2.2 Using the Identity Tracking Solution Pack
The Identity Tracking Solution Pack provides controls (views and reports) of events associated with users. Through these controls, you can monitor and report on account management activities (creation, deletion, and modification); suspicious user activities such as failed authentication, denied access, denied or increased account privileges, and impersonated account logins; account usage by users; and password management activities. Because of the identity injection provided by the Sentinel driver and Identity Vault Collector, events are associated to individual users.
The Identity Tracking Solution Pack provides high-level, identity-based controls that can help solve management and security problems within even the largest enterprises. Leveraging Novell's years of industry experience in Identity and Access Management, the solution pack integrates data from Novell and third-party applications to give unprecedented visibility into user activities and identity/account management.
2.2.1 Overview of the Identity Tracking Solution Pack
This section provides a brief overview of the components within the Identity Tracking Solution Pack.
The solution pack contains the following categories and controls:
Table 2-1 Solution Pack Controls
The content provided with the Identity Tracking Solution Pack includes several correlation rules, actions, integrators, and reports.
The reports are described below:
Table 2-2 Solution Pack Reports
2.2.2 Solution Samples
This section displays some sample results from the Solution Pack controls. Note that in the customer environment results will vary depending on the local configuration of event sources and control parameters.
-
The report presents identity provisioning activity for all the identities within the selected department and date range:
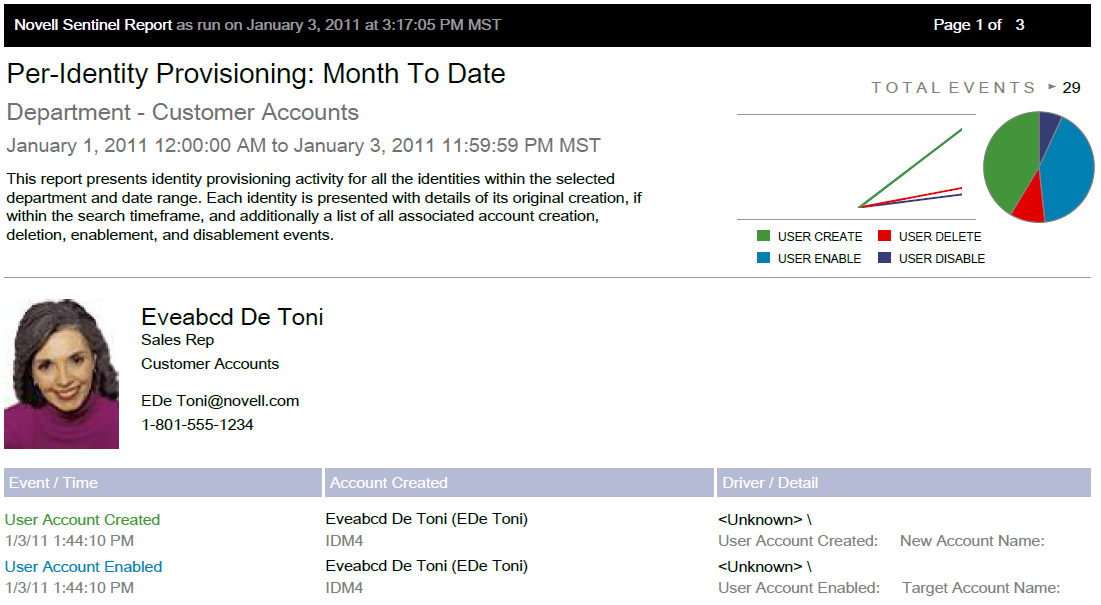
-
The report presents any attempts to access enterprise resources by terminated employees within the selected date range, grouped by the incident status:
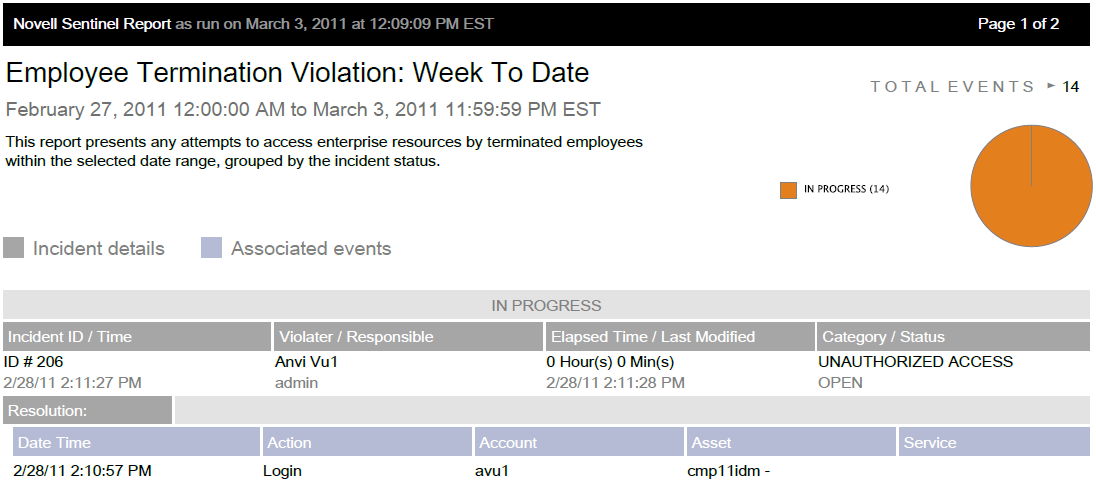
-
The report presents account management activity for an Identity within the selected date range, grouped by the domain within which each account exists and the account name:
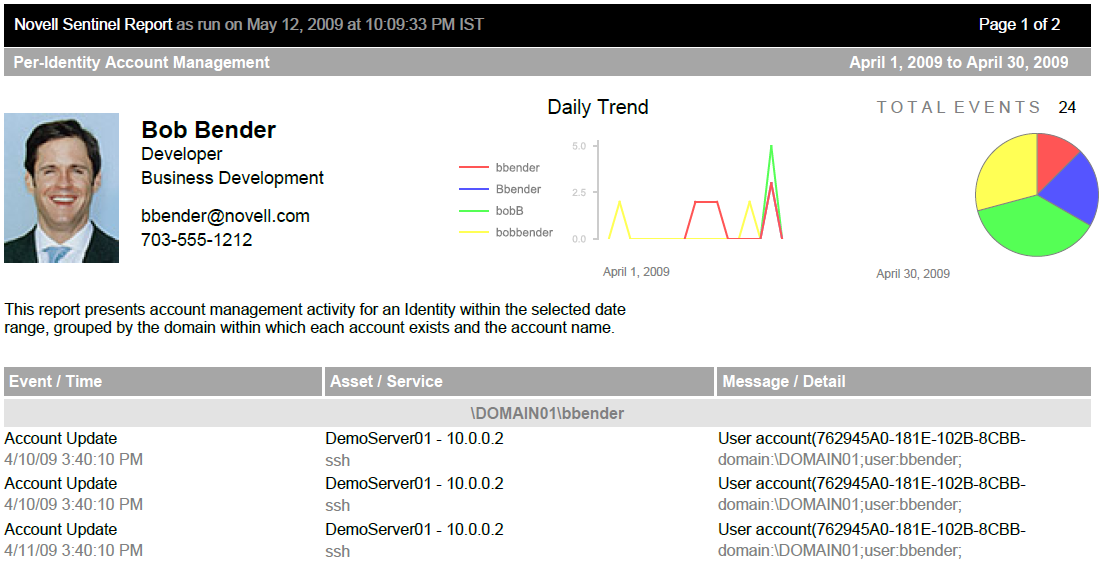
2.2.3 Installing the Identity Tracking Solution Pack
To install the Identity Tracking Solution Pack:
-
Start the Sentinel Control Center and log in as a user with rights to manage Solution Packs.
The Solution Manager option must be selected for the user, under .
-
Select s from the menu to start the Solution Pack Manager.
-
Click to start the import wizard.
-
Select , then click .
-
Browse to and select the Identity Tracking Solution Pack where you downloaded it, then click .
The filename is Identity-Tracking_6.1r4.spz.zip.
-
Review the Solution Pack directory, then click .
-
Review the Solution Pack details, then click .
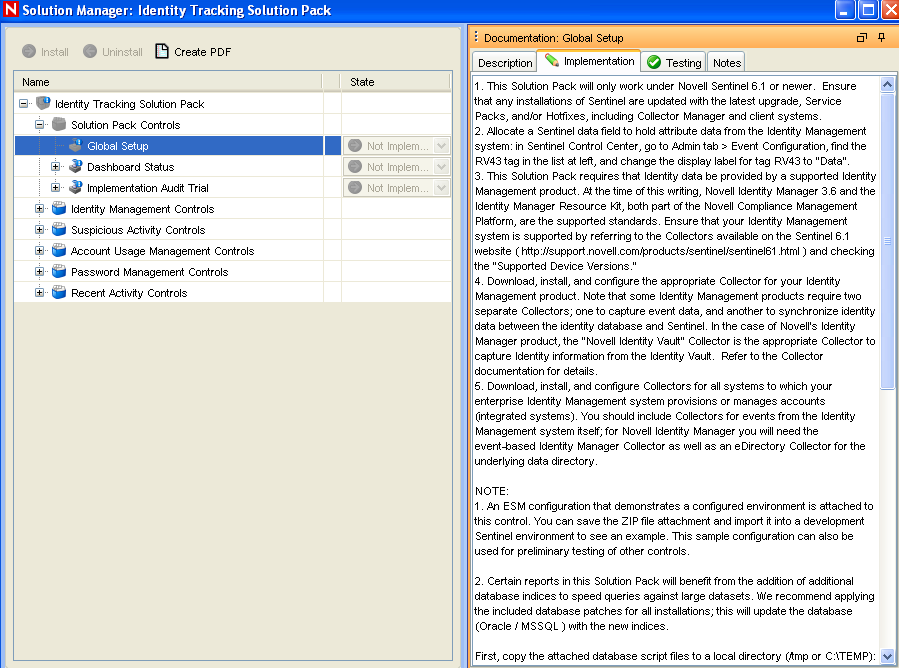
2.2.4 Configuring the Global Setup
The Identity Tracking Solution Pack requires some global configuration that must be completed. This configuration needs to be completed before any additional configuration. The configuration information is contained in the Identity Tracking Solution Pack.
If you have completed these global configuration task for another use case, you can skip the following sections:
Accessing the Global Setup Configuration
To access the Global Setup configuration information:
-
In the Sentinel Control Center tool bar, click > .
-
Double-click the Identity Tracking Solution Pack entry in the Solution Packs Manager.
-
In the left pane, select > > , then click the tab in the right pane.
Installing the Controls
To install the controls included with the solution pack:
-
Right-click a control (such as Dashboard Status) in the list displayed under Solution Pack Controls.
-
Click from the pop-up menu.
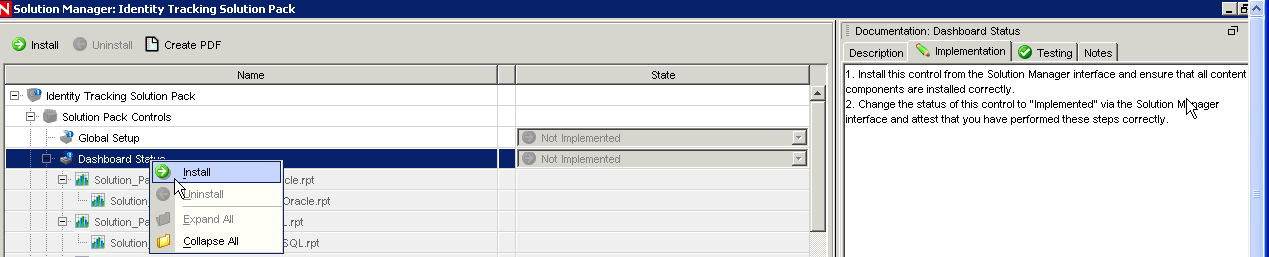
You need to do this for each control you plan to use.
Configuring the Sentinel Data Field
The Sentinel data field must be able to hold Identity Manager attribute data.
-
Start the Sentinel Control Center, then click the tab.
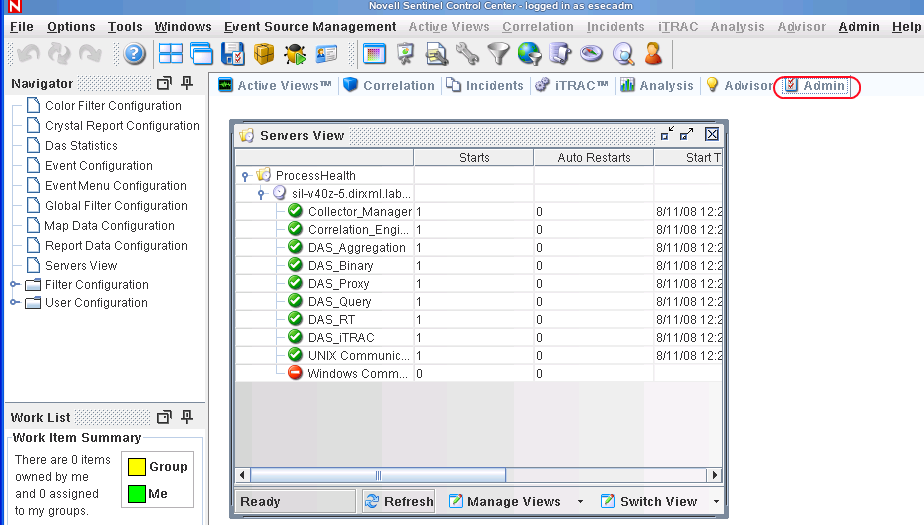
-
Select from the tool bar
-
In the left pane, locate the rv43 variable, which may have already been labeled or .
-
In the field in the right pane, change the display label to , then click .
-
Click , then close the Event Configuration window and reopen it to see the changes take place.
Adding SQL Indexes to Speed Up Queries
The performance of queries for certain reports in the Identity Tracking Solution Pack is increased if you add indexes to the database. These indexes increase the speed of queries against the large database. The Identity Tracking Solution Pack provides instructions on how to add the indexes.