5.3 Password Management Configuration
This section describes how to configure password self-service and user authentication features to your Identity Manager User Application.
5.3.1 About Password Management Features
The password management features supported by an Identity Manager User Application encompass user authentication and password self-service. When you put these features into use, they enable your application to:
-
Prompt for login information (username and password) to authenticate against eDirectory
-
Provide users with password change self-service
-
Provide users with forgotten password self-service (including prompting for challenge responses, displaying a password hint, or allowing a password change, as needed). You can configure forgotten password self-service to run inside the firewall (the default), or you can configure it to run outside the firewall.
-
Provide users with challenge question self-service
-
Provide users with password hint self-service
Required Setup in eDirectory
Before you can use most of the password self-service and user authentication features, you need to do the following in eDirectory:
-
Enable Universal Password
-
Create one or more password policies
-
Assign the appropriate password policies to users
A password policy is a collection of administrator-defined rules that specify the criteria for creating and replacing user passwords. NetIQ Identity Manager takes advantage of NMAS (NetIQ Modular Authentication Service) to enforce password policies that you assign to users in eDirectory.
You can use NetIQ iManager to perform the required setup steps. For example, here’s how someone defined the DocumentationPassword Policy in iManager.
Figure 5-1 Sample Password Policy
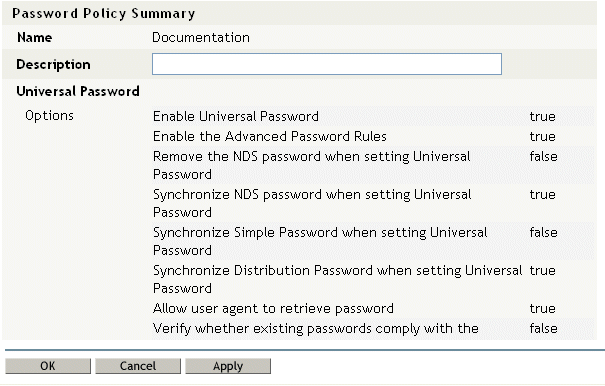
This password policy specifies:
-
Universal Password settings
-
Settings to deal with forgotten-password situations
-
Assignments that apply the policy to specific users
Case-Sensitive Passwords
By default passwords are not case-sensitive. You can create a password policy that allows case-sensitive passwords. You can specify the Allow the password to be case-sensitive in the Password Policies > Universal Password > Advanced Password Rules. If you enable case-sensitive password, you must also enable the Allow user to retrieve password setting. It is enabled by default, but you can verify it through the iManager Password Policies > Universal Password > Configuration Options tab.
Password Policy Compliance
If you enable Universal Password, it is recommended that you also configure the system to verify that existing passwords comply with the password policy. You can configure this through iManager. In iManager, go to Passwords > Password Policies > Universal Password > Configuration Options. Make sure the following option is selected: Verify whether existing passwords comply with password policy (verification occurs on login). This ensures that users created through the User Application are forwarded to the Change Password page to enter a password that complies with the Identity Manager password policy.
5.3.2 Configuring Challenge Response
The Challenge Response self-service page lets users:
-
Set up the valid responses to administrator-defined challenge questions, and set up user-defined challenge questions and responses
-
Change the valid responses to administrator-defined challenge questions, and change user-defined challenge questions and responses
NOTE:The password management facility makes passwords case-sensitive, by default, and also allows you to configure case sensitivity for passwords. This is not the case with the Challenge Response facility. Challenge Response answers are not case sensitive, and cannot be configured to support case sensitivity.
HINT:If you have localized the Challenge Response questions in iManager set the Login Configuration setting Enable Locale Check to True.
Requirements
The Challenge Response requirements are described Table 5-6.
Table 5-6 Challenge Response Requirements
|
Topic |
Requirements |
|---|---|
|
Password policy |
A password policy with forgotten password enabled and a challenge set. |
|
Universal Password |
Does not require Universal Password to be enabled. |
|
eDirectory configuration |
Requires that you grant supervisor rights to the LDAP Administrator for the container in which the logged-in user resides. Granting these privileges allows the user to write a challenge response to the secret store. For example, suppose the LDAP realm administrator is cn=admin, ou=sample, n=netiq and you log in as cn=user1, ou=testou, o=netiq. You need to assign cn=admin, ou=sample, n=netiq as a trustee of testou, and grant supervisor rights on [All attribute rights]. |
Using the Challenge Response Feature
To use the Challenge Response feature, you need to know about the following:
How Challenge Response Is Used During Login
During the login process, the Login page automatically redirects to Challenge Response whenever the user needs to set up challenge questions and responses (for example, the first time a user attempts to log in to the application after an administrator assigns the user to a password policy in iManager. The password policy must have forgotten password enabled and include a challenge set).
How Challenge Response Is Used in the User Application
By default, the User Application provides users with self-service for changing challenge questions and responses.
Configuring Challenge Response
The Challenge Response Configuration settings (on the Administration tab) are described in the following table.
|
Setting |
Description |
|---|---|
|
Mask Response Text |
Choosing Yes means that user-entered response text is masked with asterisk (*) characters. |
5.3.3 Configuring Login
The Login page performs a very robust user authentication supported by Identity Manager (through Universal Password, password policies, and NMAS). The Login page redirects to the other password pages as needed during the login process.
Requirements
The Login page requirements are listed in Table 5-7 below.
Table 5-7 Login Requirements
|
Topic |
Requirements |
|---|---|
|
Password policy |
This page does not require a password policy, unless you want to use advanced password rules or let users click the Forgot Password link. |
|
Universal Password |
This page does not require Universal Password to be enabled, unless you want to use a password policy with advanced password rules. |
|
SSL |
This page uses SSL, so make sure that your application server is properly configured to support SSL connections to your LDAP realm. |
Use the Password Module Setup Login Action to configure the following settings:
Table 5-8 Login Configuration Settings
|
Configuration Setting |
Description |
|---|---|
|
Allow ID Wildcard |
If True, users can specify the first few characters of a username and a list of usernames that include those characters is displayed so the use can select the user to login as. |
|
Enable Forgot Password Link |
If True, the User Application Login page displays the Forgot Password link. |
|
Enable Hint Migration |
If True, any existing hints are moved from the nsimHint to the nsimPasswordReminder. |
|
Enable Locale Check |
If True, and the user has not set their locale preferences, the User Application displays a page that allows them to set their preferred locale. |
|
Enable Password Autocomplete |
If True and supported by the browser, the user’s browser opens a window asking if the user wants to save the login credentials. If False (the default), the user does not receive a browser prompt to save the login credentials. |
|
Guest Container Page |
Allows you to specify a custom guest container page. For example, you might specify any of the following values to direct the user to the MyOrgChart page: /IDMProv/portal/cn/DefaultContainerPage/MyOrgChart /portal/cn/DefaultContainerPage/MyOrgChart http://localhost:9000/IDMProv/portal/cn/DefaultContainerPage/MyOrgChart The default value is: GuestContainerPage |
|
Logout URL |
This value specifies the URL that a user is redirected to after the user presses the Logout button in the User Application. |
|
Password Change Return Page |
This value specifies the URL that a user is redirected to after a password change. If you specify an URL for this setting, the User Application displays a link to the redirect page, along with a success message when the password has been changed. This setting only works when accessing the User Application via NetIQ Access Manager. If you access the User Application without going through Access Manager, the Password Change Return Page link will not display. Furthermore, this setting only works within the context of the User Application and not when you access the ChangePassword.jsp directly. If you access the ChangePassword.jsp directly, you will not see a link displayed that redirects to the Password Change Return Page. Stand-alone access to the ChangePassword.jsp When accessing ChangePassword.jsp directly, if you want users to receive a success message, you need to add the following URL parameter: ?changePasswordForcedLogout=true For example: http://myserver/IDMProv/jsps/pwdmgt/ChangePassword.jsp?changePasswordForcedLogout=true Otherwise, the user will not receive a success message after changing their password. Using NetIQ Access Manager’s Expired Password Servlet If you are using NetIQ Access Manager and want to utilize Password Expiration, then the URL for the Password Expiration Servlet within NetIQ Access Manager will need to be similar to the following: http(s)://%server%:%port%/%context%/jsps/pwdmgt/ChangePassword.jsp?changePasswordForcedLogout=true&idp_return_url=<RETURN_URL>&store=<STOREID>&dn=<USERID>&action=expire For example: http://myserver.netiq.com/IDMProv/jsps/pwdmgt/ChangePassword.jsp?changePasswordForcedLogout=true&idp_return_url=<RETURN_URL>&store=<STOREID>&dn=<USERID>&action=expire |
|
Enable Password Expiration Warning |
This setting gives you the ability to enable or disable the expired password warning. This feature is useful in configurations where another product has detected an expired password and already warned the user prior to redirecting to the Identity Manager portlets. |
|
Using SSL Login |
This setting gives you the ability to configure the Login to redirect to https. If you set Using SSL Login to true, then when user goes to the login.jsp (either directly or through a redirect from NONE SSL page), the login.jsp page will be presented with https with the SSL port configured (Server SSL Port). After user logs in, he see the https (SSL) Home page. |
|
Server SSL Port |
Specifies the SSL port that the User Application is running on. |
Using the Login Page
To use the Login page, you need to know about the following:
How Login Redirects to Other Pages
At runtime, the Login page redirects to other password pages, depending on what’s needed to complete the login process. Table 5-9 directs you to descriptions.
Table 5-9 Login Directions to Other Pages
|
If the user |
Login redirects to |
|---|---|
|
Clicks the link Forgot Password |
Forgot Password page |
|
Needs to set up challenge questions and responses |
Challenge response page |
|
Needs to set up a password hint |
Hint Definition page |
|
Needs to reset an invalid password |
Change password page |
Using Grace Logins
If you use a grace login, the Login page displays a warning message that asks you to change your password and indicates the number of grace logins that remain. If you are on your last login, the Login page redirects you to the Change Password page.
5.3.4 Configuring Password Sync Status
Password Sync Status lets users check the progress of the password change process on connected systems. You can specify a different image to represent each connected system. To set up password sync status checking:
-
Define the connected applications whose status the user should be able to view during the synchronization process. You define the connected applications in the Password Sync Status Application Settings described in Table 5-11.
-
Define the settings for the password sync status page displayed to users. These settings are described in Table 5-10, Password Sync Status Client Settings.
By default, the User Application Administrator can view the password sync status of other users when the User Application Administrator accesses the Password Sync Status page. The administrator can access the sync status for another user by specifying the other user’s DN, then clicking Check Sync Status.
In addition to the User Application Administrator, you can define a set of users to perform the Check Sync Status for other users (for troubleshooting or other purposes). The members of a group called PasswordManagement are also automatically allowed to view the password synchronization status of other users. This group does not exist by default. If you choose to create this group, it must be:
-
Named PasswordManagement.
-
Given privileges to the Identity Vault. The group must have rights to read the user’s eDirectory object attribute for users whose password synchronization status they need to view. The system accesses the DirXML-passwordSyncstatus, the pwdChangedTime, and the DirXML-Associations attributes.
Table 5-10 Password Sync Status Client Settings
|
Configuration Setting |
Description |
|---|---|
|
Password Sync Buffer Time (milliseconds) |
The password sync status checking compares time stamps across different Identity Vaults and connected systems. This buffer time is intended to account for differences between the system times on these different machines. This time is added to the time stamp on the user object’s password change attribute to determine if a change has occurred. It is used like this: The Password Sync Status process uses the buffer time as follows:
|
|
Image Per Row |
The number of application images to display per row in the Identity Self-Service Password Sync Status page. |
|
Individual Application Timeout (milliseconds) |
The amount of time that the Password Sync Status process waits for a response for each connected application’s status before checking for the next one. |
|
All Application Timeout (milliseconds) |
This value indicates the amount of time allowed for the entire password sync status process (of all connected systems) to complete. Before this timeout is reached, the password sync process continues to poll until all status values are updated or this timeout is reached. When the timeout status is reached, the system displays an error message to the user that indicates that a timeout condition has been reached. |
|
Process Count |
The number of times each connected system is checked for the password sync status. |
|
Pass Phrase |
If the DirXML-PasswordSyncStatus contains a password hash, then the value entered in this field is compared to that value. If they are not equal, the User Application displays an invalid hash message. |
|
Application Image Size Limit (bytes) |
Lets you set the maximum size (in bytes) of the application image that can be uploaded. You specify this image in the Application Image setting described in Table 5-11. |
|
Show Password Sync Status After Password Change |
If this field is set to true, after the user changes a password, the interface presents the Password Sync Status screen. If this field is set to false, the Password Sync Status screen is not displayed after a password change. |
The password Sync Status Application Settings are described in Table 5-11.
Table 5-11 Password Sync Status Application Settings
|
Configuration Setting |
Description |
|---|---|
|
Password Synchronization Application Name |
The name used to describe the connected application. You can enter the application name in multiple locales. To add a language (locale):
If you do not specify localized application names, the value specified in the Password Synchronization Application Name is used. |
|
Application DirXML-PasswordSyncStatus GUID |
You can get the driver GUID by browsing the attributes on the driver object in one of two ways:
|
|
Application Image |
The name of the connected application Image to upload. The Application Image size can be configured from the Application Image Size Limit field in the Password Sync Status Client Settings section. Supported file types are .bmp, .jpeg, .jpg, .gif, and .png. |
|
Application Filter |
Optional. Specify an LDAP filter that allows or prohibits users’ viewing the application name on their Check Password Synchronization pages. You can use any standard LDAP filter. |
|
Dependent Driver |
Optional. Specify any additional driver this application depends on. If any driver in the dependent driver chain is not visible to the user, the driver specified by Application DirXML-PasswordSyncStatus GUID is also not visible to the user. If any driver in the dependent driver chain fails to check password sync status, the driver specified by Application DirXML-PasswordSyncStatus GUID also fails to check password sync status. You can get the driver GUID by browsing the attributes on the driver object in one of two ways:
|
5.3.5 Configuring Password Hint Change
This self-service page lets users set up or change their password hints, which can be displayed or e-mailed as a clue in forgotten password situations.
Requirements
The Password Hint Change requirements are listed in Table 5-12.
Table 5-12 Password Hint Change Requirements
|
Topic |
Requirements |
|---|---|
|
Universal Password |
Does not require Universal Password to be enabled. |
Using the Password Hint Change Page
To use the Password Hint Change page, you need to know about the following:
How Password Hint Change Is Used During Login
During the login process, the Login page automatically redirects to the Password Hint Change page whenever users need to set up their password hints. For example, the first time a user attempts to log in to the application after an administrator assigns the user to a password policy in iManager, the password policy has forgotten password enabled and has the action set to Email hint to user or Show hint on page.
Using Password Hint Change in the User Application
By default, the User Application provides users with self-service for changing a password hint.
5.3.6 Configuring Change Password
This self-service page lets users change (reset) their Universal Passwords, according to the assigned password policy. It uses that policy to display the rules that the new password must conform to.
If Universal Password is not enabled, this page changes the user’s eDirectory (simple) password, as permitted in the user's Password Restrictions.
There are no Password Change configuration settings.
Requirements
The Change Password page requirements are listed in Table 5-13.
Table 5-13 Change Password Requirements
|
Topic |
Requirements |
|---|---|
|
Directory Abstraction Layer configuration |
No directory abstraction layer configuration is required for this page. |
|
Password policy |
This page does not require a password policy, unless you want to use advanced password rules (with Universal Password enabled). |
|
Universal Password |
To use this page for a Universal Password, the setting Allow user to initiate password change must be enabled in the Advanced Password Rules of the user's assigned password policy. To use this page for an eDirectory (simple) password, the setting Allow user to change password must be enabled in the user’s Password Restrictions. |
Using the Change Password Page
To use the Change Password page, you need to know about the following:
How Change Password Is Used During Login
During the login process, the Login page automatically redirects to the Change Password page whenever the user needs to reset an invalid password. For example, the first time a user attempts to log in to an application after an administrator implements a password policy that requires users to reset their passwords.
The Forgot Password page also redirects to Change Password automatically if the user’s assigned password policy specifies reset password as the action for forgotten password situations.
Using Change Password in the User Application
By default, the User Application provides users with the password change self-service using the Change Password page.
NOTE:On Firefox, if you allow the browser to save passwords, you may see a confusing pop-up message that asks the following question when you confirm a password change: Would you like to have password manager change the stored password for <user>?
. The user specified in the message may not be the same as the user who logged into the User Application. This message is generated by the Firefox password manager. To turn off this message, you need to disable the password manager in Firefox by deselecting the Remember passwords sites checkbox under Passwords on the Tools>Options>Security page.