suppress or Acknowledge operations are configured in order to see and use these right-click options. It is possible to change the permission level required for using the Suppress command; see Configuring Suppression and Acknowledgement in the Operations Center 5.6 Server Configuration Guide.
4.11.4 Automation Events
Automation events can trigger an alert when a network event occurs that might require intervention. Automation alerts can include audio signals, notifications sent using e‑mail, or entering information in a database about an event. Scripting capabilities are available to define more complex actions, such as tracking actions performed on alarms.
The Automation features are described inDefining and Managing Automation Events in the Operations Center 5.6 Server Configuration Guide.
The access control features relevant to automation tasks are:
-
The user who creates an automation event is the event owner. Only the owner should configure different automation actions for the same conditions.
-
Automation events can be defined for a user, group, or the Automation server. Automation events run on a selected element only for the users and groups for which they are set up.