3.1 Creating the Driver Object in Designer
The Designer tool helps you to create the REST driver object. You need to install the driver packages and then modify the configuration to suit your environment. After you create and configure the driver, you need to deploy it to the Identity Vault and start it.
NOTE:NetIQ recommends that you use the new package management features provided in Designer to create the REST driver. You should not create the driver objects by using the new Identity Manager 4.0 and later or configuration files through iManager. This method of creating driver objects is no longer supported.
3.1.1 Importing the Current Driver Packages
The driver packages contain the items required to create a driver, such as policies, entitlements, filters, and Schema Mapping policies. These packages are only available in Designer and can be updated after they are initially installed. You must have the most current version of the packages in the Package Catalog before you can create a new driver object.
To verify that you have the most recent version of the driver packages in the Package Catalog:
-
Open Designer.
-
In the toolbar, click Help > Check for Package Updates.
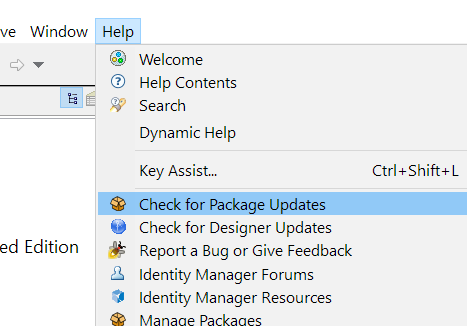
-
Click OK to update the packages
or
Click OK if the packages are up-to-date.
-
In the Outline view, right-click the Package Catalog.
-
Click Import Package.
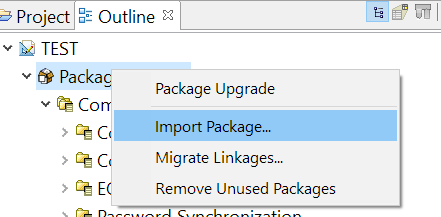
-
Select any REST driver package
or
Click Select All to import all of the packages displayed.
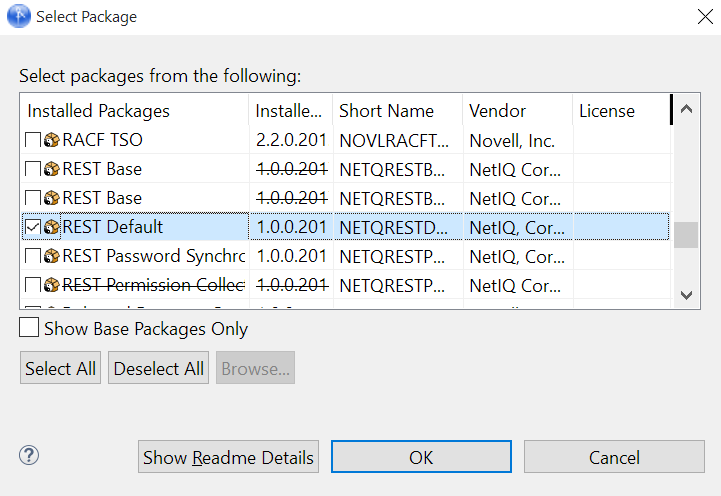
By default, only the base packages are displayed. Deselect Show Base Packages Only to display all packages.
-
Click OK to import the selected packages, then click OK in the successfully imported packages message.
-
After the current packages are imported, continue with Installing the Driver Packages.
3.1.2 Installing the Driver Packages
After you have imported the current driver packages into the Package Catalog, you can install the driver packages to create a new driver, or update the existing driver package. To install driver packages, you have to set-up Identity Vault and the driver set.
Setting up Identity Vault
-
In Designer > Outline view, open your project.
-
Right click project > New > Identity Vault, or drag and drop Identity Vault from the Palette to Modeler window.
The Add Server Association screen appears.
-
In the Add Server Association screen, select the following field values and click OK.
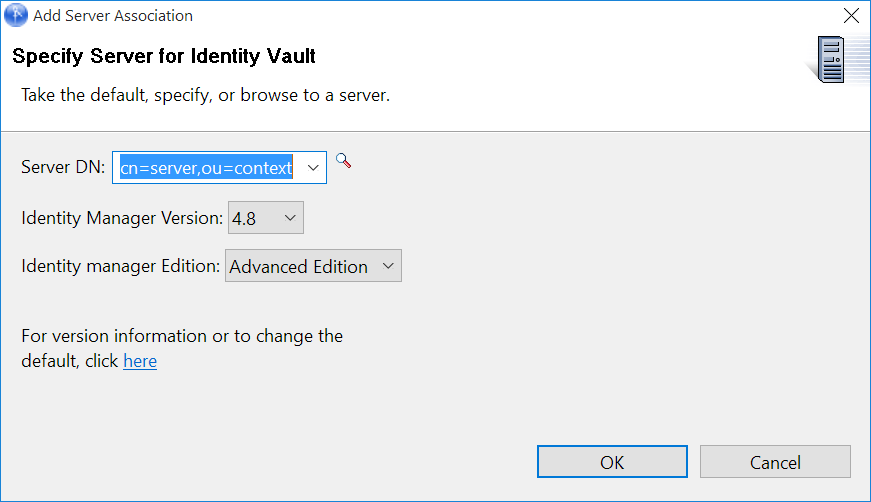
-
Server DN
-
Identity Manager Version
-
Identity Manager Edition
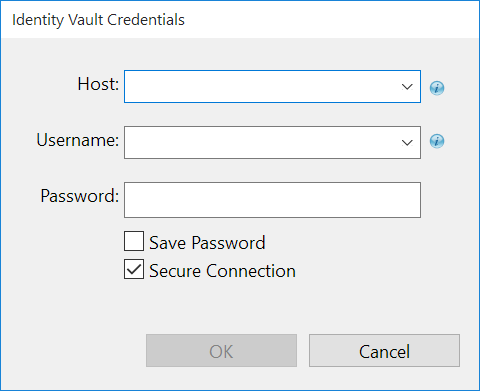
The Identity Vault Credentials window appears.
-
-
In Identity Vault Credentials window, enter values as shown in the following table.
Field
Description
Host
The identity vault hosting machine's IP address.
Username
The name of the user, for example, Admin, if the user is an administrator.
Password
Password of user to login to the identity vault.
-
Select Save Password, if you want to save your password for easy logins in the future.
-
Click OK.
The Identity Vault and the Driver Set appears in the Modeler window as shown in the following image.
-
In the right pane, drag and drop the REST Server from the Tools tab to the Modeler.
-
In the Driver Configuration Wizard, select REST Base (Contains the base functionality for a driver. You must install a driver base configuration package first).
NOTE:You can only select one base package.
-
Click Next.
-
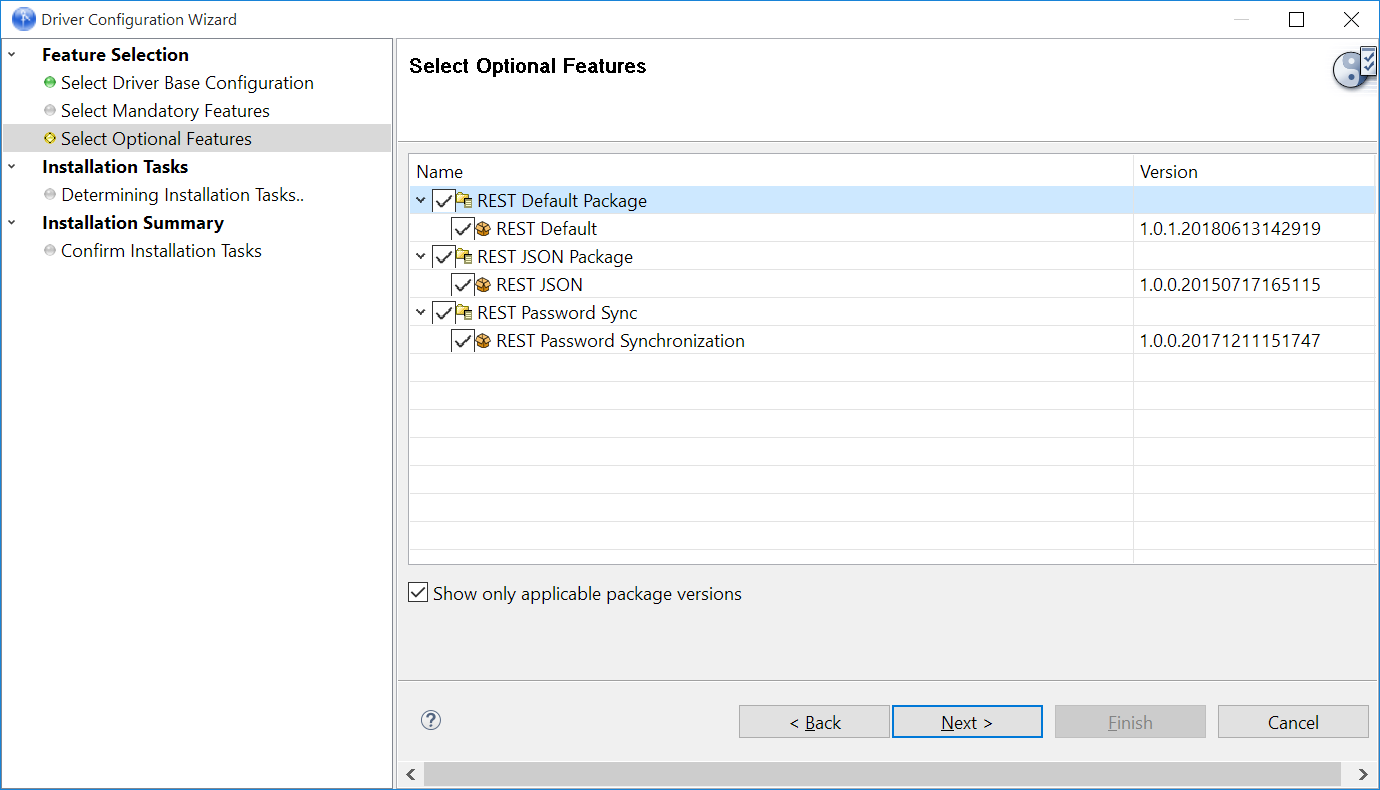
Select the optional features to install for the REST driver, the options are:
-
REST Default Package
-
REST JSON Package: This package contains the default JSON configurations
-
REST Password Sync: This packages contains the policies that enable the REST driver to synchronize passwords. If you want to synchronize passwords, verify that this option is selected. For more information, see the NetIQ Identity Manager Password Management Guide.
-
-
Click Next.
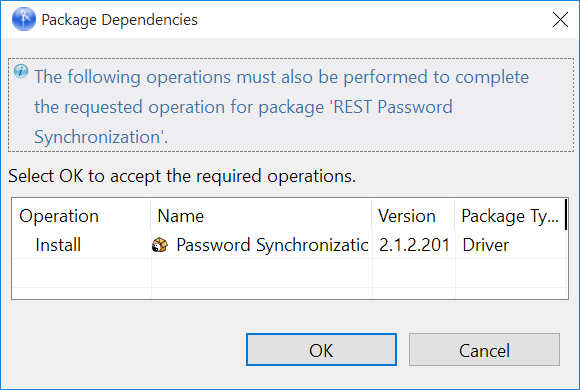
The package dependencies window appears.
-
(Conditional) Click OK to install the package dependency listed.
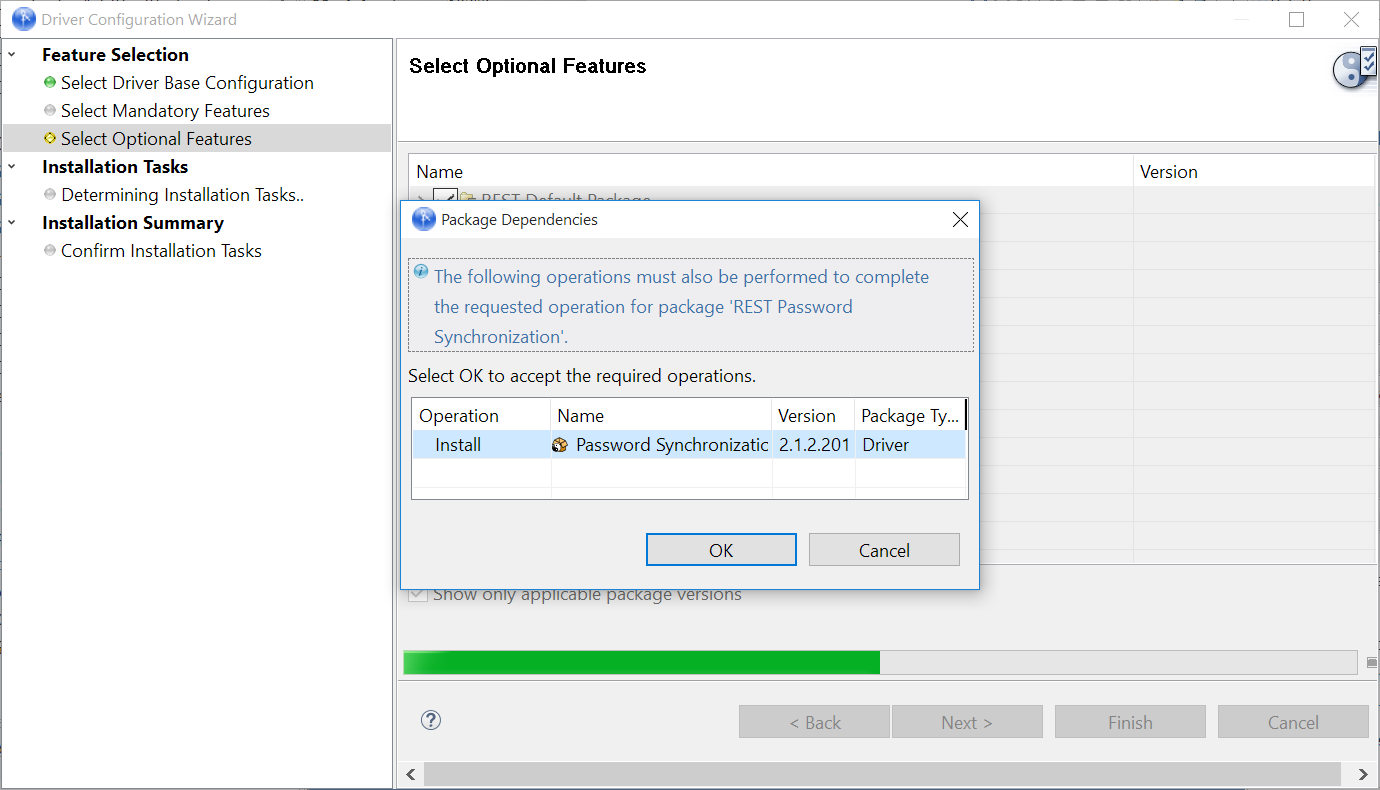
NOTE:If there are any dependent packages associated with the selected package, you must install them to proceed.
-
On the Driver Information page, specify a name for the driver, then click Next.
-
On the Install REST Base page, fill in the following fields for the Subscriber options, and click Next.
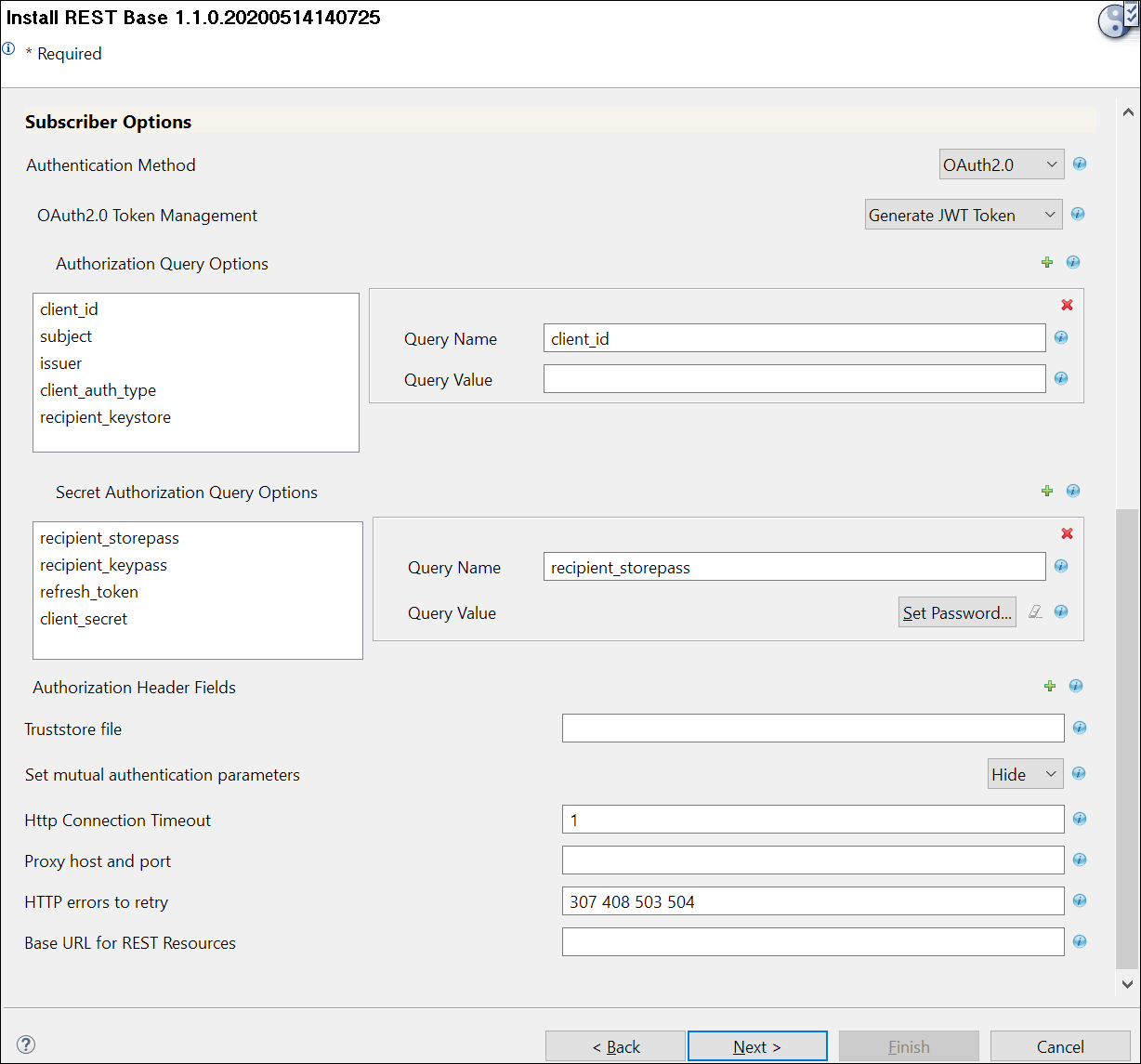
The Authentication Methods available are, Anonymous, Basic, and OAuth2.0, and the screen defaults to Basic. Based on the selection you make the other fields appear.
NOTE:Fields marked with ** indicate common fields that appear for all Authentication Methods.
-
If you select Basic, the following fields appear:
-
Authentication ID: Specify the authentication ID for Basic Authorization (on the HTTP header) is used.
-
Authentication Password: Specify the authentication password for Basic Authorization (on the HTTP header) is used.
-
Authorization Header Fields**: Click the
 icon to create authentication header fields. Enter the required authentication header fields and supported values for the selected authentication method.
icon to create authentication header fields. Enter the required authentication header fields and supported values for the selected authentication method. -
Truststore file**: Specify the path and the name of the keystore file that contains the trusted certificates for the remote server to provide server authentication. For example, C:\security\truststore. Leave this field blank when server authentication is not used.
-
Set mutual authentication parameters**: Select Show if you want to set mutual authentication information.
-
Keystore file: Specify the path and the name of the keystore file that contains the trusted certificates for the remote server to provide mutual authentication. For example, C:\security\keystore. Leave this field blank when mutual authentication is not used.
-
Keystore password: Specify the password for the keystore file. Leave this field blank when mutual authentication is not used.
-
-
Http Connection Timeout**: Specify the HTTP connection time out value. The driver waits for the time specified and terminates the HTTP connection. The timeout value must be greater than zero.
-
Proxy host and port**: Specify the host address and the host post when a proxy host and port are used. For example: 192.168.0.0:port. Choose an unused port number on your server. Otherwise, leave this field blank.
-
HTTP errors to retry**: Specify the HTTP errors that must return a retry status. Error codes must be a list of integers separated by spaces. For example, 307 408 503 504.
-
Base URL for REST**: Specify the URL of the REST server or Web service.
-
-
If you select OAuth2.0, the following fields appear:
-
OAuth 2.0 Token Management: Select the token type as required. The available options are, Generate Bearer Token, Generate JWT Token, Enter Bearer Token.
-
Generate Bearer Token: It is an access token issued by servers to achieve multi-server authentication.
If you select Generate Bearer Token, the following fields appear:
Field
Description
Access Token URL
Specify the URL of the server used for requesting token access.
User Name
<username to login to the connected application>
User Password
<password to login to connected application>
Authorization Query Options
-
grant_type: It is the method the application procures an access token.
Enter the value as password.
-
client_id: The client_id is a public identifier for the connected application.
Enter the <client identification value>.
For example: <3MVG97quAmFZJfVwk3ylU.8elhRYBqG9h25m3TWewozjKnFIY0HrhOEJl7LMET9HHocaHnTB1k04kophr1CgW>
-
issuer: The authorization server's URL that uses the https protocol.
Secret Authorization Query Options
NOTE:The * indicates mandatory fields and ^ indicates non mandatory fields.
These parameters are set to configure a refresh token. Though not mandatory, if configured the set refresh token value is not overridden with the new value when the access token expires. This may cause login issues until the new refresh token is added.
-
refresh_token^: Refresh Token is a web token to acquire new access tokens when current access tokens expire or become invalid. The authorization server of the connected system provides refresh tokens to the Identity Manager to obtain new access token, without user interaction in the backend.
-
client_secret^: It is a secret pass phrase associated with the refresh token.
-
-
Generate JWT Token: The JSON Web token is an access request token in the JSON Web Token (JWT) format. It is an encrypted data string consisting of a header, payload, and a signature, and is used to transfer authorization data in client-server applications to authenticate the resource identity.
If you select Generate JWT Token, the following fields appear:
Field
Description
Authorization Query Options
-
client_id
-
subject: The user’s unique identity for which the access token is being requested.
-
issuer
-
client_auth_type: The client's authorization types configured for granting access to the application.
-
recipient_keystore: The keystore recipient alias used to look up the digital signature which contains the public key in connected application.
Secret Authorization Query Options
-
recipient_storepass: Password for the recipient keystore.
-
recipient_keypass: Password for the recipient key value.
-
refresh_token^
-
client_secret^
-
-
Enter Bearer Token: Enter a bearer token if you already have one, and configure the refresh_token and client_secret and set the passwords accordingly.
If you select Enter Bearer Token, the following fields appear:
Field
Description
Bearer Token ID
Enter the available bearer token.
Authorization Query Options
-
client_id
-
issuer
Secret Authorization Query Options
-
refresh_token*: It is mandatory to configure for an available bearer token.
-
client_secret*
-
-
-
-
If you select Anonymous: only Authorization Header Fields, Truststore file, Set mutual authentication parameters, Http Connection Timeout, Proxy host and port, HTTP errors to retry, and Base URL for REST Resources fields appear.
-
-
On the Install REST Base page, for the Publisher Options fill in the following fields, then click Next.
Field
Description
Publisher Setting
Specify the publisher setting for the REST driver. Based on the selection the other fields appear. The available options are:
-
Poll
-
Publish
These fields appear if Publisher is selected.
Publisher Options:
-
Listening IP address and port: Specify the IP address of the server where this driver is installed and the port that this driver listens on. You can specify 127.0.0.1, if there is only one network card installed in the server. Choose an unused port number on your server. For example: 127.0.0.1:port. The driver listens on this address for incoming requests, processes the requests, and returns a result.
-
Authentication Method, Authentication ID and Authentication Password: Select the authentication values respectively for the REST driver. The authentication methods available are Anonymous and Basic. You need to specify additional parameters depending upon the selected authentication method.
For more information, see Driver Configuration.
Other options:
-
KMO name: When this server is configured to accept HTTPS connections, this is the KMO name in eDirectory. The KMO name is the name before the - in the RDN. Leave this field blank when a keystore file is issued or when HTTPS connections are not used.
-
Keystore file: When this server is configured to accept HTTPS connections, this is the path and the name of the keystore file. For example; C:\security\keystore. Leave this field blank when a KMO name is used or when HTTPS connections are not used.
-
Keystore password: When this server is configured to accept HTTPS connections, this is the keystore file password. Leave this field blank when a KMO name is used or when HTTPS connections are not used.
-
Server key alias: When this server is configured to accept HTTPS connections, this is the key alias. Leave this field blank when a KMO name is used or when HTTPS connections are not used.
-
Server key password: When this server is configured to accept HTTPS connections, this is the key alias password (not the keystore password). Leave this field blank when a KMO name is used or when HTTPS connections are not used.
-
Require Mutual authentication: When using SSL, it is common to do only server authentication. However, if you want to force both client and server to present certificates during the handshake process, select Required.
-
Heartbeat interval in minutes: Heartbeat is the interval to be specified for data synchronization between Identity Manager and the connected system. Leave this field blank to turn off the heartbeat.
These fields appear if Poll is selected.
Configure Resource for poll:
-
Schema name: Specify the class name of the user resource returned present in application schema.
-
Service Endpoints: Specify the REST URLs for the resource. Mention queryable strings as %s.
-
Method: Select the HTTP method to be used.
-
Polling interval in minutes: Specify the polling interval in minutes. Default is one minute.
-
-
(Conditional) Fill in the following fields for the Remote Loader information, then click Next.
To Connect To Remote Loader:
-
Select Yes or No to determine if the driver will use the Remote Loader.
-
If you select No, skip to Step 12.
-
If you select Yes, use the following information to complete the configuration of the Remote Loader:
Field
Description
Host Name
Specify the IP address or DNS name of the server where the Remote Loader is installed and running.
Port
Specify the port number for this driver. Each driver connects to the Remote Loader on a separate port. The default value is 8090.
KMO
Specify the key name of the Key Material Object that includes keys and certificates for SSL. You use this parameter only when an SSL connection exists between the Remote Loader and the Identity Manager engine.
NOTE:When this server is configured to accept HTTPS connections, this is the KMO name in eDirectory. The KMO name is the name before the - in the RDN. Leave this field blank when a keystore file is issued or when HTTPS connections are not used.
Other Parameters
Specify any other parameter required in the connection string. The parameter must be a key-value pair. For example, paraName1=paraValue1
Remote Loader Password
Specify a password to control access to the Remote Loader. It must be the same password that is specified as the Remote Loader password on the Remote Loader.
Driver Password
Specify a password for the driver to authenticate to the Identity Manager server. It must be the same password that is specified as the Driver Object Password on the Remote Loader.
-
-
Review the summary of tasks that will be completed to create the driver, then click Finish.
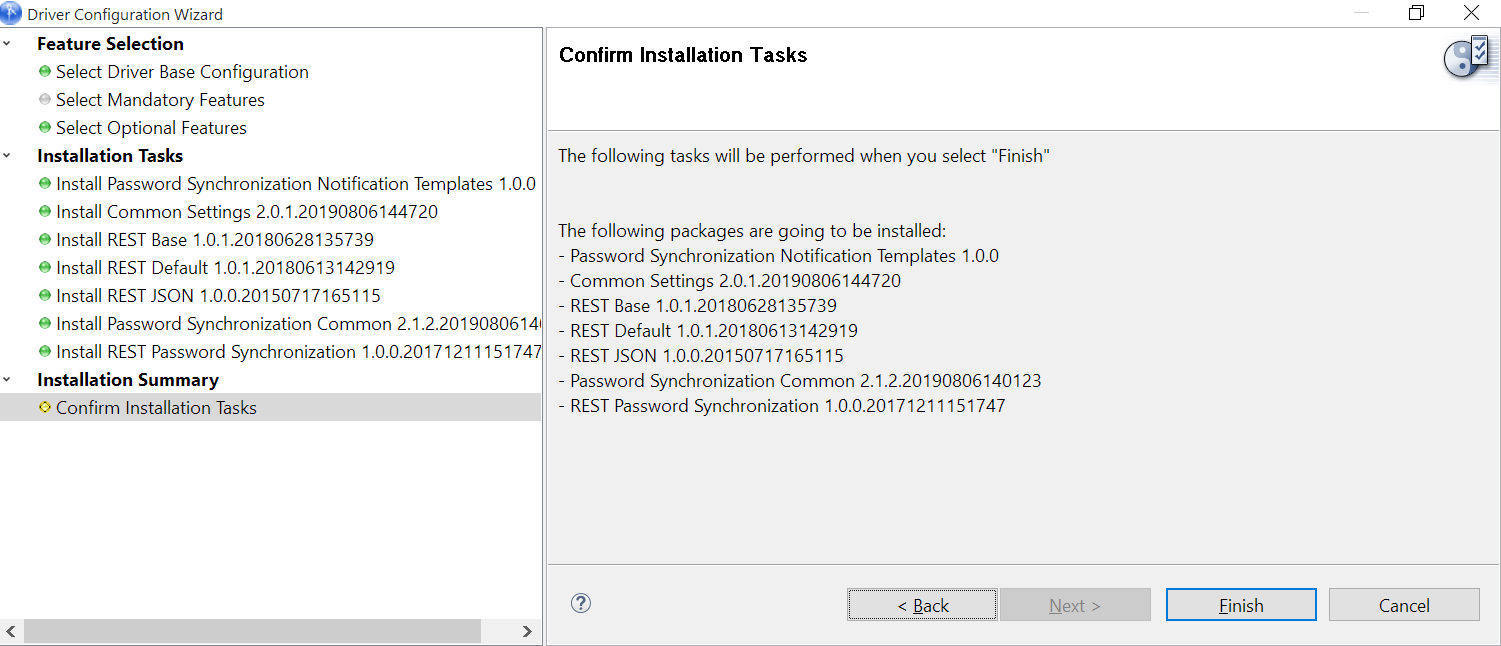
-
After you have installed the driver, you must change a few specific configurations based on your environment. Proceed to Configuring the Driver Object.
For more information, see:
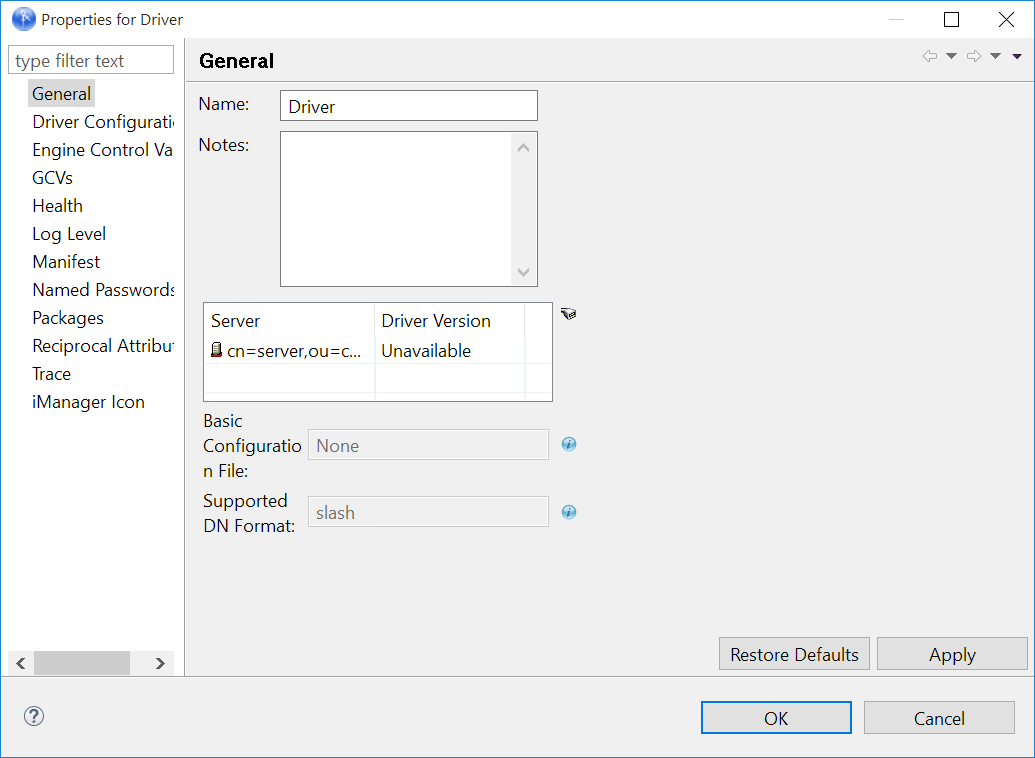
3.1.3 Configuring the Driver Object
After the driver packages are installed, you need to configure the driver before it can run. You should complete the following tasks to configure the driver:
-
Configure the driver parameters: There are many settings that can help you customize and optimize the driver. The settings are divided into categories such as Driver Configuration, Engine Control Values, and Global Configuration Values (GCVs). Although it is important for you to understand all of the settings, your first priority should be to review the Driver Parameters located on the Driver Configuration page. The Driver Parameters let you configure the publication method and other parameters associated with the Publisher channel.
-
Customize the driver policies and filter: The driver policies and filter control data flow between the Identity Vault and the application. You should ensure that the policies and filters reflect your business needs. For instructions, see Section 5.0, Customizing the Driver for RESTful Services.
-
Set Up a Secure HTTPS Connection: The connection between the driver and the RESTful connected system can be configured to use a secure HTTPS connection rather than an HTTP connection.
After completing the configuration tasks, continue withDeploying the Driver Object.
3.1.4 Deploying the Driver Object
After the driver object is created in Designer, it must be deployed into the Identity Vault.
-
In Designer, open your project.
-
In the Modeler, right-click the driver icon
 or the driver line, then select Live > Deploy.
or the driver line, then select Live > Deploy. -
If you are authenticated to the Identity Vault, skip to Step 4; otherwise, specify the following information, then click OK.
Field
Description
Host
Specify the IP address or DNS name of the server hosting the Identity Vault.
Username
Specify the DN of the user object used to authenticate to the Identity Vault.
Password
Specify the user’s password.
-
Read the deployment summary, then click Deploy.
-
Read the message, then click OK.
-
Click Define Security Equivalence to assign rights to the driver.
The driver requires rights to objects within the Identity Vault. The Admin user object is most often used to supply these rights. However, you might want to create a DriversUser (for example) and assign security equivalence to that user. Whatever rights that the driver needs to have on the server, the DriversUser object must have the same security rights.
-
Click Add, then browse to and select the object with the correct rights.
-
Click OK twice.
For more information about defining a Security Equivalent User in objects for drivers in the Identity Vault, see the NetIQ Identity Manager Security Guide
-
-
Click Exclude Administrative Roles to exclude users that should not be synchronized.
You should exclude any administrative User objects (for example, Admin and DriversUser) from synchronization.
-
Click Add, then browse to and select the user object you want to exclude, then click OK.
-
Repeat Step 7.a for each object you want to exclude, then click OK.
-
-
Click OK.
-
Continue with the next section,Starting the Driver.
3.1.5 Starting the Driver
When a driver is created, it is stopped by default. To make the driver work, you must start the driver. Identity Manager is an event-driven system, so after the driver is started, it won’t do anything until an event occurs. You can use iManager or dxevent commands to start the driver.
To start the driver using Designer:
-
In Designer, open your project.
-
In the Modeler, right-click the driver icon
 or the driver line, then select Live > Start Driver.
or the driver line, then select Live > Start Driver.
To start the driver using iManager:
-
Login to iManager,
-
Select Identity Manager Administration page, if not defaulted already.
-
Click Identity Manager Overview.
-
Browse to and select the driver set object that contains the driver you want to start.
-
Click the driver set name to access the Driver Set Overview page.
-
Click the upper right corner of the driver, then click Start driver.
IMPORTANT:When you start the driver for the first time, don't add new users to the Publisher channel until the first polling interval completes because the driver treats all users as existing users and stores them in the change cache without sending them to the Identity Manager engine. It sends the new users to the Identity Manager engine from the next polling interval. Therefore, ensure that new users are added to the Publisher channel after the first polling cycle completes.