8.1 Overview of the CardSpace Authentication Process
CardSpace puts the users in control of managing the cards that they want to use for identity information and credentials. With a CardSpace client, the users can create managed cards and personal cards for authentication to the Novell Identity Server. Figure 8-1 illustrates this process.
Figure 8-1 The Relationship between Cards and Providers
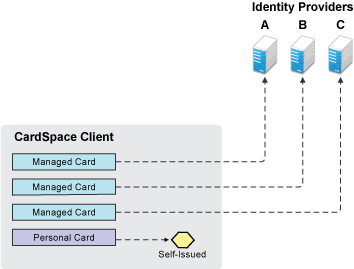
Managed cards come from an identity provider. When the users interact with the Identity Server, they can install a managed card from the Identity Server into the CardSpace client. The managed card provides metadata to CardSpace about how to interact with the Identity Server, which includes the available attributes (claims).
Personal cards are created with the CardSpace client software, and the user decides which attributes are available.
The purpose of a card is to define the source for the identity, the provider of the authentication token, and the credentials provided in the token. Figure 8-1 illustrates that the provider for the identity and token can be either an identity provider when a managed card is selected or the CardSpace client when a personal card is selected.
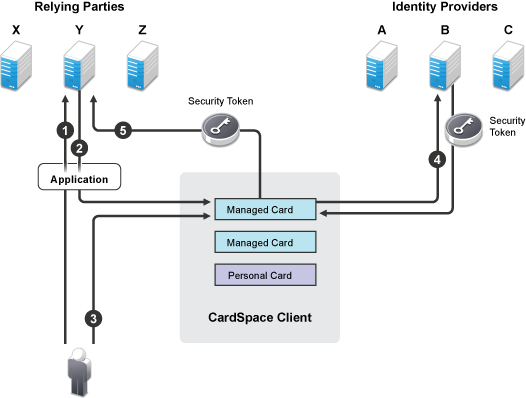
Figure 8-2 illustrates the process when a relying party requests a token.
Figure 8-2 Using a Card for Authentication
-
The user requests access to an application, and the application sends the request to the relying party.
-
The relying party returns the security token requirements, which include the issuer ID, the required attributes, and the token type to CardSpace.
-
The CardSpace client software highlights the cards that meet the requirements, and the user selects the card to use.
-
The CardSpace client software requests a security token from its configured trusted identity provider, and the identity provider returns the security token.
-
The CardSpace client software presents the token to the relying party, and if it matches the requirements, the user is granted access.
The Novell Identity Server can be configured to act as relying party or as an identity provider. It can be configured to accept the following types of cards for authentication: personal cards, managed cards, and managed cards backed by personal cards.