1.3 User Application User Types
The User Application users fall into these categories:
1.3.1 Administrative Users
The User Application defines several types of administrative users. The administrative users defined in Table 1-3 are defined at installation.
Table 1-3 User Application Administrative Users
|
User |
Description |
|---|---|
|
Identity Vault Administrator |
A user who has rights to configure the Identity Vault. This is a logical role that can be shared with other administrative user types. The Identity Vault Administrator account is a proxy user for the User Application to carry out tasks on the LDAP server that an ordinary user might not have permission to execute, such as creating a new user, group, or container. It represents credentials (username and password) used to bind to the Identity Vault to perform system LDAP operations, so these are the rights that the User Application itself needs to run. The Identity Vault Administrator needs:
|
|
User Application Administrator |
A user who has the rights to perform administrative tasks for the User Application. This user can:
This user does not have any special privileges within the User Application. This user does not need any special directory rights because it controls application level access via the Administration page. Although a User Application Administrator has the ability to manage themes in the Administration page, the User Application uses the LDAP administrator credentials to modify the theme selections in the Identity Vault. Password self-service: One task of the User Application Administrator is to configure password self-service for the User Application. A feature of password self-service is password synchronization status. To enable the User Application Administrator to view the password synchronization status for other users (for troubleshooting or other reasons), NetIQ recommends that you create a PasswordManagement group and assign one or more users to this group. The members of this group are allowed to view the password synchronization status of other users. If you choose to create this group, it must:
IMPORTANT:NetIQ recommends that you use NetIQ Self Service Password Reset (SSPR) for configuring passwords. It is the default password management program for Identity Manager. For more information, see |
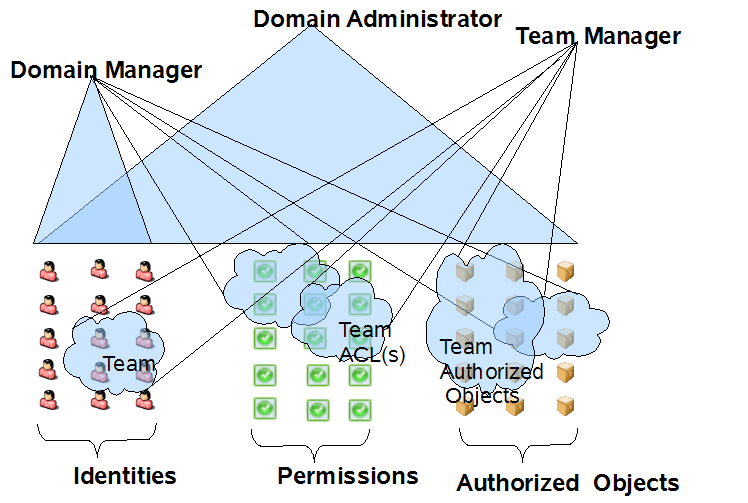
1.3.2 Domain Administrators, Domain Managers, and Team Managers
The Roles Based Provisioning Module uses a security model that recognizes three general categories of administrators and managers:
-
The Domain Administrator is an administrator who has the full range of capabilities within a particular domain, and is able to perform all operations on all objects within the domain for all users.
-
The Domain Manager is a delegated administrator who has the ability to perform selected operations for a subset of authorized objects within the domain for all users.
-
The Team Manager is a business line manager who can perform selected operations for a subset of authorized objects within the domain, but only for a designated set of users (team members).
The following diagram illustrates the security model:
Figure 1-3 Security Model
Domain Administrators and Domain Managers
Domain Administrators and Domain Managers are designated through system role assignments. The Roles Based Provisioning Module allows you to assign users to any of the following system roles:
Table 1-4 System Roles for Domain Administrators and Domain Managers
|
Role |
Description |
|---|---|
|
Compliance Administrator |
The Compliance Administrator is a Domain Administrator who can perform all possible actions for all objects within the Compliance domain. |
|
Configuration Administrator |
The Configuration Administrator is a Domain Administrator who can perform all possible actions on all objects within the Configuration domain. The Configuration Administrator controls access to navigation items with the Roles Based Provisioning Module. In addition, the Configuration Administrator configures the delegation and proxy service, the digital signature service, the provisioning user interface, and the workflow engine. |
|
Provisioning Administrator |
The Provisioning Administrator is a Domain Administrator who can perform all possible actions for all objects within the Provisioning domain. |
|
Provisioning Manager |
The Provisioning Manager is a Domain Manager who can perform only allowed actions for a subset of objects within the Provisioning domain. |
|
Report Administrator |
The Report Administrator is a Domain Administrator who can define report permissions, which include the ability to use the Identity Manager Reporting tool. |
|
Resource Administrator |
The Resource Administrator is a Domain Administrator who can perform all possible actions for all objects within the Resource domain. |
|
Resource Manager |
The Resource Manager is a Domain Manager who can perform only allowed actions for a subset of objects within the Resource domain. |
|
Role Administrator |
The Role Administrator is a Domain Administrator who can perform all possible actions for all objects (except for the System Roles) within the Role domain. |
|
Role Manager |
The Role Manager is a Domain Manager who can perform only allowed actions for a subset of objects within the Role domain. |
|
Security Administrator |
The Security Administrator is a Domain Administrator who can perform all possible actions for all objects within the Security domain. The Security domain allows the Security Administrator to configure access permissions for all objects in all domains within the Roles Based Provisioning Module. The Security Administrator can configure teams, and also assign domain administrators, delegated administrators, and other Security Administrators. NOTE:For testing purposes, NetIQ does not lock down the security model in Standard Edition. Therefore, the Security Administrator is able to assign all domain administrators, delegated administrators, and also other Security Administrators. However, the use of these advanced features is not supported in production. In production environments, all administrator assignments are restricted by licensing. NetIQ collects monitoring data in the audit database to ensure that production environments comply. Furthermore, NetIQ recommends that only one user be given the permissions of the Security Administrator. |
These roles are initialized at install time, but can also be assigned through the Administrator Assignments user interface on the Administration tab. For details on assigning users to the system roles, see Section 7.3, Administrator Assignments.
In Identity Manager 4.5 Advanced Edition, you need to assign the following administrators:
-
User Application Administrator
-
Provisioning Administrator
-
Compliance Administrator
-
Roles Administrator
-
Security Administrator
-
Resources Administrator
-
Configuration Administrator
-
Report Administrator
NOTE:At install time, you can simply specify a User Application Administrator and allow all other assignments to default to this user.
Team Managers
A Team Manager is a user designated as a manager of a team through the Team Configuration user interface on the Administration tab. For details on configuring teams, see Section 7.4, Team Configuration.
1.3.3 Designers
Designers use the Designer for Identity Manager to customize the User Application for your enterprise. Designer is a tool aimed at information technology professionals such as enterprise IT developers, consultants, sales engineers, architects or system designers, and system administrators who have a strong understanding of directories, databases, and their information environment and who act in the role of a designer or architect of identity-based solutions.
To create or edit workflow objects in Designer, the user needs the following rights on the RequestDefs.AppConfig container for the specific User Application driver.
-
[Entry Rights] Supervisor or Create
-
[All Attribute Rights] Supervisor or Write
To initiate a workflow, the user must have Browse [Entry Rights] on the RequestDefs.AppConfig container for the specific User Application driver or individually per request definition object if you are using a delegated model.
1.3.4 Business Users
Business users interact with the User Application’s Identity Self-Service, Work Dashboard, and Roles and Resources tabs. A business user is an authenticated user, such as an employee, a manager, or a delegate or proxy for an employee or manager. A delegate user is a user to whom one or more specific tasks appropriate to that user’s rights can be delegated, so that the delegate can work on those specific tasks on behalf of someone else. A proxy user is user who acts in the role of another user by temporarily assuming that user’s identity. All of the rights of the original user apply to the proxy. Work owned by the original user continues to be owned by that user.
The user’s capabilities within the User Application depend on what features of the User Application Administrator has enabled for them. They can be allowed to:
-
View and edit user information, with appropriate rights
-
Search for users or resources using advanced search criteria, which can be saved for later reuse
-
Recover forgotten passwords
The User Application can be configured so that users can:
-
Request a resource (start one of potentially many predefined workflows)
-
View the status of previous requests
-
Claim tasks and view tasklists (by resource, recipient, or other characteristics)
-
View proxy assignments
-
View delegate assignments
-
Specify one’s availability
-
Enter proxy mode to claim tasks on behalf of another
-
View team tasks and request team resources