13.2 Designing Entitlements
You must know beforehand what you want to accomplish with entitlements. Entitlements work from the functionality you build into Identity Manager drivers through policies. These driver policies implement rules and process the events between the Identity Vault and the managed system. If the policies in the Identity Manager driver do not specify what you want to do, entitlements cannot work. For example, if you don’t specify the action section of the Check User Modify for Group Membership rule in the Command policy, attempts to grant or revoke a group membership entitlement are ignored.
When you know what you want to accomplish with Identity Manager, you can correctly design granting and revoking capabilities for any managed system resources. The following four-step procedure can help you plan to create and use entitlements:
-
Know what you want to accomplish in your business situation. You can design and implement many business solutions through Identity Manager, but you need to know what you want to do before implementing something that isn’t defined. Make a numbered list of what you want to do.
-
Define an entitlement that represents one item from your numbered list. You can create valueless and valued entitlements. Valued entitlements can get their values from an external query, they can be administrator-defined, or they can be free-form. There are examples in Section 13.3, Creating Entitlements through the Entitlement Wizard.
-
Add policies to the Identity Manager Driver to implement the designed entitlement. To create a policy for an Identity Manager driver, you need to be conversant with XSLT or DirXML script to define the way the managed system handles and receives information, and the way NetIQ eDirectory stores information. Unless you are a good DirXML programmer, this is a job for consultants.
-
Set up a managing agent to grant or revoke the entitlement. If you want an automated process, use Role-Based Entitlements; if you want a manual process, use the User Application’s workflow-based provisioning feature. See
Understanding Entitlements
in the NetIQ Identity Manager Entitlements Guide. As you plan your entitlements, use the following sections for more information.
13.2.1 Terminology
Following are some terms that are used throughout this section.
Entitlement: An Identity Vault object that represents a business resource in a managed system.
Entitlement Service driver: Grants and revokes entitlements. For Role-Based Entitlements, the agent is the Entitlements Service driver, which must be initiated for entitlements to work.
Grant or revoke: Granting or revoking an entitlement is controlled by Global Configuration Variables (GCVs) on an Identity Manager driver.
Entitlement consumer: Anything that uses entitlement-related information. Entitlement consumers include iManager, the User Application, and Identity Manager policies.
13.2.2 Entitlement Prerequisites
-
eDirectory 8.7.3 or eDirectory 8.8 with the latest Support Pack
-
Identity Manager 3 or later
-
An Entitlements Service driver
You must have an Entitlements Service driver in each driver set where you want to use entitlements. This requires a very simple, two-step setup for each driver set. To do this, see
Creating Entitlements
in the NetIQ Identity Manager Entitlements Guide. -
A driver configuration that supports entitlements
Before you can use entitlements with a managed system, do one of the following:
-
Import the Identity Manager driver configuration for the driver and specify that the driver has entitlements enabled.
-
Enable your driver to support entitlements. To do this:
-
Create entitlements using Designer.
-
Add the DirXML-EntitlementRef attribute to your driver filter as described in Section 13.2.4, Enabling Entitlements on Identity Manager Drivers.
-
Write policies to implement the entitlements you create in Step 1 under Section 13.2, Designing Entitlements.
-
-
13.2.3 Identity Manager Drivers with Preconfigurations that Support Entitlements
The following drivers include configuration files that already contain entitlements and the policies required to implement the entitlements. These entitlements support the most common scenarios: granting and revoking user accounts, groups, and e-mail distribution lists.
-
Active Directory: Grant and revoke accounts, group membership, Exchange Mailbox
-
GroupWise: Grant and revoke accounts, grant and revoke members of distribution lists
-
LDAP: Grant and revoke user accounts
-
Linux and UNIX: Grant and revoke accounts
-
Lotus Notes: Grant and revoke user accounts and group memberships
-
RACF: Grant and revoke group accounts and group memberships
These are example entitlements and policies that you can use as is if they meet your needs. If not, you can modify them to meet your needs, or you can use them as examples as you implement additional entitlements.
13.2.4 Enabling Entitlements on Identity Manager Drivers
Before you can use entitlements, you must first ensure that your driver has entitlements enabled. You can do this through the Entitlements Wizard as you finish creating entitlements; this applies to both preconfigured and non-preconfigured drivers.
However, if you want to use the preconfigured driver’s entitlements and the infrastructure that supports them, you must enable entitlements when you initially create a driver in Designer or iManager; the preconfigured policies and rules that support the preconfigured entitlements cannot be added later without re-creating the driver. If you import a driver that has entitlements enabled into Designer from an Identity Vault, the imported driver also has entitlements enabled. If you deploy a driver that has entitlements enabled into an Identity Vault, the deployed driver also has entitlements enabled.
You can see if your preconfigured drivers have entitlements enabled by clicking the Outline view, then clicking the Subscriber channel of your selected driver. If entitlements are enabled, you should see the preconfigured entitlements appear under the Subscriber Channel. If entitlements do not appear under the Subscriber Channel in the Outline view, entitlements were not enabled when the driver was initially installed.
However, you can still use entitlements on preconfigured Identity Manager drivers that do not have entitlement preconfigurations enabled. To do this, run the Entitlement Wizard. The last page in the Entitlement Wizard asks if you want to add the DirXML-EntitlementRef attribute to the driver filter, with Yes selected. Click OK. However, because the policies and rules are not in place on the driver, you won’t be able to use their preconfigured entitlements without adding those supporting policies and rules yourself.
Figure 13-2 Enabling Entitlements
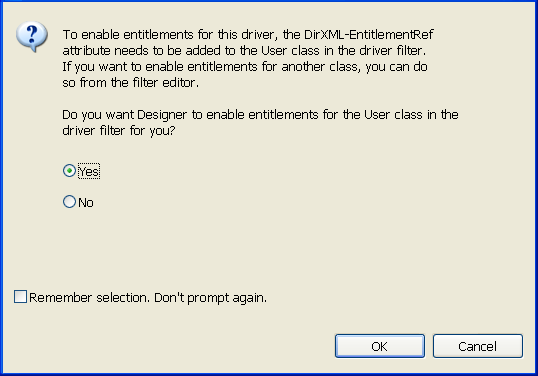
You can also use entitlements on Identity Manager drivers that do not contain entitlement preconfigurations. To enable your driver to support entitlements, add the DirXML-EntitlementRef attribute to your driver filter. Run the Entitlement Wizard as described above to add the DirXML-EntitlementRef attribute to the driver filter.