4.2 Configuring for Two-Factor Authentication Using Time-Based One-Time Password (TOTP)
This section explains how to use Google Authenticator Time-Based One-Time Password (TOTP) as a second authentication factor with Access Manager. The Google Authenticator uses a six-digit number (OTP) in addition to first authentication (for example: username, password), to log into protected services.
The first step is to register the Google Authenticator client with the secret key. This secret key is used for all future logins to the Web Site.
Typically, users download and install the Google Authenticator app on their devices. To log into a Web Site or service that uses two-factor authentication, in addition to the user name and password, the users enter a additional OTP generated by the Google Authenticator app. Access Manager validates the OTP and authenticates the user.
For more information about implementation, see Google Authenticator on Wikipedia
4.2.1 Why Two-Factor Authentication?
Two-factor authentication such as TOTP provides additional security for the systems. It works on the principle of granting access based on a knowledge factor (something the user has) and a possession factor (something the user knows). This helps organizations that need to implement a multi-factor authentication scheme to satisfy regulatory requirements or increase security.
4.2.2 Prerequisite
-
Download and install the Google Authenticator app on your device. This app generates an OTP that is later used for authentication.
-
Google Authenticator relies on the device time (of the Google Authenticator app) to generate an OTP. So, it is important that the time on your device is accurate.
4.2.3 Configuring TOTP Class, Method, and Contract
Use the Administration Console to define a new TOTP Authenticator class, method, and contract for the Identity Server cluster.
-
Log in to the Administration Console.
-
Click Devices > Identity Servers > Edit > Local > Classes > News to add a new class.
-
Specify a name to identify the class. For example, Google authenticator.
-
Select TOTPClass from the Java Class option. The Java class path is displayed as com.novell.nidp.authentication.local.TOTPAuthenticationClass. Click Apply to save the changes. By default, the TOTP class stores the secret key in the Shared Secret store and no further configuration is required.
-
[Optional] You can also optionally store the secret key in an LDAP attribute, file or memory. To do that follow the steps outlined in this table:
NOTE:File and Memory class implementation are not recommended for production deployment and are only suitable for a single node Identity Server test environment.
LDAP user attribute: This option stores the secret key on an LDAP attribute of the user object in the user store.
-
Select the Properties tab of the Google Authenticator class configuration. Add a new property to indicate that the secret key should be stored in an LDAP attribute of the user object in the user store.
Specify the Property Name as SECRET_STORE_CLASS and Property Value as USERSTORE.
-
Add another property to indicate the attribute in which the secret key should be stored.
Specify the Property Name as SECRET_LDAP_ATTRIBUTE_NAME and specify the name of any single-valued attribute. For example, you can specify the Property Value as mobile, costcentre etc.
The secret key is encrypted and stored in the LDAP attribute. If you do not specify any Property Value, the secret key is stored in the carLicense LDAP attribute.
NOTE:Do not use a multi-valued LDAP attribute like email address as the Property Value as the user registration will fail. It is also important to ensure that the LDAP attribute you have specified as the Property Value is a non-operational attribute. For example, it is not recommended to use LDAP Attributes like groupmembership.
File class: The File class writes the secret key to a file on the Identity Server file system.
Select the Properties tab of the Google Authenticator class configuration and add a new property to have the user's secret key stored in a file on the file system.
Specify the Property Name as SECRET_STORE_CLASS and Property Value as FILE.
Memory class: The Memory based class writes the secret key into memory. This memory is transient in nature and therefore the secret key value is lost each time the Identity Server is restarted.
Select the Properties tab of the Google Authenticator class configuration and add a new property to define the memory-based property where each user’s secret key is stored.
Specify the Property Name as SECRET_STORE_CLASS and Property Value as MEMORY.
-
-
Click Devices > Identity Servers > Edit > Local > Methods. Select New to add a new method.
-
Specify a name to identify the method. Select the Google authenticator class from drop-down list. This links the Google authenticator class to the authentication method.
-
Deselect the Identifies User option. Click Apply to save the changes.
-
Select the user store from the list of Available user stores and move it to User store.
-
You can either use an existing authentication contract or create a new authentication contract. For example, you can add the default Name/Password – Form method as the first method and Google Authenticator method as the second method. Click Apply to save the changes.
NOTE:If you use TOTP as a post-authentication method in a federation setup, a JSP file not found message is displayed and federation fails.
4.2.4 Registering with Google Authenticator
-
Go to NetIQ Identity Server page http(s)://<idp server >:<port>/nidp
-
Select the contract where Google Authenticator is configured as the second method for two-factor authentication.
-
Login with the first method.
-
Click the link beside Please register for two factor authentication to generate a OTP. Make a note of the secret key displayed.
If you have installed the Google Authenticator client on your device, scan the code. You can also manually enter the secret key in the Google Authenticator mobile client.
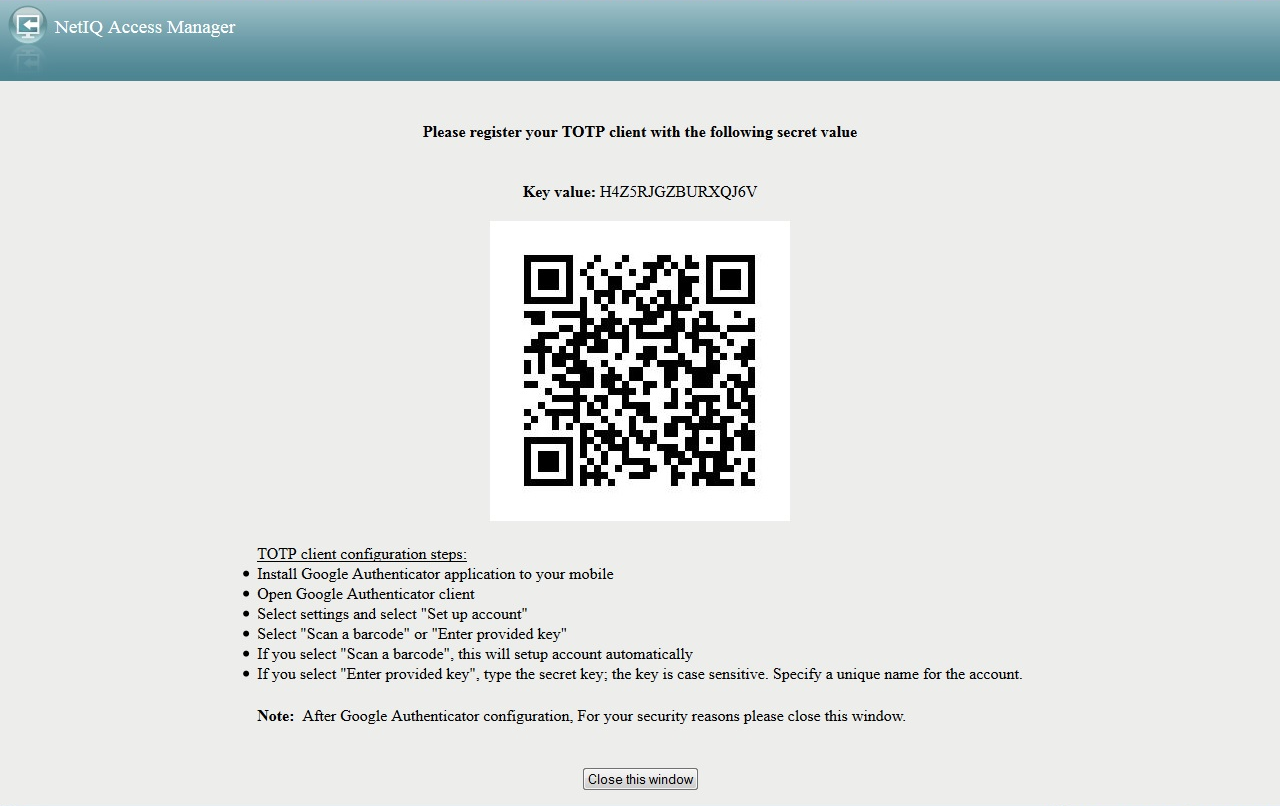
After the registration is complete on the Google Authenticator client on your mobile, the OTP is displayed.
4.2.5 Verifying TOTP Configuration
-
Go to NetIQ Identity Server page: http(s)://<idp server >:<port>/nidp
-
Select the contract where Google Authenticator is configured as the second method for two-factor authentication.
-
Login with the first method.
After successfully authenticating with the username and password, prompt is displayed to enter the Google Authenticator OTP.
-
Use the Google Authenticator app to generate the OTP and login using this OTP.