5.6 Configuring SSL VPN to Monitor the Health of the Cluster
The L4 switches use health checks to determine which cluster members are ready to receive requests and which cluster members are unhealthy and should not receive requests. You need to configure the L4 switch to monitor the heartbeat URL of the Identity Servers and Access Gateways, so that the L4 switch can use this information to accurately update the health status of each cluster member.
5.6.1 Services of the Real Server
A user’s authentication resides on the real (authentication) server cluster member that originally handled the user’s authentication. If this server malfunctions, all users whose authentication data resides on this cluster member must reauthenticate.
Requests that require user authentication information are processed on this server. When the system identifies a server as not being the real server, the HTTP request is forwarded to the appropriate cluster member, which processes the request and returns it to the requesting server.
A Note about Alteon Switches
When you configure an Alteon* switch for clustering, direct communication between real servers must be enabled. If direct access mode is not enabled and one of the real servers tries to proxy another real server, the connection fails and times out.
To enable direct communication on an Alteon switch:
-
Go to cfg > slb > adv > direct.
-
Specify e to enable direct access mode.
With some L4 switches, you should configure only the services that you are using. For example, if you configure the SSL service for the L4 switch and you have not configured SSL in Access Manager, then the HTTP service on the L4 switch does not work. If the health check for the SSL service fails, the L4 switch assumes that all the services configured to use the same virtual IP are down.
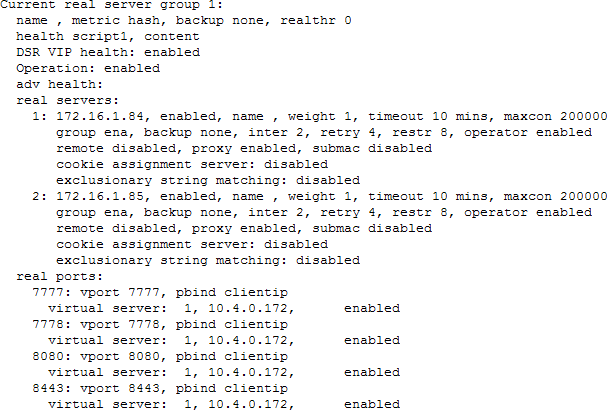
Real Server Settings Example
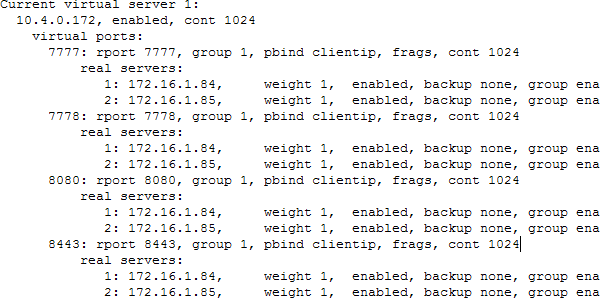
Virtual Server Settings Example
5.6.2 Monitoring the SSL VPN Server Health
The health status of the SSL VPN server can be monitored by using the heartbeat URL. The heartbeat URL uses the DNS name of the SSL VPN server as follows:
https://<SSLVPN DNS NAME>/sslvpn/heartbeat
L4 switches require you to use the IP address rather than the DNS name. If the IP address of the SSL VPN server is 10.10.16.50, and you have configured it for HTTPS, the heartbeat URL is:
https://10.10.16.50:8443/sslvpn/heartbeat
You must configure the L4 switch to use this heartbeat to perform a health check. If you have configured SSL on the SSL VPN servers and your L4 switch has the ability to do an SSL L7 health check, you can use HTTPS. The SSL L7 health check returns a value of 200 OK, indicating everything is healthy. Any other status code indicates an unhealthy state.
For a Foundry* switch, the L7 health check script string should look similar to the following when the hostname is sslvpn1 and the IP address is 10.10.16.50:
healthck sslvpn1ssl tcp dest-ip 10.10.16.50 port ssl protocol ssl protocol ssl url "GET /sslvpn/heartbeat HTTP/1.1\r\nHost: st160.lab.tst" protocol ssl status-code 200 200 l7-check
If your switch does not support an SSL L7 health check, the HTTPS URL returns an error, usually a 404 error. The SSL VPN Server heartbeat URL listens on both HTTPS and HTTP, so you can use an HTTP URL for switches that do not support the SSL L7 health check. For example:
http://10.10.16.50:8080/sslvpn/heartbeat
An Alteon switch does not support the L7 health check, so the string for the health check should look similar to the following:
open 8080,tcp send GET /sslvpn/heartbeat HTTP/1.1\r\nHOST:heartbeat.lab.tst \r\n\r\n expect HTTP/1.1 200 close