4.6 Graded Authentication Example
Departments within a company are often assigned security classifications that are based on the department's function and the kind of information that it handles. For example:
-
Human Resources handles sensitive information such as personnel files.
-
Engineering handles restricted or confidential information such as product specifications and schematics.
-
Sales handles public information that is freely accessible.
-
Finance handles sensitive information critical to the operation and survival of the company.
Depending upon the sensitivity of the information, it might be secured in locked filing cabinets that serve as access control mechanisms. Access control to this information is with a separate key for each filing cabinet issued to a person authorized to access the information.
Graded authentication replaces the physical key given to users with a clearance. Also, NMAS replaces the filing cabinet with NetWare file system volumes that are also assigned security labels. These security labels replace the filing cabinet lock type.
As the network administrator, you assign users authorization levels for login. When a user logs in, the user is assigned a clearance for that login session. The clearance becomes the key that is necessary for access. Access is granted to the user based on the clearance (key) that the user is authorized to hold and the security label (lock) that is being accessed.
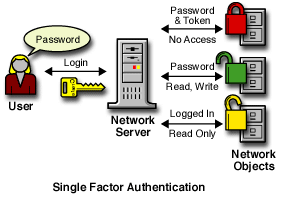
Although a user can be authorized to have more than one clearance, only one clearance is assigned at login, and it is this clearance that determines what information can be unlocked. For example, the following would apply (as illustrated in Figure 4-1) to a user logging in with an authentication grade of Password:
-
Read/Write access to network resources labeled Password.
-
No access to resources labeled Password and Token, because this label is higher than the Password clearance.
-
Read-only access to any information labeled with a lower label than Password (for example, Logged In).
Figure 4-1 Single-Factor Authentication
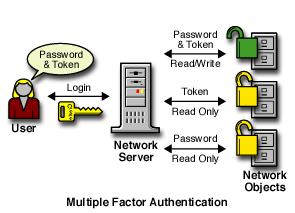
The following would apply (as illustrated in Figure 4-2) to a user logging in with a password and token:
-
Read/write access to network resources labeled Password and Token.
-
Read-only access to any information labeled with a lower label than Password and Token, including Password and Logged In.
Figure 4-2 Multiple-Factor Authentication
A user working in Human Resources with information classified as sensitive logs in with a Password & Token clearance. The information that the user needs is on a network volume that is also labeled Password & Token. Because the user's clearance and the volume security label match (the Read label dominates the volume label and the volume label dominates the Write label), the user is able to read from and write to the NetWare volume.
However, suppose the same user attempts to copy the sensitive information to a network area that requires only a password for access. Graded authentication prevents this action because copying or moving information from a higher label to a lower label is not allowed. This prevents the user from compromising the sensitive information.
The following table shows how several departments within a company might classify their information. Security labels and clearances are assigned based on the information classification and not on a user.
Table 4-4 Information Classification and Security Labels
|
Department |
Information Classification |
Assigned Security Label (Lock) |
Assigned Clearance (Key) |
|---|---|---|---|
|
Human Resources |
Sensitive |
Password & Token |
Password & Token |
|
Engineering |
Confidential |
Password |
Password |
|
Sales |
Public |
Logged In |
Logged In |
|
Finance |
Sensitive |
Biometric & Token |
Biometric & Token |
In this example, because Sales has been assigned a Public clearance and Sales information is freely accessible, a user only needs to be logged in to access Sales information.
However, users who work in Engineering must use a password to access the confidential information needed for their job function. Engineering's data volumes would also be labeled Password for read/write access.
Human Resources often deals with sensitive information related to personnel records. A password and token are required to access this information.
Finance also has sensitive classified information and considers financial information critical to the company's operation and survival. A biometric and token are required to access this information.