2.2 Possible Configurations
The J2EE server uses the Identity Server for authentication.You can configure your J2EE server in such a way that either the users have direct access to it or the J2EE server is a protected resource of the Access Gateway.
2.2.1 Allowing Direct Access to the J2EE Server
This scenario is most often used when you have users who want to access the application server behind your firewall. This configuration requires an internal DNS server that resolves the DNS name of the application server to its IP address.
When you configure the Identity Server to provide authentication for the applications on the J2EE server, the communication process follows the paths illustrated in Figure 2-1.
Figure 2-1 JBoss Applications Using the Identity Server
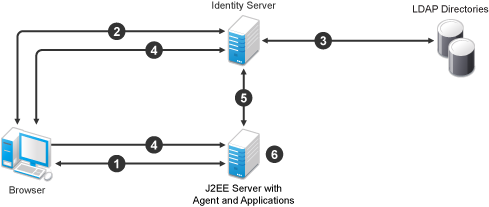
-
The user requests access to an application on the J2EE server. The user is redirected to the Identity Server.
-
The Identity Server prompts the user for a username and password.
-
The Identity Server verifies the username and password against a user store (an LDAP directory).
-
The Identity Server builds the roles for the user and redirects the user back to the application server.
-
The agent verifies the user’s credentials and obtains the user’s role information.
-
The application server allows access to the requested application.
For configuration information, see Section 2.0, Configuring the Agent for Authentication.
2.2.2 Protecting the Application Server with the Access Gateway
In this scenario, the J2EE server with the application is protected by the Access Gateway. The Access Gateway is a reverse proxy server that restricts access to Web-based content, portals, and Web applications that employ authentication and access control policies.
When you configure the Access Gateway to protect the application server, the communication process follows the paths illustrated in Figure 2-2.
Figure 2-2 The J2EE Server as a Protected Resource
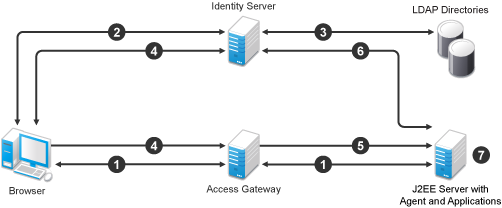
-
The user requests access to the application server by using a published DNS name. The request is sent to the Access Gateway, and the Access Gateway proxies the request to the agent.
-
The agent redirects the request to the Access Gateway, and the Access Gateway redirects the user to the Identity Server, which prompts the user for a username and password.
-
The Identity Server verifies the username and password against a user store (an LDAP directory).
-
The Identity Server builds the roles for the user and redirects the user back to the Access Gateway.
-
The Access Gateway directs the user’s request to the application server.
-
The agent verifies the user’s credentials and obtains the user’s role information.
-
The application server allows the user to access to the requested application.
For configuration information, see Section 2.5, Protecting the Application Server with the Access Gateway.