6.3 Firewalls
An important configuration consideration is the use of firewalls in your environment. Is there a firewall between the Operations Center server and end users? Is there a firewall between the Operations Center server and the underlying management systems?
A common approach is to place a firewall between the external Internet world and the local network, but allow external users to access the Operations Center server over the Internet. By default, Operations Center is installed with a specific port for HTTP and a range of ports for the IIOP communications. In most cases, you should configure the Operations Center server to utilize one specific port for IIOP, then configure the firewall to allow external traffic to access the internal network using this specific port.
Other variations might require the Operations Center server to connect through a firewall to a data source, such as a management system or a database. In some cases this is an easy exercise. However, depending on the data source, internal security policies might not allow the communication.
Review the following sections for information on using firewalls:
6.3.1 Firewall between Operations Center server and Console
Figure 6-2 shows a Operations Center system with users who are outside the network:
Figure 6-2 Operations Center Configuration for Users Outside the Network

For the dashboard, the only connection established from the outside is the HTTP or HTTPS port specified. Operations Center consoles require the HTTP or HTTPS and the IIOP (Corba) port.
6.3.2 Firewall between Operations Center server and Management Systems
Figure 6-3 shows a firewall between the Operations Center server and an actual data integration point, such as an IBM Micromuse Netcool system, a database through BDI, or an HP OpenView NNM:
Figure 6-3 Firewall Configuration between Operations Center server and Management Systems
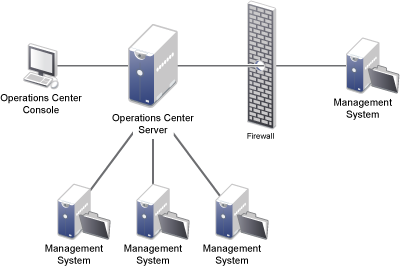
Each system allows a ports to be configured on the firewall to enable communication. The specific port could be a configurable item on the adapter, ORB, or in the underlying management system.
For example, for Netcool, configure the port in the Netcool system. The Operations Center adapter is informed of the port to use. In the case of OpenView, during the ORB installation, use the option to specify the port. Then specify the same port number in the OpenView adapter properties.
6.3.3 Operations Center server in DMZ
In computer security, a demilitarized zone (DMZ), more appropriately known as demarcation zone or perimeter network, is a physical or logical subnetwork that contains an organization’s external services to a larger, untrusted network, usually the Internet. The purpose of a DMZ is to add an additional layer of security to an organization’s Local Area Network (LAN).
Figure 6-4 shows an example of a Operations Center system outside the network in a DMZ:
Figure 6-4 DMZ Configuration for Operations Center

The Operations Center system on the outside is configured with an ICA adapter. The DMZ server can have views for the Operations Center console and/or the dashboard. Regardless, the firewall traversal requires the initial HTTP or HTTPS connection as well as the IIOP connection.