4.2 Configuring Data Collection for Syslog Event Sources
Events can be collected from various data sources by using the Syslog Connector. Sentinel Log Manager is preconfigured to accept syslog data from syslog event sources that send data over TCP (port 1468), UDP (port 1514), or SSL (port 1443).You can also configure Sentinel Log Manager to listen on additional ports.
To get started with syslog data collection, configure your syslog event sources to send their data to one of these ports. When Sentinel Log Manager receives data from configured event sources, it automatically chooses the most suitable Collector to parse the data, parses the data into events, and stores the event and raw data in the configured networked storage location.
The following sections describe how you can configure the event sources to send data to the Sentinel Log Manager and how you can configure new syslog ports to receive data:
4.2.1 Parsing Logic for Syslog Messages
Sentinel Log Manager can receive, store, and search against events from any syslog source. If the data source is recognized, Sentinel Log Manager automatically chooses the most suitable Collector to parse the data, parses the data into events, and stores the event and raw data in the configured networked storage location.
You can filter the collected data to drop any unwanted events. Messages from recognized data sources are parsed into fields such as target IP address and source username. Messages from unrecognized data sources are placed in a single field for storage, searching, and reporting.
The Generic Event Collector collects and processes data from unrecognized event sources that have suitable connectors.If the data was generated by a supported event source, the Generic Event Collector analyses the received data and attempts to parse the information. If the Generic Event Collector does not understand the message, it does minimal parsing and places the bulk of the text in the (Msg) field.
4.2.2 Configuring Syslog Servers
When you point your syslog event sources (an application or a system that logs the event) to Sentinel Log Manager, it automatically creates an event source entry to track data received from the event source. It also allows you to manage how the data is processed. An entry is created for each unique IP address or hostname that appears in the header portion of the syslog messages. This entry enables you to identify the machines generating the syslog messages, regardless of whether they are being aggregated by a syslog relay or not.
The Sentinel Log Manager Web interface allows you to configure ports to listen on to receive syslog data.
To add or remove syslog servers, use the Event Source Management interface. For more information, see Configuring Data Collection for Other Event Sources.
-
Log in to Sentinel Log Manager as an administrator.
-
Click the link in the upper left corner of the page.
-
Select the s tab.
-
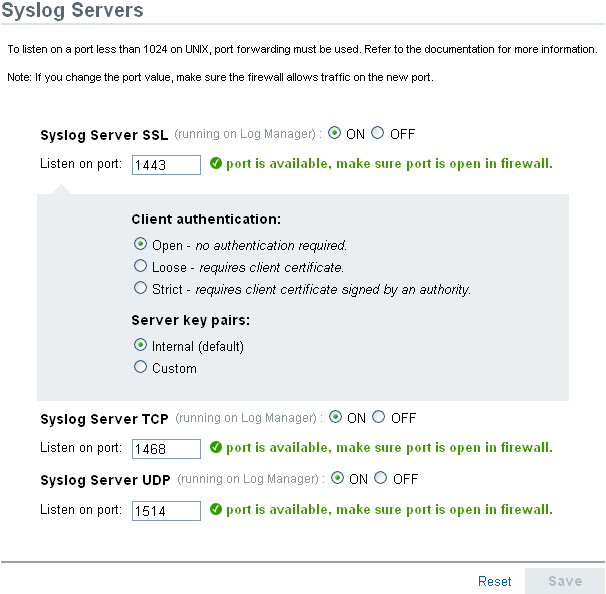
In the section, specify the TCP, UDP, and SSL port numbers for the syslog servers.
The default ports for TCP, UDP, and SSL are 1468, 1514, and 1443.
-
To start or stop the data collection for each of the syslog servers, select the on or off options next to them.
-
To change the port values, specify a valid port value.
The following table shows the status messages you see after entering the valid or non-valid port values.
Status Icon
Message
Green Check Mark Icon
If the specified port is valid and is not in use, a port is valid and open message is displayed.
Red Cross Icon
If the specified port is not valid (non-numeric or not between 1 to 65535), a port is not valid message is displayed.
Red Cross Icon
If the specified port is valid but it is already in use, or if the syslog server does not have permission to use it, a port is valid but not open message is displayed.
-
Set the appropriate client authentication and server key pairs settings for the SSL syslog server.
For more information on setting the client authentication, see Configuring Client Authentication for the SSL Syslog Server.
The SSL Syslog server is automatically restarted if any changes are made here.
-
(Optional) Click to change the specified settings to previous settings.
-
Click to save the new settings.
The button is disabled until a valid port is specified for all of the servers.
4.2.3 Setting the Syslog Server Options
You can configure the type of client and server authentication for syslog serves that uses SSL.
Configuring Client Authentication for the SSL Syslog Server
The client authentication settings determine how strictly the SSL syslog server verifies the identity of syslog event sources that are attempting to send their data.You should use a strict client authentication policy that is applicable in your environment to prevent rogue syslog event sources from sending undesired data into Sentinel Log Manager.
Open: No authentication is required. Sentinel Log Manager does not request, require, or validate a certificate from the event source.
Loose: A valid X.509 certificate is required from the event source, but the certificate is not validated. It does not need to be signed by a certificate authority.
Strict: A valid X.509 certificate is required from the event source, and it must be signed by a trusted certificate authority. If the event source does not present a valid certificate, Sentinel Log Manager does not accept its event data.
Creating a Trust Store
For strict authentication, you must have a trust store that contains the public certificate of the certificate authority (CA) that signed the event source certificate. After you have a DER or PEM certificate, you can create the trust store by using the TruststoreCreator utility that comes with Log Manager.
-
Log in to the Sentinel Log Manager server as novell.
-
Go to /var/opt/novell/sentinel_log_mgr/data/updates/done.
-
Use the following command to extract the syslog_connector.zip file:
unzip syslog_connector.zip
-
Copy the TruststoreCreator.sh or TruststoreCreator.bat file to the machine that has the certificates.
or
Copy the certificates to the machine with the TruststoreCreator utility.
-
Run the TruststoreCreator.sh utility as follows:
TruststoreCreator.sh -keystore /tmp/my.keystore -password password1 -certs /tmp/cert1.pem,/tmp/cert2.pem
In this example, the TruststoreCreator utility creates a keystore file called my.keystore that contains two certificates (cert1.pem and cert2.pem). It is protected by the password password1. The keystore file must be imported into the trust store.
Importing a Certificate into the Trust Store
For strict authentication, the administrator can import a certificate by using the button. This helps ensure that only authorized event sources are sending data to Log Manager. The trust store must include public certificate of the certificate authority (CA) that signed the event source certificate.
The following procedure must be run on the machine that has the trust store on it. You can open a Web browser on the machine with the trust store or move the trust store to any machine with a Web browser.
NOTE:If the CA is signed by another CA, then you must import the chain of CA certificates until the root CA.
To import a trust store:
-
Log in to Sentinel Log Manager as an administrator.
-
Click the link at the upper left corner of the page.
-
Click the tab.
-
In the Syslog Server section, select the option under .
-
Click and browse to the trust store file (for example, my.keystore)
-
Specify the password for the truststore file.
-
Click .
-
(Optional) Click to see more information about the trust store.
-
(Optional) Click to change to previous settings before saving
-
Click .
After the trust store is successfully imported, you can click to see the certificates included in the trust store.
Server Key Pair
Sentinel Log Manager is installed with a built-in certificate, which is used to authenticate the Sentinel Log Manager server to the event sources. This certificate can be overridden with a certificate signed by a public certificate authority (CA).
To replace the built-in certificate:
-
Log in to Sentinel Log Manager as an administrator.
-
Click the link at the upper left corner of the page.
-
Select the tab.
-
In the Syslog Server section, under, select .
-
Click and browse to the trust store file.
-
Specify the password for the truststore file.
-
Click .
-
(Optional) If there is more than one public-private key pair associated with the file, select the desired key pair, and click .
-
Click to see more information about the server key pair.
-
Click to change the specified settings to previous setting before saving it
-
Click .
Listening on Ports Below 1024
NOTE:The instructions in this section assume that your firewall is enabled and is compatible with the iptables command. If this is not the case, there are probably options in your firewall configuration interface to allow you to configure the same port forwarding as described here.
Because Sentinel Log Manager runs as the novell user, it cannot directly listen on ports that are lower than 1024. To listen on a port that is lower than 1024, use port forwarding to forward data to a port that Sentinel Log Manager can directly listen on. Use the /opt/novell/sentinel_log_mgr/bin/config_firewall.sh script to setup port forwarding.
You must run the following port forwarding command as root:
iptables -t nat -A PREROUTING -p <protocol> --destination-port <incoming port> -j REDIRECT --to-ports
The following command is an example of how to forward events from the default syslog server port 514 to the Novell Sentinel Log Manager port 1514 for syslog UDP traffic:
iptables -t nat -A PREROUTING -p udp --destination-port 514 -j REDIRECT --to-ports 1514