2.1 Configuration Options
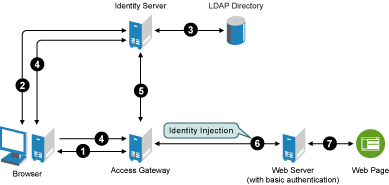
A typical Access Manager configuration includes an Identity Server with LDAP directories and an Access Gateway with a protected Web server. Figure 2-1 illustrates the process flow that allows an authorized user to access the protected resource on the Web server.
Figure 2-1 Accessing a Web Resource
-
The user requests access to a resource protected by the Access Gateway.
-
The Access Gateway redirects the user to the Identity Server, which prompts the user for a username and password.
-
The Identity Server verifies the username and password against an LDAP directory (eDirectory, Active Directory, or Sun ONE).
-
The Identity Server returns an authentication success to the browser and the browser forwards the resource request to the Access Gateway.
-
The Access Gateway verifies that the user is authenticated and retrieves the user’s credentials from the Identity Server.
-
The Access Gateway uses an Identity Injection policy to insert the basic authentication credentials in the HTTP header of the request and sends it to the Web server.
-
The Web server grants access and sends the requested page to the user.
When you are setting up the Access Gateway to protect Web resources, you create and configure reverse proxies, proxy services, and protected resources. The following figure illustrates the hierarchy of these modules and the major configuration tasks you perform on each module.
Figure 2-2 Access Gateway Modules and Their Configuration Options
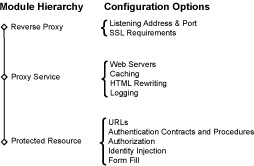
This hierarchy allows you to have precise control over what is required to access a particular resource, and also allows you to provide a single sign-on solution for all the resources protected by the Access Gateway. The authentication contract, authentication procedure, Authorization policy, Identity Injection policy, and Form Fill policy are configured at the resource level so that you can enable exactly what the resource requires. This allows you to decide where access decisions are made:
-
You can configure the Access Gateway to control access to the resource.
-
You can configure the Web server for access control and configure the Access Gateway to supply the required information.
-
You can use the first method for some resources and the second method for other resources or use both methods on the same resource.