A.5 Scenario 5: Synchronizing Application Passwords to the Simple Password
This scenario is a specialized use of password synchronization features. Using Identity Manager and NMAS, you can take a password from a connected system and synchronize it directly to the Identity Vault Simple Password. If the connected system provides only hashed passwords, you can synchronize them to the Simple Password without reversing the hash. Then, other applications can authenticate to the Identity Vault by using the same clear text or hashed password through LDAP or the Novell Client, with NMAS components configured to use the Simple Password as the login method.
Figure A-10 Synchronizing to the NDS Password
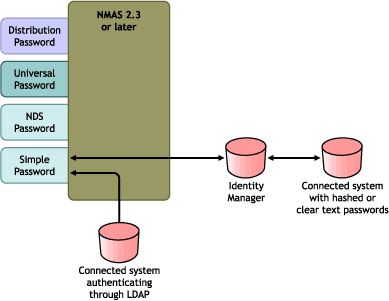
If the password in the connected system is in clear text, it can be published as it is from the connected system into the Identity Vault Simple Password store.
If the connected system provides only hashed passwords (MD5, SHA, SHA1,or UNIX Crypt are supported), you must publish them to the Simple Password with an indication of the kind of hash, such as {MD5}.
For another application to authenticate with the same password, you need to customize the other application to take the user's password and authenticate to the Simple Password using LDAP.
NMAS compares the password value from the application with the value in the Simple Password. If the password stored in the Simple Password is a hash value, NMAS first uses the password value from the application to create the correct type of hash value, before comparing. If the password from the application and the Simple Password are the same, NMAS authenticates the user.
In this scenario, Universal Password cannot be used.
The following sections provide information and instructions for this scenario:
A.5.1 Advantages and Disadvantages of Scenario 5
Table A-5 Synchronizing to the NDS Password
A.5.2 Setting Up Scenario 5
Use the information in the following sections to help complete the tasks in the Password Management Checklist.
Password Policy Configuration
No password policy is required for users for this scenario. Universal Password cannot be used.
Password Synchronization Settings
For this scenario, you use Identity Manager Script to directly modify the SAS:Login Configuration attribute. This means that the Password Synchronization global configuration values (GCVs), which are set by using the Password Synchronization page in iManager, have no effect.
Driver Configuration
-
Make sure that the SAS:Login Configuration attribute in the filter has the setting of for both Publisher and Subscriber channels.
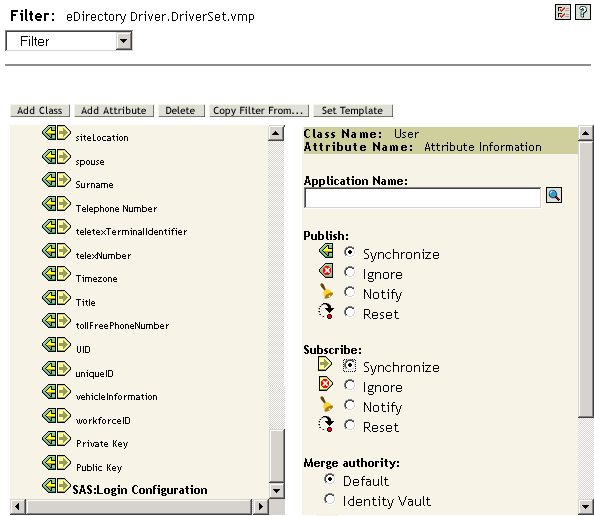
-
Configure the driver policies to publish the password from the connected system.
-
For hashed passwords, configure the driver policies to prepend the type of hash (if it is not already provided by the application):
-
{MD5}hashed_password
This password is Base64 encoded.
-
{SHA}hashed_password
This password is Base64 encoded.
-
{CRYPT}hashed_password
Clear text passwords and UNIX Crypt password hashes are not Base64 encoded.
-
-
To place the password into the Simple Password, configure the driver policies to modify the SAS:Login Configuration attribute.
The following example illustrates how to use a modify-attr element within a modify operation to change the Simple Password to an MD5 hashed password:
<modify-attr attr-name="SAS:Login Configuration> <add-value> <value>{MD5}2tEgXrIHtAnGHOzH3ENslg==</value> </add-value> </modify-attr>For clear text passwords, follow this example.
<modify-attr attr-name="SAS:Login Configuration> <add-value> <value>clearpwd</value> </add-value> </modify-attr>For add operations, the add-attr element would contain one of the following:
<add-attr attr-name="SAS:Login Configuration> <value>{MD5}2tEgXrIHtAnGHOzH3ENslg==</value> </add-attr>or
<add-attr attr-name="SAS:Login Configuration> <value>clearpwd</value> </add-attr>