3.4 Creating Custom Entitlements
In an enterprise, entitlement servers as granting agent. Custom entitlements helps to control the permission parameters such as user accounts, group memberships., resources access.
The Permission Collection and Reconciliation Services (PCRS) help you to create entitlements that you can map with resources in the Identity Vault. You can dynamically create resources with custom entitlement populated with permission values of connected system, and permission assignments between Identity Manager resource/entitlement model and connected systems.
Unlike other drivers, the REST packages do not include the default entitlements. However, you can customize the REST driver to support the default entitlements such as useracccount and group membership. The driver also supports other entitlements such as printers, conference rooms, floor access, and so forth.
The Identity Manager driver for REST installed with Permission Collection and Reconciliation Service packages perform the following actions:
-
Provide a way to create custom entitlements and resources specific to your environment.
-
Reconcile resource or permission assignments between the Identity Vault and connected systems.
For example, let’s consider a deployment scenario in which the Identity Vault connects with the SCIM server as the target system.
You can define a new role “Manager” in the SCIM server and assign users to this role. You can define the Manager role as a custom entitlement and when the driver returns the custom entitlements from the connected system, all users assigned with this role is created and mapped as resources in the Identity Vault. The REST driver synchronizes the permission updates from the connected system and updates the Identity and Resource Catalog.
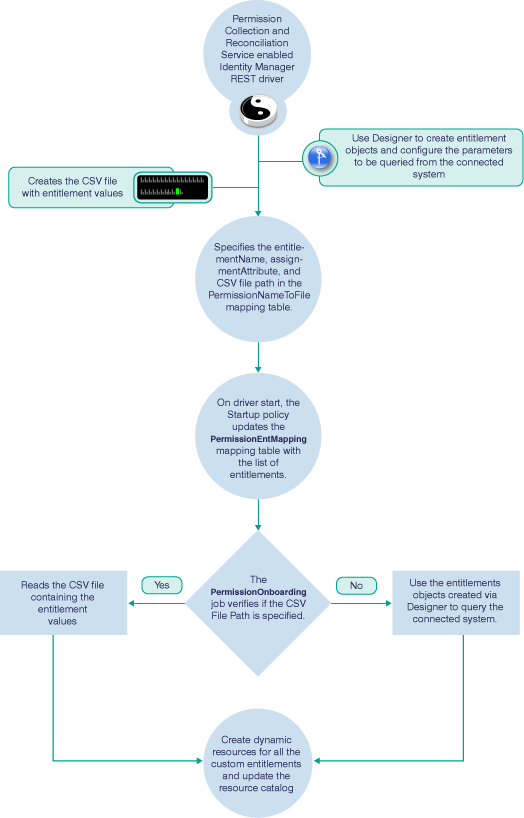
Figure 3-1 illustrates the process of creating resources using PCRS:
Figure 3-1 Permission Collection and Reconciliation Service Flow
IMPORTANT:In the Driver Configuration, ensure that you configure the resources in the Subscriber Setting. You should configure the Schema name as Entitlement and the required handlers for the PCRS to work. For more information, see Resources.
For creating custom entitlements, you should specify the entitlement value, attribute, and CSV file path in the PermissionNameToFile mapping table in the Driver Configuration page. The REST driver uses either the CSV file or query the connected system to populate entitlement values. If the custom entitlements are not dependent on the values from the connected system, use the CSV file to provide the entitlement values to create entitlements and resources. If the custom entitlements are dependent on the values from the connected system, create entitlements objects using Designer and specify the information required for querying the connected system.
In the CSV file, the administrator must provide the entitlement values of the connected system in the specified format that includes the entitlement value, the display name and the description. You must place the CSV file containing the entitlement values on the server where Identity Manager engine is installed. Ensure that you update the csvFile column in the PermissionNameToFile mapping table with the correct path for the CSV file. The REST driver access the custom entitlement information from the CSV file.
For any REST driver enabled with PCRS, to create custom entitlements, you should create the entitlements objects. The Designer tool helps you to create the entitlement objects. You can define the values that must be queried for from the connected system in these entitlement objects. For example, you can create entitlement objects for users and groups. For more information about creating entitlement objects, see “Valued Entitlement that Queries an External Application”
in the NetIQ Designer for Identity Manager Administration Guide.
The PermissionOnboarding job is a standard Identity Manager job and is available in the entitlement package. During the driver startup, the PermissionOnboarding job runs and queries the connected system for resource updates. After you create, deploy, and start the driver, the driver automatically reads the PermissionNameToFile mapping table. If the CSV file name is available in PermissionNameToFile mapping table, the driver consumes the entitlements values from the file and creates the custom entitlements. If the csvFile column in the PermissionNameToFile mapping table is empty, the driver queries the connected system using the entitlement objects. New resources are created with the entitlement values from the CSV file or values obtained as the query response.
The new custom entitlement and the corresponding resource object is created in the Resource Catalog. When the permission assignments change in connected system, the driver policies consume the modified permission values and update the Resource Catalog.
IMPORTANT:
-
If you are querying the connected system to create resources, ensure that entitlement objects are configured correctly. If the entitlement object configuration is wrong, the PermissionOnboarding job fails to create resources for all entitlements provided in the PermissionNameToFile mapping table editor.
-
The entitlement assignments are only for a user class. A user resource is eligible to reconcile and synchronize the entitlement changes. However the assignment attributes can differ as per the requirement.
CSV File Format
The REST driver consumes the entitlement information from the CSV file, which is present on the server where Identity Manager is installed. This file must contain values of the connected system permissions in the format specified below. The connected system administrator should maintain a separate CSV file for every custom entitlement.
For example, a CSV file can contain details about granting access to the users for the ResourcesAccess entitlement. A CSV file that contains ResourceAccess entitlement details represents this information in the following format:
Resource A,Google,The google access Resource B ,Twitter,The twitter access Resource C,Facebook,The facebook access
where Resource A is the entitlement value, Google is the display name in the User Application for the entitlement value Resource A, and The google access is the description for the entitlement value. This description is displayed in the User Application.