8.1 Using the Manage Schema Tool
To open the Manage Schema tool, right-click an Identity Vault object in the Modeler or Outline View, then select Manage Vault Schema.
If a custom schema in the production environment needs to be tested, you can import the schema into Designer. After you have tested and modified the schema, you can deploy it into the production environment. For information about importing schema, see Section 8.6, Importing the Schema.
The Manage Schema tool lets you add, delete, rename, and modify classes and attributes in the Identity Vault schema. The class information and the attribute information is organized into separate tabs in the Manage Schema tool.
8.1.1 The Classes Tab
From the Classes tab, the Manage Schema tool lets you add, delete, rename, and modify schema classes.
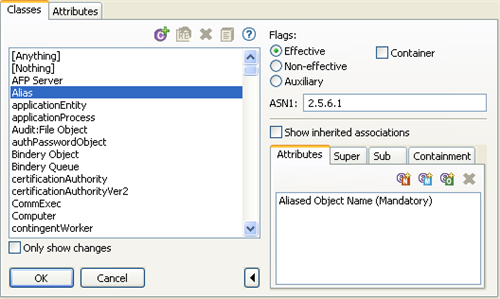
The Classes tab includes the following components:
Class List Toolbar
The Classes list includes the following tools:
Table 8-1 Classes List Toolbar
|
Icon |
Description |
|---|---|
|
Add Class |
Launches the New Class Wizard to create a new Identity Vault class. |
|
Rename Class |
Renames any non-base class. You cannot rename base classes. |
|
Delete Class |
Deletes any non-base class. You cannot delete base classes. |
|
Schema Notes |
Adds descriptive notes to any non-base class.You cannot add notes to base classes. |
Only Show Changes
The Only show changes check box is below the Classes list. When it is selected, the Classes list displays only those classes that are not part of the base schema, as defined in BaseIVSchema.xml. If no non-base classes exist, the Classes list is empty.
Deselect Only show changes to see a complete list of base and non-base classes in the Identity Vault schema.
ASN1
Specifies the class’s Abstract Syntax Notation number One ID. The ASN1 ID is important as you plan to make the schema definition publicly available.
If you register your schema definition with Novell, Novell assigns your class an ASN1 ID. This unique identifier eliminates the possibility of schema collisions caused by duplicate schema names with different definition structures.
For more information about ASN1, visit the International Telecommunications Union Web site.
Flags
The Flags options let you modify the class type:
Table 8-2 Supported Class Types
|
Flag |
Description |
|---|---|
|
Effective |
You can create an instance of the defined object in the Identity Vault. |
|
Noneffective |
Only used to define other classes. You cannot create an object of a noneffective class. |
|
Auxiliary |
Combines attributes to be added to other classes by extending the object class attribute. |
|
Container |
Sets the object to be a container object instead of a leaf object. If it is set to be a container, this object can contain other objects. |
Show Inherited Associations
The Show Inherited Associations check box determines whether the Associations list displays all attributes associated with a class. When the check box is selected (the default), the Associations list displays both assigned and inherited attributes. When the check box is deselected, the Associations list displays only assigned attributes.
NOTE:When you select Show Inherited Associations, you cannot delete entries from the Associations list.
Associations List
The Associations list displays the classes and attributes associated with the selected class. The Associations list includes four tabs, each with a toolbar.
Attributes: The Attributes tab displays the attributes associated with the selected class. It also identifies if attributes are mandatory or naming. All unmarked attributes are optional.
The Attributes tab includes the following tools:
|
Class Field |
Description |
|---|---|
|
Add Naming |
Adds a naming attribute association to the selected class. |
|
Add Mandatory |
Adds a mandatory attribute association to the selected class. |
|
Add Optional |
Adds an optional attribute association to the selected class. |
|
Delete |
Deletes an attribute association from the select class. |
Super: The Super tab displays the classes from which the selected class inherits attributes. A class that another class inherits from is called a superclass.
A class can inherit attributes from more than one superclass. The superclass that every class inherits from is Top. No class exists above Top. For example, Group inherits directly from Top, but User inherits from Organizational Person. Organizational Person inherits from Person. Person inherits from ndsLoginProperties, and ndsLoginProperties inherits from Top.
The Super tab includes the following tools:
|
Class Field |
Description |
|---|---|
|
Add Superclass Association |
Adds a superclass association to the selected class. |
|
Delete |
Deletes a superclass association from the selected class. |
Sub: The Sub tab displays all classes that inherit from the selected class. If the Sub tab is empty, no classes inherit from the selected class.
The Sub tab includes the following tools:
|
Class Field |
Description |
|---|---|
|
Add Subclass Association |
Adds a subclass association to the selected class. |
|
Delete |
Deletes a subclass association from the selected class. |
Containment: The Containment tab displays the container classes that can contain the selected class. For example, if you select the Group class, the Manage Schema tool lists the domain, Organization, and Organizational Unit classes, which can contain the Group class.
The Containment tab includes the following tools:
|
Class Field |
Description |
|---|---|
|
Add Containment Class Association |
Adds a containment class association to the selected class. |
|
Delete |
Deletes a containment class association from the selected class. |
8.1.2 The Attributes Tab
From the Attributes tab, the Manage Schema tool lets you add, delete, rename, and modify attributes associated with schema classes.
Figure 8-1 The Attributes Tab on the Manage Schema Toll
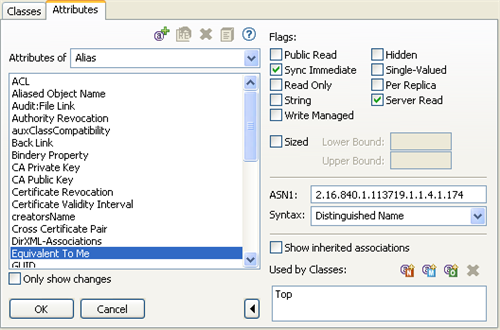
The Attributes tab includes the following components:
Attributes List Toolbar
The Attributes list includes the following tools:
|
Icon |
Description |
|---|---|
|
Add Attribute |
Launches the New Class Wizard to create a new attribute. |
|
Rename Attribute |
Renames the selected non-base attribute. You cannot rename base attributes. |
|
Delete Class |
Deletes the selected non-base attribute. You cannot delete base attributes. |
|
Schema Notes |
Adds descriptive notes to any non-base attribute.You cannot add notes to base classes. |
Only Show Changes
The Only show changes check box is below the Attributes list. When this check box is selected, the Attributes list displays only those attributes that are not part of the base schema, as defined in BaseIVSchema.xml. If no non-base attributes exist, the Attributes list is empty.
Deselect Only show changes to see a complete list of base and non-base attributes in the Identity Vault schema.
Flags
Attribute flags specify the information that is stored in the attribute and limit the list of acceptable operations that the Identity Vault and eDirectory clients can perform on the attribute.
|
Constraint |
Description |
|---|---|
|
Public Read |
Allows anyone to read this attribute without the read privilege specifically assigned. You can’t use inheritance masks to prevent an object from reading attributes with this constraint. |
|
Sync Immediate |
When the attribute is modified, it is synchronized immediately to all of the servers in the replica ring. |
|
Read Only |
Only the eDirectory server process can read this attribute. |
|
String |
Allows only string information to be stored in the attribute. |
|
Write Managed |
Explicit rights are granted before this attribute can be changed. In order to modify this attribute, users must have managed rights on the object to change the attribute. |
|
Hidden |
Only the eDirectory server process can read this attribute. |
|
Single Valued |
Allows one value to be stored in the attribute. |
|
Per Replica |
Allows one value to be stored in the attribute. |
|
Server Read |
The attribute can be read by an NCP server object even though the right to read is not inherited or explicitly granted. The NCP server object is always able to read this attribute, regardless of the rights granted in the ACL. |
|
Sized |
Limits the range of values supported by the attribute to some subset of those supported by the attributes data type. For example, you might restrict an Integer attribute to only accept values between 1 and 100. |
ASN1
Specifies the attribute’s Abstract Syntax Notation number One ID. The ASN1 ID is important is you plan to make the schema definition publicly available.
If you register your schema definition with Novell, Novell assigns your attribute an ASN1 ID. This unique identifier eliminates the possibility of schema collisions caused by duplicate schema names with different definition structures.
For more information about ASN1, visit the International Telecommunications Union Web site.
Syntax
An attribute syntax defines a standard data type that an attribute uses to store its values in the Identity Vault. Each attribute must have a syntax. The following table describes the available syntaxes for Identity Vault attributes.
|
Syntax |
Description |
|---|---|
|
Back Link |
The remoteID field identifies the backlinked object on the server, and the objectName field identifies the server holding an external reference. |
|
Boolean |
Two Boolean attributes match for equality if they are both True or both False. True is represented as one (1), and False is represented as zero (0). Any attribute defined by using this syntax is single valued. |
|
Case Exact String |
Attributes using this syntax can set size limits. Two Case Exact Strings match for equality when they are of the same length and their corresponding characters are identical. |
|
Case Ignore List |
Two Case Ignore Lists match for equality if the number of strings in each is the same, and all corresponding strings match. For two corresponding strings in the list to match, they must be the same length and their corresponding characters must be identical (according to the rules for case ignore strings). |
|
Case Ignore String |
Used in attributes whose values are strings and where the case (upper or lower) is ignored. |
|
Class Name |
Used to match two class names where the case (upper or lower) is ignored. |
|
Counter |
The attribute is single valued. The syntax is similar to Integer, except that any value added to an attribute is arithmetically added to the total, and any value deleted is arithmetically subtracted from the total. |
|
Distinguished Name |
The attribute is the distinguished name of the object up to 256 Unicode characters. This is not case sensitive. |
|
EMail Address |
Used to match attributes whose values are e-mail addresses and whose lengths and corresponding characters are identical; however, it ignores case (upper and lower). Only the EMail Address attribute uses this syntax. |
|
Facsimile Telephone Number |
Facsimile Telephone Number values are matched based on the telephone number field. The rules for matching fax telephone numbers are identical to those for the Case Exact syntax except that all space and hyphen (-) characters are skipped during the comparison. Only the Facsimile Telephone Number attribute uses this syntax. |
|
Hold |
This syntax is an accounting quantity, which is an amount tentatively held against a subject’s credit limit, pending completion of a transaction. In the wire format, the Subject field is the distinguished name of the object. The Identity Vault treats the Hold amount similarly to the Counter syntax, with new values added to or subtracted from the base total. If the evaluated Hold amount goes to 0 (zero), the Hold record is deleted. |
|
Integer |
The attribute is an integer. Attributes using this syntax can set size limits. |
|
Interval |
The Interval value is the number of seconds in a time interval. |
|
Net Address |
Stores the network address as a binary string. The string is the literal value of the address. It lists the type of communication protocol used. |
|
Numeric String |
Two numeric strings match for equality when they are of the same length and their corresponding characters are identical. It matches the digits 0-9 and spaces if they are contained in the numeric string. |
|
Object ACL |
An Object ACL value can protect either an object or an attribute. The protected object is always the one that contains the ACL attribute. If an ACL entry is to apply to the object as a whole, the protected attribute name should be left empty (NULL). If a specific attribute is to be protected, it should be named in the ACL entry. |
|
Octet List |
A presented octet list matches a stored list if the presented list is a subset of the stored list. Octet strings are so designated because they are not interpreted by the Directory. They are simply a series of bits with no Unicode implications. The length is the number of bits divided by 8 and rounded to the nearest integer. Thus, each octet represents eight bits of data. The number of data bits is always evenly divisible by 8. |
|
Octet String |
For two octet strings to match, they must be the same length and the corresponding bit sequence (octets) must be identical. When comparing two strings, the first pair of octets that do not match are used to determine the order of the strings. Octet strings are not Unicode strings. |
|
Path |
The string represented by the path field is compared for equality by using the same rules that Case Exact String uses. That is, two paths match for equality when their lengths and corresponding characters, including case, are identical. |
|
Postal Address |
An attribute value for Postal Address is typically composed of selected attributes from the MHS Unformatted Postal O/R Address version 1 according to Recommendation F.401. The value is limited to 6 lines of 30 characters each, including a Postal Country Name. Normally the information contained in such an address could include a name, street address, city, state or province, postal code, and possibly a postal office box number depending on the specific requirements of the named object. |
|
Printable String |
The following characters are in the printable string character set. A...Z a...z 0...9 Space Character ‘ Apostrophe ( Left Parenthesis ) Right Parenthesis + Plus Sign Modeler, Comma - Hyphen . Period / Slash : Colon = Equal Sign ? Question Mark Two printable strings match for equality when they are the same length and their corresponding characters are identical. Case (upper or lower) is significant when comparing printable strings. For example, as printable strings, “Jones” and “JONES” do not match. |
|
Replica Pointer |
Each value of the replica pointer syntax is composed of five parts:
|
|
Stream |
Streams are files of information. The data stored in a stream file has no syntax enforcement of any kind. It is purely arbitrary data, defined by the application that created and uses it. The attribute is single valued. |
|
Telephone Number |
The length of telephone number strings must be between 1 and 32. Two telephone numbers string match for equality when they are of the same length and their corresponding characters are identical. All spaces and hyphen (-) characters are skipped during the comparison. |
|
Time |
A time value consists of a whole number of seconds, where zero equals 12:00 midnight, January 1, 1970, UTC. |
|
Timestamp |
A Timestamp value contains three components:
|
|
Typed Name |
The syntax names an Identity Vault object and attaches two numeric values to it:
The objectName or Distinguished Name identifies the Identity Vault object referred to by the Typed Name. |
|
Unknown |
Unknown syntax is used to stop the loss of data, if the Identity Vault database becomes corrupted. When an object becomes Unknown, there is information stored in this attribute that can allow the object to be recovered. This syntax is used by the Identity Vault. |
NOTE:The information in this table comes from the Novell LogicSource for eDirectory. LogicSource is a subscription-based service Novell provides to its customers. For more information about LogicSource, see Novell Technical Subscriptions.
Show Inherited Associations
The Show Inherited Associations check box determines whether the Associations list displays all classes associated with an attribute. When this check box is selected (the default), the Associations list displays both assigned and inherited classes. When this check box is deselected, the Associations list displays only assigned classes.
The schema allows for inheritance of other attributes from superclasses. If you select this item, all attributes that are associated with a class, whether assigned or inherited, are listed. If you don’t select this item, only the assigned attributes are listed.
Used by Classes lists all classes that use the selected attribute. If you select Show inherited associations, the list includes classes that inherit the attribute.
Associations List
The Associations list displays the classes associated with the selected attribute. The Associations list toolbar lets you make changes to the classes associated with the attribute.
|
Class Field |
Description |
|---|---|
|
Add as Naming |
Associates the selected attribute as a naming attribute to a class. |
|
Add as Mandatory |
Associates the selected attribute as a mandatory attribute to a class. |
|
Add Optional |
Associates the selected attribute as an optional attribute to a class. |
|
Delete |
Deletes the selected classes from the association list. |







