4.3 Configuring Data Collection for the Novell Audit Server
Sentinel Log Manager has enhanced support for Novell Audit servers. Data collection for Novell Audit server can be configured by using a simplified Web interface. Many Novell products send data to Sentinel Log Manager by using a Platform Agent. The data is received by an event source server called the Audit Server, which is packaged with Sentinel Log Manager. The audit server is similar in many ways to a syslog server. For more information on configuring logging for Novell products, see the Novell Audit 2.0.2 documentation, which packages the platform agent.
The following sections describe the procedure to configure the audit server port to receive data and also to set the audit server options:
4.3.1 Specifying the Audit Server Settings
To specify the data collection settings for the Audit server:
-
Log in to Sentinel Log Manager as an administrator.
-
Click the link in the upper left corner of the page.
-
Select the tab.
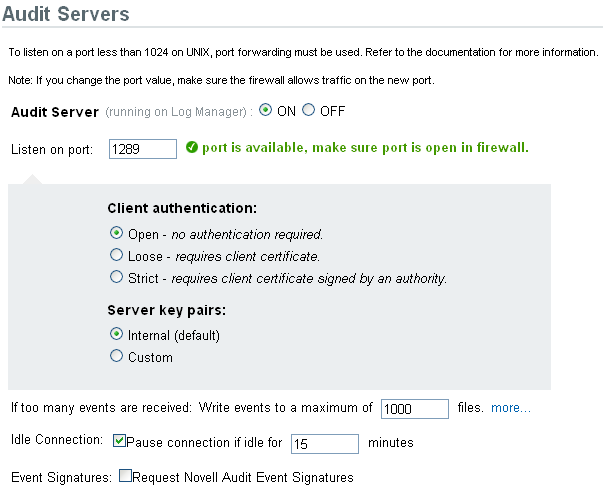
-
In the section, select the and options to start or stop the data collection for the audit server.
-
In the Audit Server section, specify the port on which the Sentinel Log Manager server listens to messages from the event sources.
For more information about setting the port, see Port Configuration and Port Forwarding for the Audit Server.
-
Set the appropriate client authentication and server key pairs settings.
For more information about client authentication, see Client Authentication for the Audit Server.
The Audit server and all related Audit Connectors are automatically restarted if any changes are made here.
-
Select the Sentinel Log Manager server behavior when the number of events received exceeds the buffer capacity.
WARNING:If you select , there is no supported method for recovering dropped messages,
-
Select to disconnect event sources that have not sent data for a certain period of time.
The event source connections are automatically re-created when they start sending data again.
-
Specify the number of minutes before an idle connection is disconnected.
-
(Optional) Select to receive a signature with the event.
To receive a signature, the Platform Agent on the event source must be configured properly.
-
(Optional) Click to change the specified settings back to the previous settings before saving
-
Click to save the new settings.
The button is disabled until a valid port is specified for the server.
These settings might affect data collection for several servers (for example, multiple eDirectory instances). However, they do not start or stop services on the event source machines.
Changes on this page take effect immediately.
To view the health of the Audit server and its event sources, see Section 4.5, Managing Event Sources.
4.3.2 Setting the Audit Server Options
Administrators can change the settings for how Sentinel Log Manager listens for data from the event source applications, set the port on which Sentinel Log Manager listens, and select the type of authentication between the event source and Sentinel Log Manager.
Port Configuration and Port Forwarding for the Audit Server
By default, Sentinel Log Manager listens on port 1289 for messages from the server. When the port is changed, the system checks whether the specified port is valid and open.
Binding to ports lower than 1024 requires root privileges, so you should use a port higher than 1024. You can change the source devices to send data to a higher port or use port forwarding on the Sentinel Log Manager server.
To change the Platform Agent to send data to a different port:
-
Log in to the event source machine.
-
Open the logevent file for editing. The file location depends on the operating system:
-
Linux: /etc/logevent.conf
-
Windows: C:\WINDOWS\logevent.cfg
-
NetWare: SYS:\etc\logevent.cfg
-
Solaris: /etc/logevent.conf
-
-
Set the LogEnginePort parameter to the desired port.
-
Save the file.
-
Restart the Platform Agent.
The method varies by operating system and application. Reboot the machine or refer to the application-specific documentation on the Novell Documentation Web Site for more instructions.
To configure port forwarding on the Sentinel Log Manager server:
-
Log in to the Sentinel Log Manager server operating system as root (or su to root).
-
Open the /etc/init.d/boot.local file for editing.
-
Add the following command at the end of the bootup process:
iptables -A PREROUTING -t nat -p protocol --dport incoming port -j DNAT --to-destination IP:rerouted port
Replace protocol with tcp or udp, incoming port is the port with the messages are arriving, and IP:rerouted port with the IP address of the local machine and an available port above 1024.
-
Save the changes.
-
Reboot. If you cannot reboot immediately, run the iptables command in Step 3 from a command line.
Client Authentication for the Audit Server
The event sources send their data over an SSL connection, and the Client authentication setting for the Sentinel Log Manager server determines what kind of authentication is performed for the certificates from the audit server on the event sources.
Open: No authentication is required. Log Manager does not request, require, or validate a certificate from the event source.
Loose: A valid X.509 certificate is required from the event source, but the certificate is not validated. It does not need to be signed by a certificate authority.
Strict: A valid X.509 certificate is required from the event source, and it must be signed by a trusted certificate authority. If the event source does not present a valid certificate, Log Manager does not accept its event data.
Creating a Trust store
For strict authentication, you must have a trust store that contains the public certificate of the certificate authority (CA) that signed the event source certificate. After you have a DER or PEM certificate, you can create the trust store by using the CreateTrust store utility that comes with Log Manager.
-
Log in to Sentinel Log Manager server as novell.
-
Go to /var/opt/novell/sentinel_log_mgr/data/updates/done.
-
Unzip the audit_connector.zip file:
unzip audit_connector.zip
-
Copy TruststoreCreator.sh or TruststoreCreator.bat to the machine with the certificates
or
Copy the certificates to the machine with the TruststoreCreator utility
-
Run the TruststoreCreator.sh utility:
TruststoreCreator.sh -keystore /tmp/my.keystore -password password1 -certs /tmp/cert1.pem,/tmp/cert2.pem
In this example, the TruststoreCreator utility creates a keystore file called my.keystore that contains two certificates (cert1.pem and cert2.pem). It is protected by the password password1.
Importing a Certificate into the Trust Store
For strict authentication, the administrator can import a certificate. This helps ensure that only authorized event sources are sending data to Log Manager. The trust store must include public certificate of the certificate authority (CA) that signed the event source certificate.
The following procedure must be run on the machine that has the trust store on it. You can open a Web browser on the machine with the trust store or move the trust store to any machine with a Web browser.
NOTE:If the CA is signed by another CA, then you must import the chain of CA certificates until the root CA.
-
Log in to Sentinel Log Manager as an administrator.
-
Click the link in the upper left corner of the page.
-
Select the tab.
-
In the Audit Server section, select the option under .
-
Click and browse to the trust store file (for example, my.keystore)
-
Specify the password for the trust store file.
-
Click .
-
(Optional) Click to see more information about the trust store.
-
(Optional) Click to change the specified settings back to the previous setting before saving.
-
Click .
After the trust store is imported successfully, you can click to see the certificates included in the trust store.
Server Key Pair
Log Manager is installed with a built-in certificate, which is used to authenticate the Sentinel Log Manager server to the event sources. This certificate can be overridden with a certificate signed by a public certificate authority (CA).
To replace the built-in certificate:
-
Log in to Sentinel Log Manager as an administrator.
-
Click the link in the upper left corner of the page.
-
Select the tab.
-
In the Audit Server section, under, select .
-
Click and browse to the trust store file.
-
Specify the password for the trust store file.
-
Click .
-
(Optional) If there is more than one public-private key pair in the file, select the desired key pair and click .
-
(Optional) Click to see more information about the server key pair.
-
(Optional) Click to change the specified settings back to the previous setting before saving.
-
Click .