3.3 Key Component I&A
The I&A processes between key components are described in this section:
3.3.1 Operations Server Servers
You can connect multiple Operations Center servers for different reasons, such as load balancing or creating a gateway to establish a single connection for users outside their firewall. Operations Center uses adapter technology to establish connections and interactions between Operations Center servers. Operations Center adapters are restricted by their credentials and optionally by a trusted list of IP addresses. This combination identifies the Operations Center servers from which the adapters can accept and process information requests.
Adapters are configured with a one-to-one relationship, where one adapter communicates with a specific Operations Center server. To establish communication between two Operations Center servers, the Operations Center administrator must configure an InterCommunication adapter (ICA) on each Operations Center server. See the Operations Center 5.5 Adapter and Integration Guide for details on creating and configuring adapters.
During the adapter configuration, the Operations Center administrator defines a set of credentials (such as an account name and password) for each Operations Center server that communicates with another Operations Center server. Server credentials are stored on each Operations Center server and the passwords are also encrypted and stored.
Whether the environment is in secured or unsecured mode, communication between Operations Center servers always involves transmitting the credentials in encrypted form and comparing them to the credential data stored on the remote Operations Center server.
The Operations Center server must trust its own certificate. Otherwise, the threads used to connect to itself fail and other applications, such as the dashboard, cannot log in.
Figure 3-5 illustrates how communication between Operations Center servers transmits credentials in encrypted form:
Figure 3-5 Encryption Between Operations Center servers
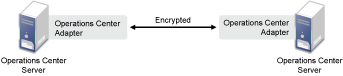
Upon successful authentication, the Operations Center server is allowed access to the remote Operations Center server based on its assigned levels of access, as defined in the Operations Center access control lists.
In some cases, organizations place Operations Center servers outside the firewall and leverage their firewalls to ensure more secure communications.
3.3.2 Operations Center Server to Remote Management System
Operations Center uses adapter and ORB technology to establish connections and interactions with third-party management systems. Adapters are configured with a one-to-one relationship, where one adapter talks to a specific management system either directly or through an ORB. See the Operations Center 5.5 Adapter and Integration Guide for details on creating and configuring adapters and ORBs. Operations Center adapters and ORBs are identified by their credentials and optionally by a trusted list of IP addresses. This combination identifies the Operations Center adapters and ORBs from which the server accepts and process information requests.
When a management system does not require an ORB, the Operations Center adapter passes its credentials along with the information requests to the remote management system.
When a management system requires an ORB, the Operations Center administrator must configure both a Operations Center adapter and a Operations Center ORB.
Operations Center ORBs execute using their own credentials. When configuring an ORB, the Operations Center ORB administrator defines the ORB’s credentials (such as a service account and password, if needed). These credentials are sometimes used to assign rights in the remote management system. The ORB’s credentials are encrypted and stored locally with the Operations Center server, and are passed to the ORB when making a connection.
When configuring an adapter that uses an ORB for management system communication, the Operations Center administrator typically defines in the Operations Center server the ORB’s credentials and its location on the network (such as the IP address). The ORB credentials are stored on the Operations Center server and the password is encrypted and stored. An ORB can be configured to only accept a connection from a single IP address, to further insulate its possible connection paths.
When communicating with an ORB, the Operations Center adapter transmits the ORB’s credentials to the ORB in an encrypted format. The ORB authenticates the credentials and processes the request. Communication between the adapter and the ORB is accomplished using CORBA APIs.
Figure 3-6 Encryption Between Operations Center server and ORB

Operations Center uses adapter and ORB technology to establish connections and interactions with third-party management systems.
When a Operations Center ORB accepts a request from a Operations Center server through its adapter, it passes its credentials along with the information requests to the remote management system. Communication between the ORB and the remote management system is accomplished by using the management platform’s defined API or database connection.
3.3.3 Operations Center Server to Web Server I&A
Operations Center uses Apache Tomcat as its internal Web server, but Operations Center does not use Tomcat’s authentication. Operations Center prompts users to provide their credentials to access the Operations Center server. The Operations Center session is maintained within the HTTP session.
3.3.4 Operations Center Server to Database I&A
Operations Center uses database management systems (DBMS) for several purposes:
-
To store system configuration data
-
To store historical alarm (including audit alarms) and performance data
-
To store portal configuration data
The interface between the DBMS and Operations Center engine consists of Java Database Connectivity (JDBC) API calls.
Operations Center uses Windows authentication when communicating with a third party DBMS on the Windows platforms.
For information on how to configure Single Sign On (SSO) for Operations Center databases, see Configuring and Administering the Database
in the Operations Center 5.5 Server Configuration Guide.
3.3.5 Operations Center server to SQL Views and Web Services
When using SQL Views, the Operations Center user ID and password are used to access data. The data is transferred unencrypted between the requesting application and SQL Views.