5.1 Running an Event Search
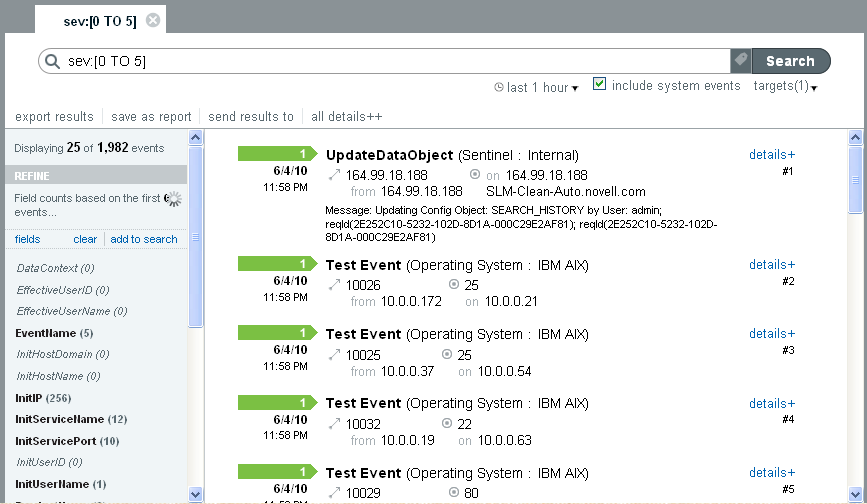
Users can run simple or advanced searches.Basic event information includes event name, source, time, severity, information about the initiator (represented by an arrow icon), and information about the target (represented by a bull’s-eye icon)
5.1.1 Running a Basic Search
A basic search runs against all the event fields listed in Table E-1.
NOTE:If time is not synchronized across your server, client, and event sources, you might get unexpected results from your search. This is especially a problem if searches are performed on time durations such as Custom,, and where display results are based on the time zone of the machine on which the search is performed.
To run a basic text search:
-
Log in to Sentinel Log Manager.
-
Click .
-
Type the Search criteria in the field and click the button on the upper right corner of the page.
Sentinel Log Manager is configured to run a default search for non-system events with severity 0 to 5 when a user clicks the button for the first time. Otherwise, it reuses the last search term the user entered.
For more information on the case-sensitive fields and tokenized (not case-sensitive) fields, see Section E.0, Event Fields.
-
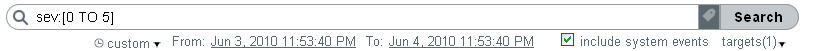
Select a time period for the search.
Most of the time settings are self-explanatory. The default is .
-
allows you to select a start date and time and an end date and time for the query. The start date should be earlier than the end date, and the time is based on the machine’s local time.
-
searches all available data, without any time constraints.
-
-
(Optional) To retrieve all log events from all sources, select , If the option is selected, all events generated by Sentinel Log Manager system operations are included. These events are tagged with the SentinelLogManager tag.
If the logged in user is not granted permission to view system events, the user does not see the option.
-
Click .
All fields in the index are searched for the specified text. A spinning icon
 indicates that the search process is being performed.
indicates that the search process is being performed.
The search results are displayed.
5.1.2 Running an Advanced Search
an advanced search can narrow the search for a value to a specific event field. The advanced search criteria are based on the short names for each event field and the search logic for the index. For more information on the field names, their descriptions, the short names that are used in advanced searches, and for information on the fields are visible in the basic and detailed event views, see Table E-1, Event Fields. For more information on the search procedure, see Section 5.1.1, Running a Basic Search.
NOTE:For more information on the tag names, click the link.
To search for a value in a specific field, use the short name of the field, a colon, and the value. For example, to search for an authentication attempt to Sentinel Log Manager by user2, use the following text in the search field:
evt:<eventmane> AND sun:user2
Other advanced searches could include the product name, severity, source IP, and the event type. For example:
-
pn:NMAS AND sev:5 (This search is for events with the product name NMAS and severity five.)
-
sip:123.45.67.89 AND evt:“Set Password” (This search is for the initiator IP of 123.45.67.89 and an event of 'Set Password'.)
Multiple advanced search criteria can be combined by using the following operators:
-
AND (must be capitalized)
-
OR (must be capitalized)
-
NOT (must be capitalized and cannot be used as the only search criterion)
-
+
-
-
The following special characters must be escaped by using a \ symbol:
+ - && || ! ( ) { } [ ] ^ " ~ * ? : \
The advanced search criteria syntax is modeled on the search criteria for the Apache Lucene open source package. For more information on the search criteria, see Lucene Query Parser Syntax.
To run an advanced search:
-
Log in to Sentinel Log Manager.
-
Click .
A new tab is displayed.
-
To search based on tags, you can do one of the following:
-
Click the tags widget
 , and select the tags from the pop-up, based on which you want to search the events.
, and select the tags from the pop-up, based on which you want to search the events.
-
Specify the following query:
@<tagname>
For example, @SentinelLogManager lists all the system events.
-
-
If distributed search is configured, click to select the server in a distributed environment, from which to search for events. For more information on Distributed Search, see Section 7.0, Searching and Reporting Events in a Distributed Environment.
5.1.3 Search Expression History
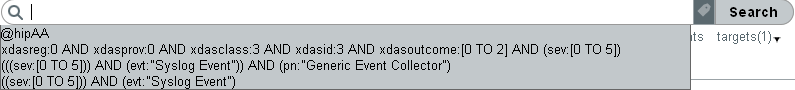
Sentinel Log Manager allows you to select a search expression from the search history list. The search history displays a maximum of 15 search expressions.When you enter a value in you can select one of the recently used searches and run it with the selected time parameters
Figure 5-1 Search Expression History Llist
-
When you enter a text value in , the closely matched search expressions appear in the recently used search expression list.
-
When the text is not entered in , the search history displays all the recently used search expressions. The most recent search expression appears at the top of the list.
-
For each user, a maximum of 250 search expressions is stored. If the number of search expressions exceeds 250, the oldest expressions are deleted from the list.