19.1 Overview
Identity Manager uses a resource model for event-based reconciliation of external system permission assignments. This resource model was introduced in Identity Manager 4.0 to simplify the entitlement model and provide you a convenient way to perform resource-based provisioning actions. The resource-based provisioning actions allow you to manage resource definitions and resource assignments within your organization.
You can map resource assignments to users or to roles within your organization. For example, you can use resources to:
-
Make resource requests for yourself or other users within your organization
-
Create resources and map them to entitlements
A resource is any digital entity such as a user account, computer, or database that a business user needs to be able to access. Identity Manager provides a way to manage permissions assignments in connected systems. You can think of an entitlement as a permission slip. A resource definition can have no more than one entitlement bound to it. You can bind a resource to the same entitlement more than once, with different entitlement values for each resource. For more information about entitlements in Identity Manager, see the Identity Manager 4.0.2 Entitlements Guide.
You can assign resources to users only. You cannot assign them to groups or containers. If the resource is mapped to a role then the role can be assigned to a group or container resulting in assignment of mapped resource to all the users in that group or container.
Before you can assign resources to users, these resources must be defined in the Identity Manager Resource Catalog. The Resource Catalog is a storage repository of all resources definitions and supporting data needed by the Role and Resource Subsystem. The tab of the Identity Manager user application allows you to view resources that have been previously defined in the Resource Catalog. It also lets you create new resources and modify, delete, and assign existing resources.
This model works well when the source of assignment changes or permission changes is Identity Manager and you need to update connected systems with these changes. However, you need additional functionality to synchronize the permission assignment changes from connected systems to Identity Manager.
For example, if a connected system administrator provides additional permissions to existing users or creates new users, the Identity Manager driver publishes these changes to the Identity Vault. With the default content shipped with the Identity Manager driver, the changes in the permission assignments are not directly updated to the User Application Resource Catalog. You need to customize the package content so that Resource Catalog reflects the current state of connected system.
Identity Manager now provides an out-of-box solution to update the resource when permission assignments are published to the Identity Vault as they occur in connected systems. It provides a way to dynamically create an entitlement and a dynamic resource for each permission and load entitlement values into the resource catalog of Identity Manager Roles Based Provisioning Module.
An Identity Manager driver installed with this package content can update the Resource Catalog with connected system changes. The driver can automatically assign or revoke resources to Identity Manager identities based on attribute values changed in connected system. For a newly installed driver with this package content, you can migrate users and groups (for example, Active Directory) into the Identity Vault, which updates the Resource Catalog with the current state of connected system.
You can dynamically create resources with custom entitlement populated with permission values of connected system, and permission assignments between Identity Manager resource/entitlement model and connected systems. Figure 19-1 depicts the flow of permissions from a connected system to the Resource Catalog and then into the Identity Vault.
Figure 19-1 Flow of New Users and Permission Assignments
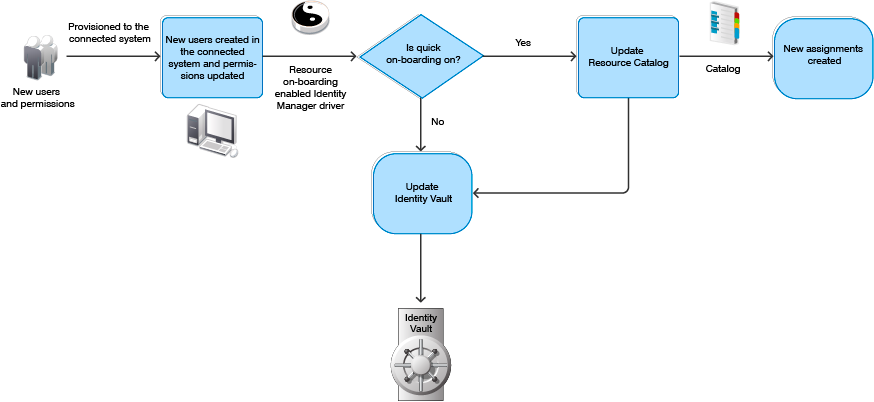
You can use Designer to create custom entitlements on any driver enabled with this functionality to reflect the current state of connected systems. Figure 19-2 illustrates how the driver updates the Resource Catalog with custom permission assignments in entitlement changes.
Figure 19-2 Custom Entitlements Creation
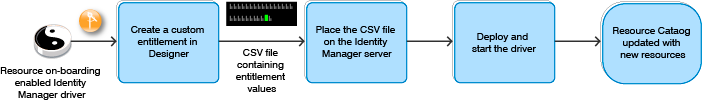
You must place the CSV file containing the entitlement values on the server where Identity Manager engine is installed. After you create, deploy, and start the driver, the driver automatically creates a new resource in the Resource Catalog with the entitlement values from the CSV file. When the permission assignments change in connected system, the driver policies consume the modified permission values and update the Resource Catalog.
IMPORTANT:You can create a new resource and map it to a custom entitlement and reconcile permission assignments. However, if Permission Collection and Reconciliation service is turned off, all resource assignments for the custom entitlement are disabled regardless of whether the resource is created through this service or not. The common package supplied with the Permission Collection and Reconciliation service is not supported on a driver that already supports entitlements.
The Identity Manager drivers installed with these packages perform the following actions:
-
Provide a way to create custom entitlements and resources specific to your environment.
-
Reconcile resource or permission assignments between the Identity Vault and connected systems.
19.1.1 Prerequisites
The following requirements are common for all drivers:
-
Designer for Identity Manager 4.0.2 AU4 and later
-
Identity Manager 4.0.2 with Engine Patch 4 and later
-
Managed System Gateway driver version 4.0.0.6 and later
-
Driver Set Package:
-
Common Settings Advanced Edition Package (NOVLACOMSET 2.0.0 and later)
-
-
Driver Package:
-
Permission Collection and Reconciliation service package (NOVLCOMPCRS 2.0.0 and later)
This package contains the content for Permission Collection and Reconciliation service.
-
19.1.2 CSV File Format
An Identity Manager driver can consume the entitlement information from the CSV file, which is present on the server where Identity Manager is installed. This file must contain values of the target system permissions in the format specified below. The target system administrator should maintain a separate CSV file for every custom entitlement. For example, a CSV file can contain details about granting access to the employees for the entitlement. A CSV file that contains entitlement details represents this information in the following format:
Building A Engineering The engineering building Building B Accounting The accounting building Building C Facilities The facilities building Building D Warehouse The warehouse
where is the entitlement value, is the display name in the User Application for the entitlement value , and is the description for the entitlement value displayed in the User Application.