12.2 Defining User Identification for SAML 1.1
12.2.1 Selecting a User Identification Method for SAML 1.1
Two methods exist for identifying users from an identity provider when using the SAML 1.1 protocol. You can specify that no account matching needs to occur, or you can configure a match method. You configure a match method when you want to use attributes from the identity provider to uniquely identify a user on the service provider.
-
In the Administration Console, click > > > > > .
-
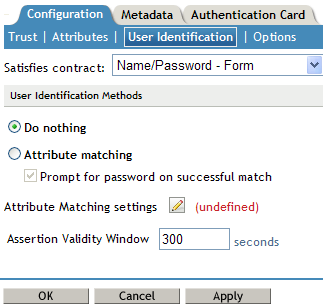
In the option, specify the contract that can be used to satisfy the assertion received from the identity provider. Because SAML 1.1 does not use contracts and because the Identity Server is contract-based, this setting permits an association to be made between a contract and a SAML 1.1 assertion.
Use caution when assigning the contract to associate with the assertion, because it is possible to imply that authentication has occurred, when it has not. For example, if a contract is assigned to the assertion, and the contract has two authentication methods (such as one for name/password and another for X.509), the server sending the assertion might use only name/password, but the service provider might assume that X.509 took place and then incorrectly assert it to another server.
-
Select one of the following options for user identification:
-
Do nothing: Specifies that an identity provider account is not matched with a service provider account. This option allows the user to authenticate the session without identifying a user account on the service provider.
-
Attribute matching: Authenticates a user by matching a user account on the identity provider with an account on the service provider. This option requires that you set up the match method.
-
Prompt for password on successful match: Specifies whether to prompt the user for a password when the user is matched to an account, to ensure that the account matches.
-
-
-
Select one of the following:
-
If you selected , continue with Step 6.
-
If you selected , continue with Section 12.2.2, Configuring the Attribute Matching Method for SAML 1.1.
-
-
You can also configure the assertion time manually.
-
Assertion Validity Window: You can manually set the assertion validity time for SAML Service Provider (SP) to accommodate clock skew between Service Provider and SAML Identity (IDP) Server.
-
-
Click twice.
-
Click to make the user identification configuration changes.
-
Update the Identity Server.
12.2.2 Configuring the Attribute Matching Method for SAML 1.1
A user matching expression is a set of logic groups with attributes that uniquely identify a user. User matching expressions enable you to map the Liberty attributes to the correct LDAP attributes during searches. You must know the LDAP attributes that can be used to identify unique users in the user store.
In order to use user matching, the Personal Profile must be enabled. It is enabled by default. If you have disabled it, you need to enable it. See Section 14.2, Managing Web Services and Profiles.
-
In the Administration Console, click > > > > > >
-
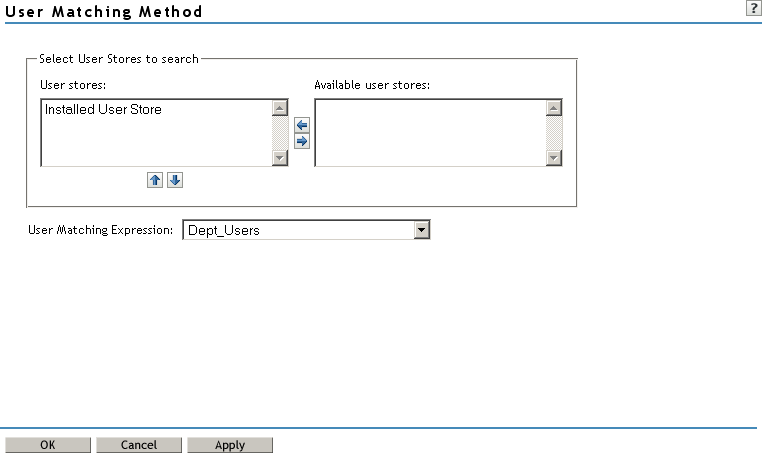
To configure the match method, click .
-
Select and arrange the user stores you want to use.
Order is important. The user store at the top of the list is searched first. If a match is found, the other user stores are not searched.
-
Select a matching expression, or click to create a look-up expression. For information on creating a look-up expression, see Section 6.3, Configuring User Matching Expressions.
-
Click .
-
Update the Identity Server.