2.1 Discovery Phase
The Identity Manager solution affects many aspects of your business. In order to create an effective solution, you must take time to define all of your current business processes, then identify how an implementation of Identity Manager changes these processes, who these changes affect, and how the changes are implemented.
The discovery phase provides a common understanding of the issues and solutions for all stakeholders. It creates a plan or road map that contains the key business and systems information that are affected by the Identity Manager solution. It also allows all stakeholders to participate in the creation of the Identity Manager solution so they understand how it can affect their area of the business.
The following list indicates the steps needed to have a successful discovery phase. There might be additional items you find that you need to add to the list as you proceed through the discovery and design phases.
2.1.1 Defining Current Business Processes
Identity Manager automates business processes to easily manage identities in your environment. If you do not know what the current business processes are, you cannot design an Identity Manager solution that automates those processes. You can use the Architecture mode of Designer to capture your current business processes and display them graphically. For more information, see Architect Mode
in the Designer 4.0.1 for Identity Manager 4.0.1 Administration Guide.
For example, you company might identify the following business processes:
-
When an employee is terminated, the user account in the e-mail system is deleted, but the user’s account in all other systems is disabled, not deleted.
-
The format for a user’s e-mail address.
-
The systems or resources that sales employees can access.
-
The systems or resources that managers can access.
-
What systems generate new accounts? Is it the human resource system or is it through a workflow request?
-
A password policy for the company that defines how often a password changes, how complex the password is, and which systems are synchronizing the password.
As you define your business processes, use the following list of items to help you understand all of the processes:
-
Define or clarify the current business issues.
-
Determine what initiatives are required to address these issues.
-
Determine which services and systems are affected by these initiatives.
This step allows you to create a high-level overview of what your business is currently doing and what processes need to be improved. For example, Figure 2-1 uses Designer to show how new user accounts are generated from the PeopleSoft system. They are synchronized into the Identity Vault and then synchronized into Lotus Notes and Active Directory. Passwords are being synchronized between Active Directory and the Identity Vault. Accounts are synchronizing into the Notes system, but no accounts are synchronizing back to the Identity Vault.
Figure 2-1 Example of Business Processes
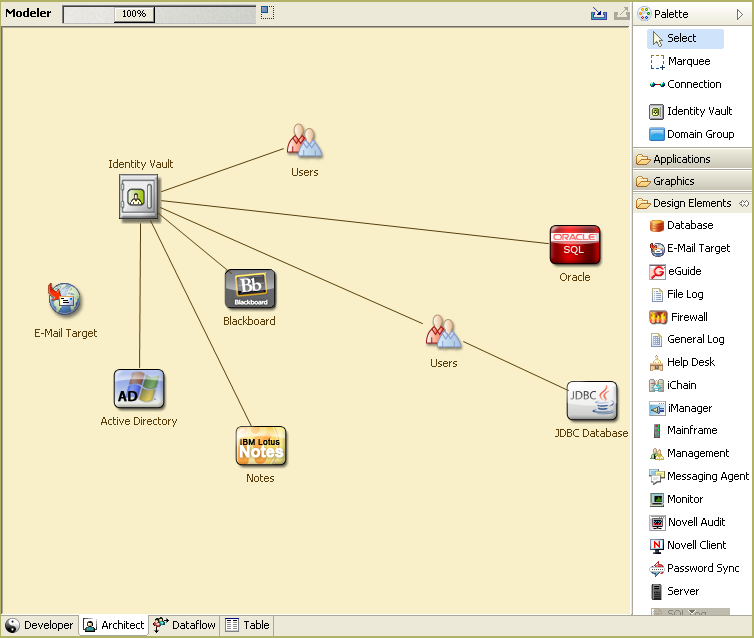
After you determine processes, you start to identify how Identity Manager can be involved. Continue with Section 2.1.2, Defining How the Identity Manager Solution Affects the Current Business Processes.
2.1.2 Defining How the Identity Manager Solution Affects the Current Business Processes
After you have defined your current business processes, you need to decide which processes you want to incorporate into an Identity Manager solution.
It is best to look at the entire solution and then prioritize which processes should be implemented. Identity Manager encompasses so many aspects of your business, it is easier to plan the entire solution rather than approach each business process as its own solution.
Create a list of which business processes are a priority to automate, then identify which systems these changes will affect. Then continue with Section 2.1.3, Identifying the Key Business and Technical Stakeholders.
2.1.3 Identifying the Key Business and Technical Stakeholders
Identifying all stakeholders involved in the Identity Manager solution is important for the success of the solution. In most companies, there is not just one person you can contact who understands all business and technical aspects of the business processes. You must identify which services and systems are going to be affected by the Identity Manager solution, and you must also identify the person who is responsible for that service or system.
For example, if you are integrating an e-mail system into your solution, you would need to list what the e-mail system is, who the e-mail system administrator is, and what the contact information is. You can add all of this information into the Designer project. Each application icon has a place where you can store information about the system and the system administrator. For more information, see Configuring Application Properties
in the Designer 4.0.1 for Identity Manager 4.0.1 Administration Guide.
After you have identified all of the people involved in each business process, the next step is in Section 2.1.4, Interviewing All Stakeholders.
2.1.4 Interviewing All Stakeholders
Interviews with key business and technical stakeholders allow you to gather information needed for a complete design of the Identity Manager solution. The interviews also allow you to educate each stakeholder about the Identity Manager solution and how the solution affects them. Here is a list of items to cover when you do the interviews:
-
Define or clarify the business processes being addressed by the Identity Manager solution. The person you are interviewing might have information that can change the current plan.
-
Determine how the solution will impact the stakeholders and address any concerns they have. Also ask the stakeholders how much time their part of the solution might take. They might or might not have an estimate, but gathering this information helps to determine the scope of the solution.
-
Capture key business and systems information from the stakeholders. Sometimes a proposed plan might adversely affect a business process or a system. By capturing this information, you can make educated decisions about the Identity Manager solution.
After you have interviewed the key stakeholders, the next step is in Section 2.1.5, Creating a High-level Strategy and an Agreed Execution Path.
2.1.5 Creating a High-level Strategy and an Agreed Execution Path
After all of the information is gathered, you need to create a high-level strategy or road map for the Identity Manager solution. Add all of the features you want to be included in the Identity Manager solution. For example, new user accounts are generated from a request through a workflow, but the type of user depends upon the resources the user is given access to.
Present this high-level strategy to all of the stakeholders in the same meeting, if possible. This allows you to accomplish several things:
-
Verify that the included initiatives are the most correct and identify which ones have the highest priority.
-
Identify planning activities in preparation for a requirements and design phase
-
Determine what it would take to carry out one or more of these initiatives.
-
Create an agreed execution path for the Identity Manager solution.
-
Define additional education for stakeholders.
Discovery provides a common understanding of the issues and solutions for all stakeholders. It provides an excellent primer for the analysis phase, which is a phase that requires stakeholders to have a basic knowledge of directories, Novell eDirectory, Novell Identity Manager, and XML integration in general.
After you have completed the discovery phase, proceed to Section 2.2, Requirements and Design Analysis Phase.